A new phishing-as-a-service (PhaaS) platform named Rockstar 2FA has emerged, enabling adversary-in-the-middle (AiTM) attacks to bypass multifactor authentication (MFA) and steal Microsoft 365 credentials.
Attack Methodology
Like other AiTM platforms, Rockstar 2FA intercepts session cookies to bypass MFA protections. The attack involves:
- Directing victims to a fake Microsoft 365 login page.
- Tricking victims into entering their credentials.
- Acting as a proxy to forward credentials to Microsoft’s legitimate service, completing authentication.
- Capturing the session cookie returned to the victim’s browser, which attackers can use to access the account without needing the credentials.
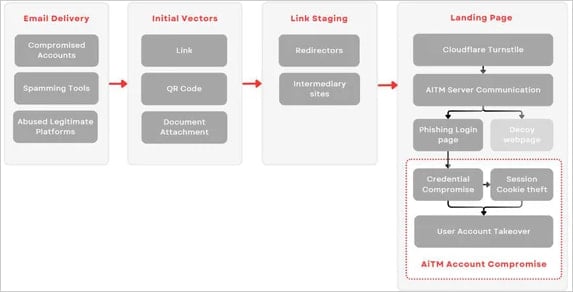 Rockstar 2FA’s attack flow
Rockstar 2FA’s attack flow
Source: Trustwave
The Rise of Rockstar 2FA
Trustwave reports that Rockstar 2FA evolved from earlier phishing kits like DadSec and Phoenix, gaining popularity in the cybercrime community since August 2024.
The service is marketed on platforms like Telegram, priced at $200 for two weeks or $180 for API access renewal.
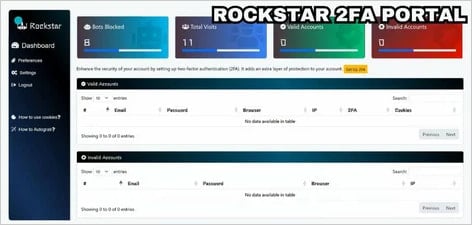 The Rockstar 2FA admin panel
The Rockstar 2FA admin panel
Source: Trustwave
Offensive Security, Bug Bounty Courses
Discover your weakest link. Be proactive, not reactive. Cybercriminals need just one flaw to strike.
Features and Capabilities
Rockstar 2FA boasts an extensive feature set:
- Support for Microsoft 365, Hotmail, GoDaddy, and SSO services.
- Randomized source code and links to evade detection.
- Cloudflare Turnstile Captcha to filter bots and screen victims.
- Automated FUD (Fully Undetectable) attachments and links.
- A user-friendly admin panel with real-time logs and backup options.
- Multiple login page themes with automatic organization branding (logo, background).
Since May 2024, the platform has established over 5,000 phishing domains, facilitating widespread phishing campaigns.
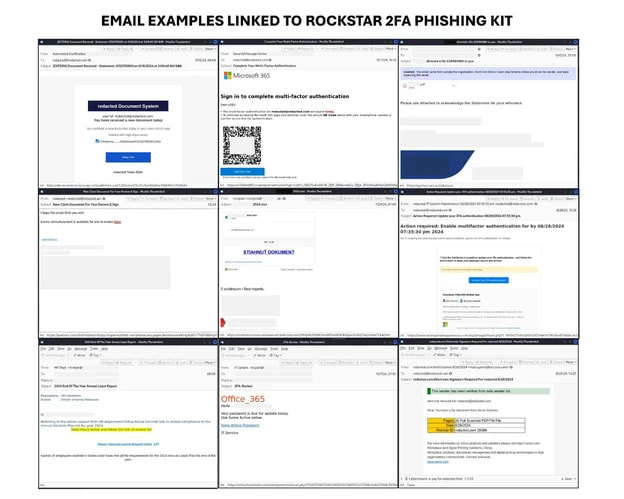 Phishing emails sent from Rockstar 2FA
Phishing emails sent from Rockstar 2FA
Source: Trustwave
Phishing Campaigns
Rockstar 2FA’s phishing campaigns leverage compromised accounts and legitimate email marketing platforms to distribute malicious emails. These emails often feature lures such as:
- Document-sharing notifications.
- IT department alerts.
- Password reset prompts.
- Payroll-related messages.
Evasion Tactics:
- QR codes and shortened URLs.
- PDF attachments embedding phishing links.
- Cloudflare Turnstile Captcha challenges to filter bots and security researchers.
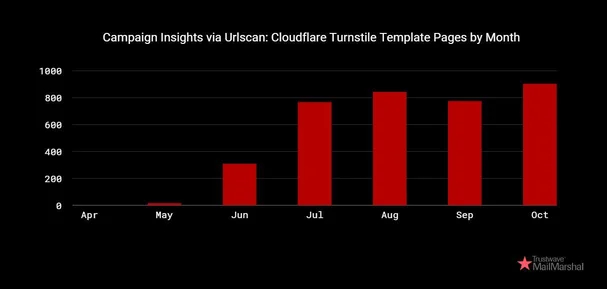 Volume of Cloudflare Turnstile challenge requests linked to Rockstar 2FA
Volume of Cloudflare Turnstile challenge requests linked to Rockstar 2FA
Source: Turstwave
When targets visit the phishing page, JavaScript evaluates their profile:
- Valid targets are directed to the phishing site.
- Non-targets, bots, or security researchers are redirected to a harmless, car-themed decoy page.
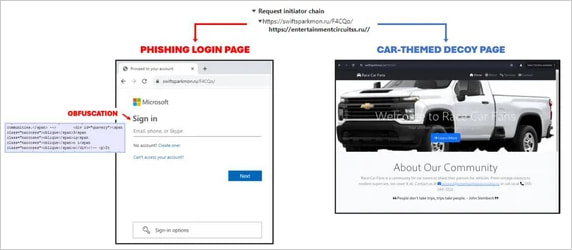 Redirecting to a phishing or a decoy page
Redirecting to a phishing or a decoy page
Source: Trustwave
Trending: Top 10 Things to Do After Installing Kali Linux
Trending: Blue Team Tool: Ghostport
Implications and Persistence
The emergence of Rockstar 2FA highlights the ongoing evolution of phishing techniques despite law enforcement crackdowns on major PhaaS operators.
As Trustwave notes, the accessibility and low cost of tools like Rockstar 2FA significantly raise the risk of large-scale phishing operations. Businesses and individuals are urged to remain vigilant and deploy robust anti-phishing and authentication measures to mitigate these threats.
Trending: New Ghost Tap Attack: The Next-Level Credit Card Scam Exploiting Apple Pay and Google Pay
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: info@blackhatethicalhacking.com