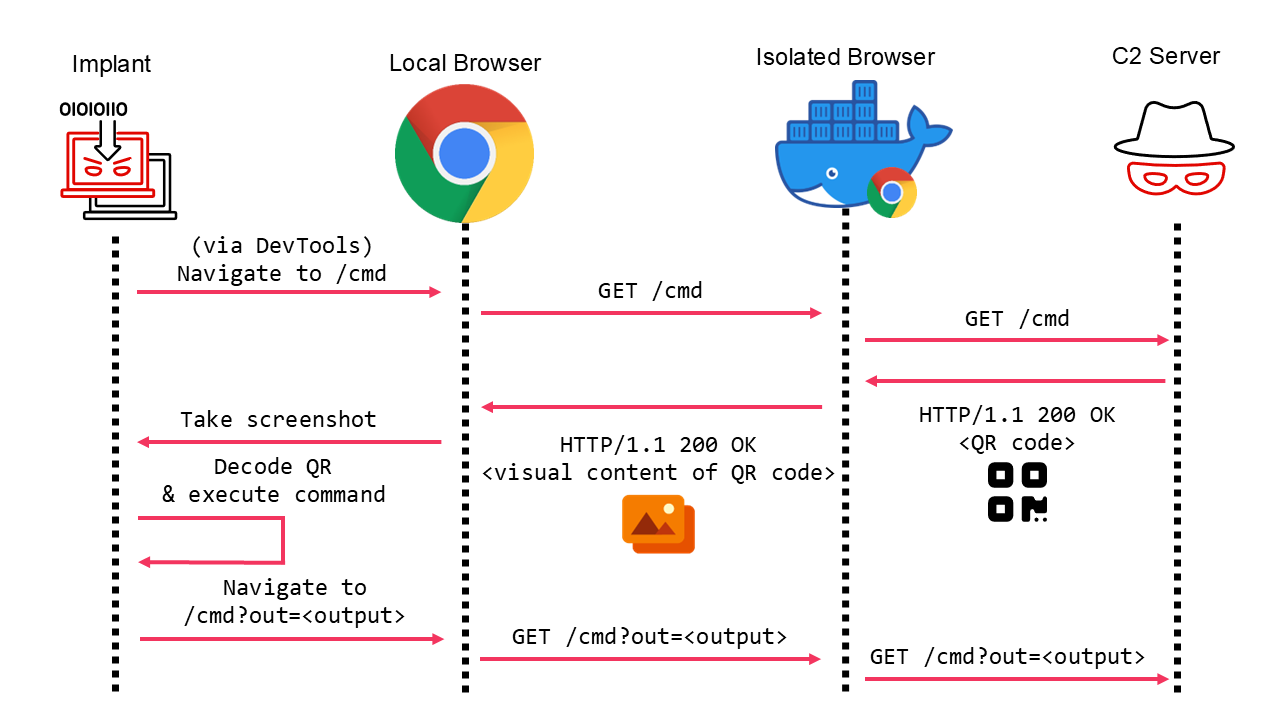
Threat actors are getting smarter. The days of blocklisting or threat hunting for IP addresses and domains you find in cyber threat intelligence reports are gone. You must get ahead of the bad guys and start performing C2 hunting.
A Command and Control (C2) server is an attacker’s lifeline. It allows them to control systems they have compromised, upload hacking tools, and exfiltrate sensitive data.
Wouldn’t it be great if you could hunt down this essential network infrastructure?
Well, let me introduce you to C2 hunting. A powerful threat hunting technique that allows you to stay one step ahead of the bad guys with publicly available information and investigative rigor.
Let’s dive in!
The complete version of this article can be viewed for free on: https://kravensecurity.com/c2-hunting-using-shodan/
What is C2 Hunting?
A cyber attack typically happens in stages (a cyber kill chain). The attacker will perform reconnaissance to find security gaps, exploit them to gain initial access, and then pillage systems to achieve their objectives.
One of the key stages of a cyber attack is the Command and Control (C2) stage.