Microsoft Expands Access to Windows Recall AI Feature

NEWS BRIEF Microsoft has expanded access for its Windows Recall feature to Copilot+ PCs that use AMD and Intel chipsets, after initially offering it to users with Snapdragon-powered machines. And, it has now launched in Europe. The launch is part of a gradual rollout that for now is in a preview phase within the Windows […]
Misconfigured WAFs Heighten DoS, Breach Risks

Many organizations using Web application firewall (WAF) services from content delivery network (CDN) providers may be inadvertently leaving their back-end servers open to direct attacks over the Internet because of a common configuration error. The problem is so pervasive that it affects nearly 40% of Fortune 100 companies leveraging their CDN providers for WAF services, […]
Diese Unternehmen hat’s schon erwischt

Ransomware, Brute Force, DDoS und Co: Diese deutschen Unternehmen wurden in diesem Jahr bereits von Cyberkriminellen attackiert. Sie denken, Ihre Sicherheitsmaßnahmen können Sie langfristig vor Cyberangriffen schützen? Oder dass Ihr Unternehmen zu klein und damit uninteressant für Hacker ist? Egal, ob Sie dem Mittelstand angehören, an der Börse gelistet sind oder zu den kritischen Infrastrukturen […]
Bundesländer beschließen Porno-Filter für Betriebssysteme

Die Regierungschefs der Länder haben am Donnerstag bei der Ministerpräsidentenkonferenz in Berlin eine erneute Reform des Jugendmedienschutz-Staatsvertrags (JMStV) beschlossen. Damit sollen Pornofilter schon auf der elementaren Ebene von PCs, Laptops und Smartphones installiert und eine Alterskennzeichnung für Webseiten und Apps eingeführt werden. Laut dem überarbeiteten Paragraf 12 müssen Anbieter von Betriebssystemen künftig sicherstellen, dass diese […]
Russian cyberspies target Android users with new spyware

Russian cyberspies Gamaredon has been discovered using two Android spyware families named ‚BoneSpy‘ and ‚PlainGnome‘ to spy on and steal data from mobile devices. According to Lookout, which discovered the two malware families, BoneSpy has been active since 2021, while PlainGnome emerged in 2024. Both target Russian-speaking individuals in former Soviet states. Gamaredon (aka „Shuckworm“) […]
Iran-linked IOCONTROL malware targets critical IoT/OT infrastructure in Israel, US
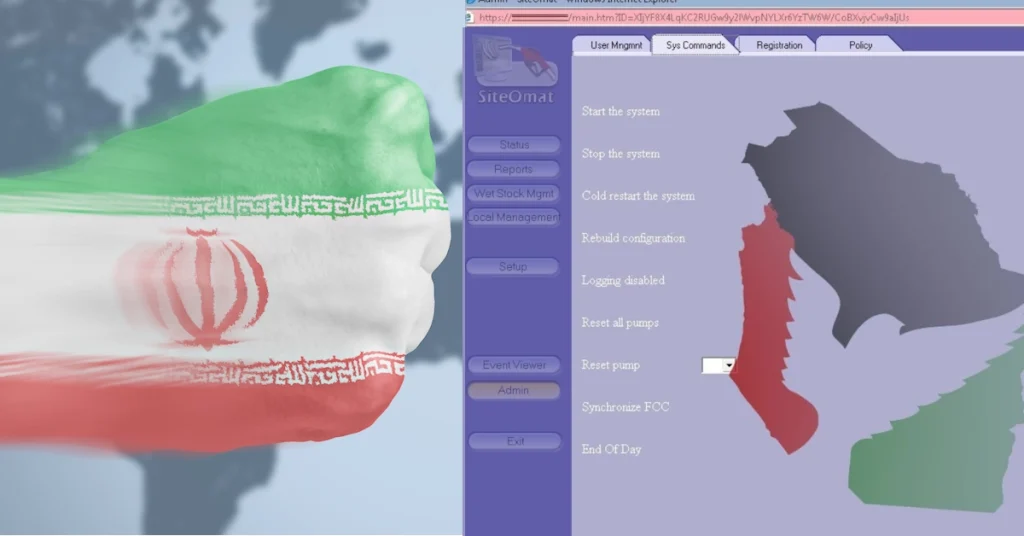
Researchers from Claroty’s Team82 arm have obtained a sample of a custom-built IoT/OT malware called IOCONTROL used by the Iran-affiliated attackers to attack Israel- and U.S.-based OT/IoT devices. IOCONTROL has been used to attack IoT and SCADA/OT (supervisory control and data acquisition/operational technology) devices of various types including IP cameras, routers, PLCs (programmable logic controllers), HMIs (human-machine interfaces), […]
390,000+ WordPress Credentials Stolen via Malicious GitHub Repository Hosting PoC Exploits

A now-removed GitHub repository that advertised a WordPress tool to publish posts to the online content management system (CMS) is estimated to have enabled the exfiltration of over 390,000 credentials. The malicious activity is part of a broader attack campaign undertaken by a threat actor, dubbed MUT-1244 (where MUT refers to „mysterious unattributed threat“) by […]
‚Dubai Police‘ Lures Anchor Wave of UAE Mobile Attacks

The Dubai Police are the latest victims of impersonation by fraudsters in the United Arab Emirates (UAE), who are sending thousands of text messages out to unwitting mobile users while purporting to represent the law enforcement agency. Researchers at BforeAI observed a recent surge in phishing attacks leveraging alleged police communications, which encourage text recipients […]
Crypted Hearts: Exposing the HeartCrypt Packer-as-a-Service Operation

Executive Summary This article analyzes a new packer-as-a-service (PaaS) called HeartCrypt, which is used to protect malware. It has been in development since July 2023 and began sales in February 2024. We have identified examples of malware samples created by this service based on strings found in several development samples the operators used to test their […]
Cleo MFT Zero-Day Exploits Are About to Escalate, Analysts Warn

An active ransomware campaign against the Cleo managed file transfer tool is about to ramp up now that a proof-of-concept exploit for a zero-day flaw in the software has become publicly available. Defenders should brace for widespread deployment of the Cleopatra backdoor and other steps in the attack chain. The flaw, which is the result […]