Microsoft NTLM Zero-Day to Remain Unpatched Until April

Microsoft has released fresh guidance to organizations on how to mitigate NTLM relay attacks by default, days after researchers reported finding a NTLM hash disclosure zero-day in all versions of Windows Workstation and Server, from Windows 7 to current Windows 11 versions. However, it was not immediately clear if the two developments are related or […]
Citrix shares mitigations for ongoing Netscaler password spray attacks

Citrix Netscaler is the latest target in widespread password spray attacks targeting edge networking devices and cloud platforms this year to breach corporate networks. In March, Cisco reported that threat actors were conducting password spray attacks on the Cisco VPN devices. In some cases, these attacks caused a denial-of-service state, allowing the company to find […]
Russian cyberspies target Android users with new spyware

Russian cyberspies Gamaredon has been discovered using two Android spyware families named ‚BoneSpy‘ and ‚PlainGnome‘ to spy on and steal data from mobile devices. According to Lookout, which discovered the two malware families, BoneSpy has been active since 2021, while PlainGnome emerged in 2024. Both target Russian-speaking individuals in former Soviet states. Gamaredon (aka „Shuckworm“) […]
U.S. CISA adds Cleo Harmony, VLTrader, and LexiCom flaw to its Known Exploited Vulnerabilities catalog

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added the vulnerability CVE-2024-50623 (CVSS score 8.8), which impacts multiple Cleo products to its Known Exploited Vulnerabilities (KEV) catalog. “Cleo has identified an unrestricted file upload and download vulnerability (CVE-2024-50623) that could lead to remote code execution.” reads the advisory. “Cleo strongly advises all customers to immediately upgrade instances of Harmony, VLTrader, and LexiCom […]
SAP systems increasingly targeted by cyber attackers

Long viewed as an opaque black box, attackers are increasingly focused upon hacking into enterprise systems from SAP, according to research presented at Black Hat Europe 2024. A review of four years of threat intelligence data, presented Friday at Black Hat by Yvan Genuer, a senior security researcher at Onapsis, reports a spike in hacker interest […]
390,000 WordPress accounts stolen from hackers in supply chain attack

A threat actor tracked as MUT-1244 has stolen over 390,000 WordPress credentials in a large-scale, year-long campaign targeting other threat actors using a trojanized WordPress credentials checker. Researchers at Datadog Security Labs, who spotted the attacks, say that SSH private keys and AWS access keys were also stolen from the compromised systems of hundreds of […]
Kritischer Fehler in allen Notes/Domino-Servern verhindert Mail-Routing

Von Volker Weber Anzeige Das Support-Dokument von HCL gibt sich sehr schmallippig. Es warnt davor, Server zu rebooten und teilt mit, dass HCL an einer Lösung arbeitet, ohne aktuell eine anbieten zu können. Das Dokument warnt auch davor, das Datum zurückzustellen. Es gibt bisher keine Hinweise, was diesen Fehler verursacht. Server, die nicht neu gestartet wurden, laufen […]
Lynx Ransomware Breach Targets Romania’s Electrica Group

The Romanian National Cybersecurity Directorate (DNSC) has confirmed that the Lynx ransomware gang successfully breached Electrica Group, a leading electricity supplier in Romania. About Electrica Group Electrica Group, initially part of the National Electricity Company (CONEL) in 1998, became an independent entity in 2000. Since 2014, it has been publicly traded on the London and Bucharest […]
Google’s Quantum Computing Leap: Introducing the “Willow” Chip
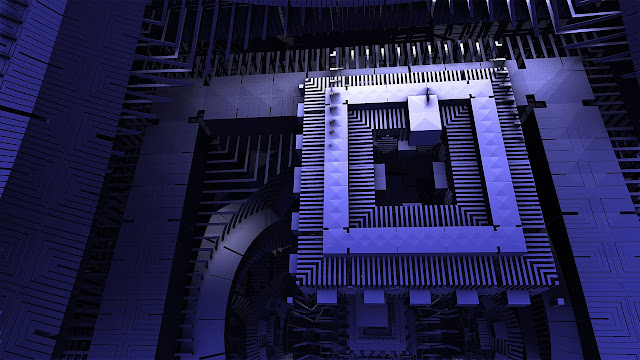
Google has made a significant stride in quantum computing with the announcement of its latest chip, named “Willow.” According to Google, this advanced chip can solve problems in just five minutes that would take the most powerful supercomputers on Earth an astonishing 10 septillion years to complete. This breakthrough underscores the immense potential of quantum computing, a […]
The Top Ten List of Why You Got Hacked This Year (2023/2024)

tl;dr: BHIS does a lot of penetration testing in both traditional and continuous penetration testing (CPT) formats. This top ten style list was derived from an analysis of our findings across our penetration testing services. Anywho… This list is based on the last couple years of analyzing our report findings, mostly the findings that lead […]