Identify your IT vulnerabilities
with just one click
- No Prior Knowledge
- No Installation required

Gain instant visibility into your external risk surface—no technical skills needed.
4.8 / 5 Basierend auf 4.109 Bewertungen | DSGVO konform
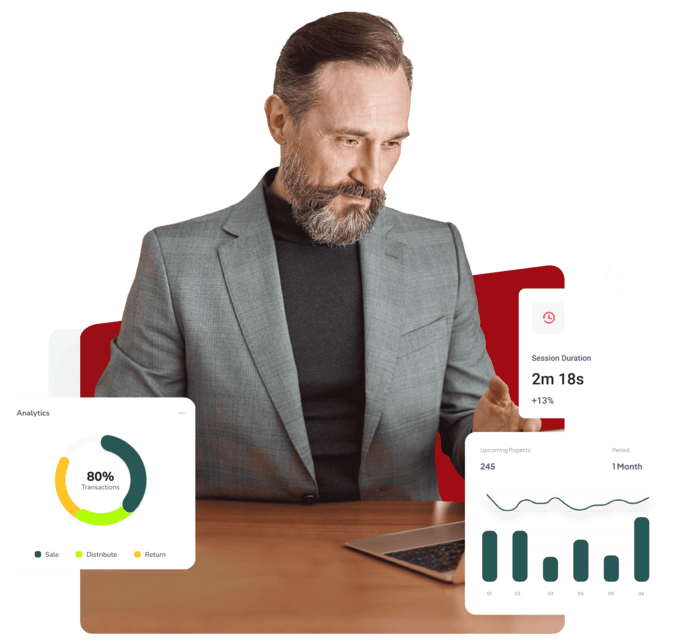







One click. Complete visibility.
- Companies / Investors
- Credit Protection Associations
- Insurance Companies
- Auditors
- Reseller
Know the risks.
Avoid costs.
We help identify critical IT vulnerabilities and provide smart, budget-conscious fixes—so you can stay focused on growth, not security gaps.
See your system from a hacker’s viewpoint

Zero system impact, no service delay

Instant steps to reduce exposure fast

Support for due diligence, on demand



Monitor risks.
Obtain industry index.
Credit protection helps manage financial risk—so why not cybersecurity?
Gain insight into their partners’ digital vulnerabilities. In a world of AI-powered phishing, ransomware, and darknet activity, understanding external cyber risk is essential for proactive protection.
Fully Automated Interface with Complete Documentation

Round-the-Clock Service. Data at Your Fingertips.

Dedicated Support • White-Label On Request




Making IT Risks Measurable.
To assess the likelihood and potential impact of risks, we provide aggregated benchmark data for calculations, along with recurring real-time analyses of your own datasets—accessible through a seamless interface.
Insights from Over 28 Million Companies Across the EU

Integration with Insurance Systems

One-Time Assessments or Continuous Monitoring

Complete Historical Data Across All Sets

Real-Time Alerts for New Vulnerabilities




Comprehensive Analysis.
Expert Recommendations.
From quick plausibility checks to in-depth scans and thorough penetration tests—we only need your domain or email. All results are delivered on a single platform, with recurring assessments as needed to maintain top-tier security
Fully White-Labeled, Client-Branded Reports

One-Time or Scheduled Security Testing

Company-Specific Historical & Statistical Insights

Real-Time Alerts for Emerging Vulnerabilities




Reliable partnership.
Solid growth.
The added value for customers is the added value in sales, and we create this together with resellers around the world in order to offer customers more security every day.
Individual analyses or

Ongoing, real-time monitoring of all customers

Professional sales documents

Attractive conditions and tiered prices




Intelligent Cybersecurity
Check for vulnerabilities now
- No Credentials
- Darknet Monitoring
- Domain Monitoring
- Server Monitoring
Affordable pricing

save 25%
Start
€ 130
€ 99
Per Month
- 1 Company
- 100 Assets
- quarterly scan interval
- Darknet Monitoring
- Domain Monitoring
- Server Monitoring
Most popular
Business
€ 649
€ 495
Per Month
- 3 Companies
- 1000 Assets
- monthly scan interval
- Darknet Monitoring
- Domain Monitoring
- Server Monitoring
Premium
€ 2550
€ 1950
Per Month
- 10 Companies
- 5000 Assets
- monthly scan interval
- Darknet Monitoring
- Domain Monitoring
- Server Monitoring
Enterprise

€ 8500
€ 6500
Per Month
- 10 Companies
- 5000 Assets
- monthly scan interval
- Darknet Monitoring
- Domain Monitoring
- Server Monitoring
Start
€ 115
€ 75
Per Month
- 1 Company
- 100 Assets
- quarterly scan interval
- Darknet Monitoring
- Domain Monitoring
- Server Monitoring
Most popular
Business
€ 599
€ 399
Per Month
- 3 Companies
- 1000 Assets
- monthly scan interval
- Darknet Monitoring
- Domain Monitoring
- Server Monitoring
Premium
€ 2200
€ 1450
Per Month
- 10 Companies
- 5000 Assets
- monthly scan interval
- Darknet Monitoring
- Domain Monitoring
- Server Monitoring
Enterprise

€ 7500
€ 5500
Per Month
- 10 Companies
- 5000 Assets
- monthly scan interval
- Darknet Monitoring
- Domain Monitoring
- Server Monitoring
Let’s schedule your personalized offer
Get expert advice now
CEO statement and company vision
IT-Security can be
automated
In today’s fast-paced work environment, IT departments—whether internal or outsourced—are often overwhelmed, acting as a digital fire brigade focused on keeping systems operational and resolving critical issues. As a result, proactive services like cybersecurity are frequently overlooked because everything “just works”—until it doesn’t. This gap leads to the rise of Shadow IT, where employees try to solve their own problems, inadvertently exposing the organization to security risks. They reuse passwords across systems, sometimes even ones compromised in data breaches, putting sensitive company data at risk.
We created Risk Monitor as a practical, affordable solution to support IT professionals. It helps identify vulnerabilities efficiently, raise awareness among users, and strengthen overall organizational security without requiring extensive technical knowledge or large budgets.
Testimonials

Optimal tool for
critical infrastructure.
The analysis also showed us our attack.
vectors on the dark web and through our suppliers. Incredibly detailed.
WERNER LEHNER
CIO, UDB

Very useful as a
reseller for our customers.
We show customers weak points in the Darknet and monitor all domains and public servers. A lot of work has been done for us, and the benefits are enormous.
CHRISTIAN DICK
CEO, bit-Studio
Probably the most promising
startup I have ever heard of.
The market benefit of this cybersecurity SaaS solution is enormous.
FLORIAN HAAS
MARKETS BOARD MEMBER, EY

Advanced pentesting to
strengthen your IT security
Our system uncovers all vulnerabilities hackers target—whether data breaches, insecure servers, weak passwords, or domain phishing—helping you stay one step ahead.

No prerequisites or technical expertise required

No need for installation, migration or implementation.

With just one click, we analyze everything—even what unauthorized users could discover.
FAQ
We provide an intuitive solution that allows businesses monitor publicly exposed vulnerabilities and attack vectors—no technical expertise required. Proactively assess and mitigate security risks across your company’s IT systems with ease.
We enable automated IT security by continuously tracking vulnerabilities, providing clear insights, and alerting you to potential threats. This empowers IT teams to quickly identify and resolve weaknesses before they escalate.
Designed for everyone, no technical background needed. Our platform delivers clear, straightforward insights on vulnerabilities and security risks—so anyone in your organization can take effective action.
We track a wide range of security risks, including attack vectors, data breaches, exposed passwords, shadow IT risk, and other vulnerabilities that unauthorized users or hackers could potentially exploit.
We continuously scan for leaked credentials, exposed passwords, and any security incidents that could lead to a data breach. It helps businesses stay aware of any compromised information and ensures prompt action is taken to secure accounts.
Absolutely! We’re a practical and valuable partner for businesses of all sizes. Our simple, automated approach makes us an ideal choice for small businesses without dedicated security teams or deep technical resources.











