Bitdefender has released a decryptor for the ‘ShrinkLocker’ ransomware strain, which uses Windows’ built-in BitLocker drive encryption tool to lock victim’s files.
Discovered in May 2024 by researchers at cybersecurity company Kaspersky, ShrinkLocker lacks the sophistication of other ransomware families but integrates features that can maximize the damage of an attack.
According to Bitdefender’s analysis, the malware appears to have been repurposed from benign ten-year-old code, using VBScript, and leverages generally outdated techniques.
The researchers note that ShrinkLocker’s operators seem to be low-skilled, using redundant code and typos, leaving behind reconnaissance logs in the form of text files, and rely on readily available tools.
However, the threat actor has had successful attacks on corporate targets.
In a report today, Bitdefender highlights a ShrinkLocker attack against a healthcare organization where attackers encrypted Windows 10, Windows 11, and Windows Server devices across the network, including backups.
The encryption process finished in 2.5 hours and the organization lost access to critical systems, potentially facing difficulties in providing patient care.
Bitdefender is releasing a free decryption tool that can help ShrinkLocker victims recover their files.
ShrinkLocker attacks
Instead of using custom encryption implementations like traditional ransomware, ShrinkLocker uses Windows BitLocker with a randomly generated password that is sent to the attacker.
The malware first runs a Windows Management Instrumentation (WMI) query to checks if BitLocker is available on the target system, and installs the tool if not present.
Next, it removes all default protections that keep the drive from being encrypted by accident. For speed, it uses the ‘-UsedSpaceOnly’ flag to have BitLocker only encrypt occupied space on the disk.
The random password is generated using network traffic and memory usage data, so there are no patterns to make brute-forcing feasible.
The ShrinkLocker script will also delete and reconfigure all BitLocker protectors, to make more difficult the recovery of the encryption keys.
“Protectors are mechanisms used by BitLocker to protect the encryption key. They can include hardware protectors like TPMs or software protectors like passwords or recovery keys. By deleting all protectors, the script aims to make it impossible for the victim to recover their data or decrypt the drive,” Bitdefender explains.
For propagation, ShrinkLocker uses Group Policy Objects (GPOs) and scheduled tasks, modifies Group Policy settings on Active Directory domain controllers, and creates tasks for all domain-joined machines to ensure the encryption of all drives on the compromised network.
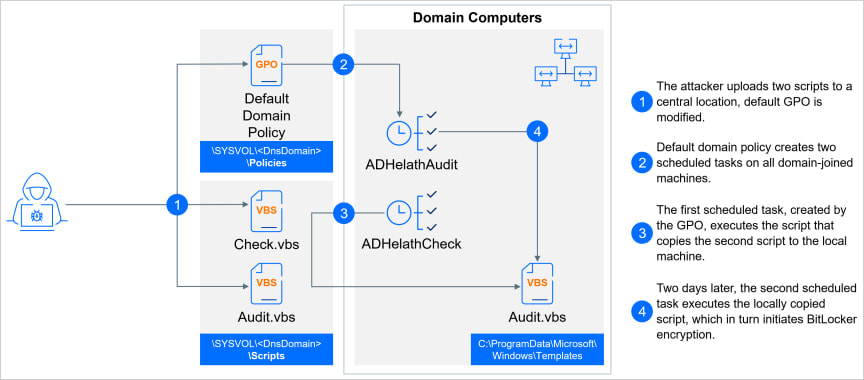
Source: Bitdefender
After reboot, victims see a BitLocker password screen that also includes the threat actor’s contact details.
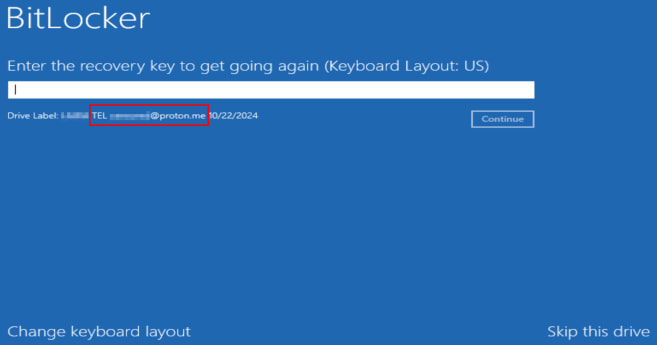
Source: Bitdefender
Bitdefender releases decryptor
Bitdefender created and released a decryptor that reverses the sequence in which ShrinkLocker deletes and reconfigures BitLocker’s protectors.
The researchers say that they identified “a specific window of opportunity for data recovery immediately after the removal of protectors from BitLocker-encrypted disks,” which allows them to decrypt and recover the password set by the attacker.
This makes it possible to reverse the encryption process and bring the drives back to their previous, unencrypted state.
ShrinkLocker victims can download the tool and use it from a USB drive connected to the impacted systems. When the BitLocker recovery screen shows, users should enter BitLocker Recovery Mode and skip all the steps to get to Advanced options, which provides a command prompt that allows launching the decryption tool.
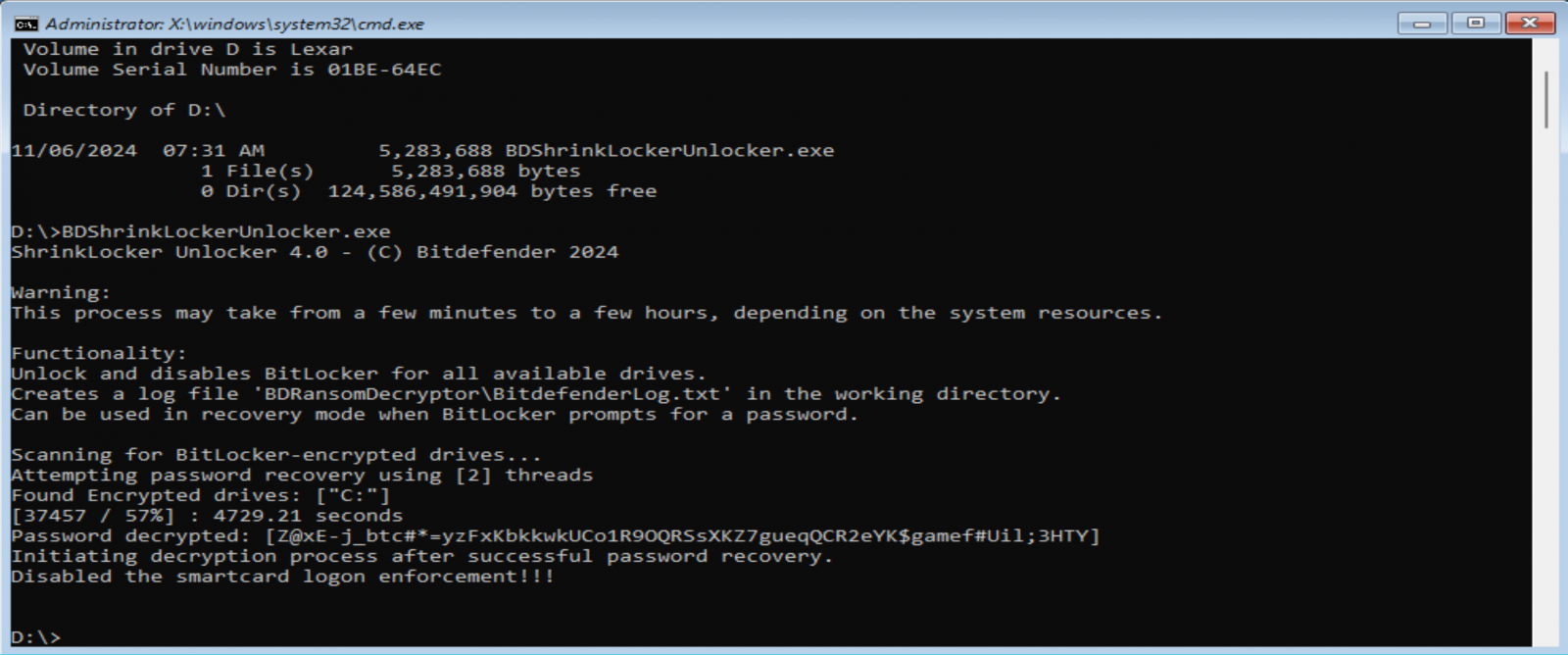
Source: Bitdefender
The researchers warn that the time to decrypt the data depends on the system’s hardware and the complexity of the encryption and could take some time.
When done, the decryptor will unlock the drive and disable smart card-based authentication.
Bitdefender notes that the decryptor only works on Windows 10, Windows 11, and recent Windows Server versions and is most effective when used shortly after the ransomware attack, when BitLocker’s configurations are not fully overridden yet and can be recovered.
Unfortunately, this method will not work to recover BitLocker passwords created using other methods.



