A new malicious package called ‘SteelFox’ mines for cryptocurrency and steals credit card data by using the “bring your own vulnerable driver” technique to get SYSTEM privileges on Windows machines.
The malware bundle dropper is distributed through forums and torrent trackers as a crack tool that activates legitimate versions of various software like Foxit PDF Editor, JetBrains and AutoCAD.
Using a vulnerable driver for privilege escalation is common for state-sponsored threat actors and ransomware groups. However, the technique now appears to extend to info-stealing malware attacks.
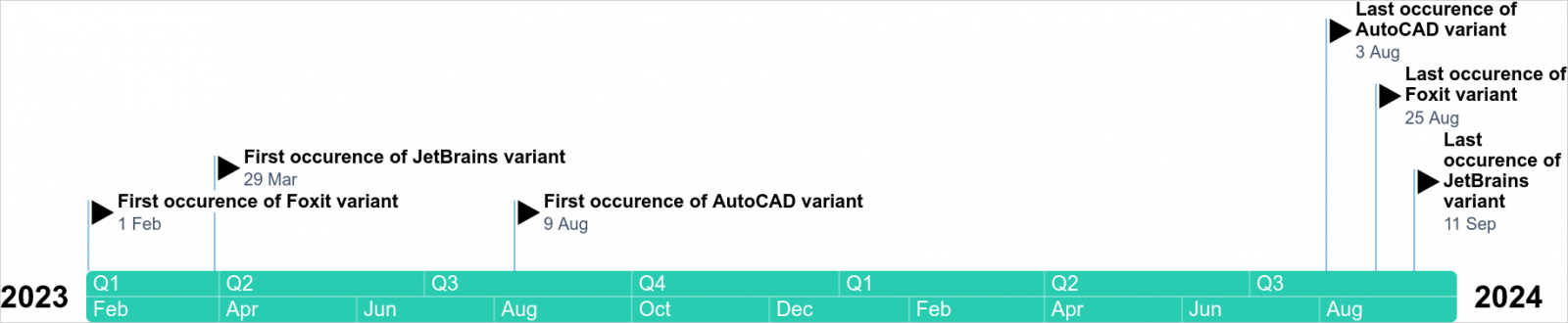
Kaspersky researchers discovered the SteelFox campaign in August but say that the malware has been around since February 2023 and increased distribution lately using multiple channels (e.g. torrents, blogs, and posts on forums).
According to the company, its products detected and blocked SteelFox attacks 11,000 times.
Source: Kaspersky
SteelFox infection and privilege escalation
Kaspersky reports that malicious posts promoting the SteelFox malware dropper come with complete instructions on how to illegally activate the software. Below is a sample of such a post providing directions on how to activate JetBrains:
.jpg)
Source: Kaspersky
The researchers say that while the dropper does have the advertised functionality, users also infect their systems with malware.
Since the software targeted for illegal activation is typically installed in the Program Files, adding the crack requires administrator access, a permission that the malware uses later in the attack.
Kaspersky researchers say that “the execution chain looks legitimate until the moment the files are unpacked.” They explain that a malicious function is added during the process, which drops on the machine code that loads SteelFox.
Having secured admin rights, SteelFox creates a service that runs WinRing0.sys inside, a driver vulnerable to CVE-2020-14979 and CVE-2021-41285, which can be exploited to obtain privilege escalation to NT/SYSTEM level.
Such permissions are the highest on a local system, more powerful than an administrator’s, and allow unrestricted access to any resource and process.
The WinRing0.sys driver is also used for cryptocurrency mining, as it is part of the XMRig program for mining Monero cryptocurrency. Kaspersky researchers say that the threat actor uses a modified version of the miner executable that connects to a mining pool with hardcoded credentials.
The malware then establishes a connection with its command-and-control (C2) server using SSL pinning and TLS v1.3, which protects the communication from being intercepted.
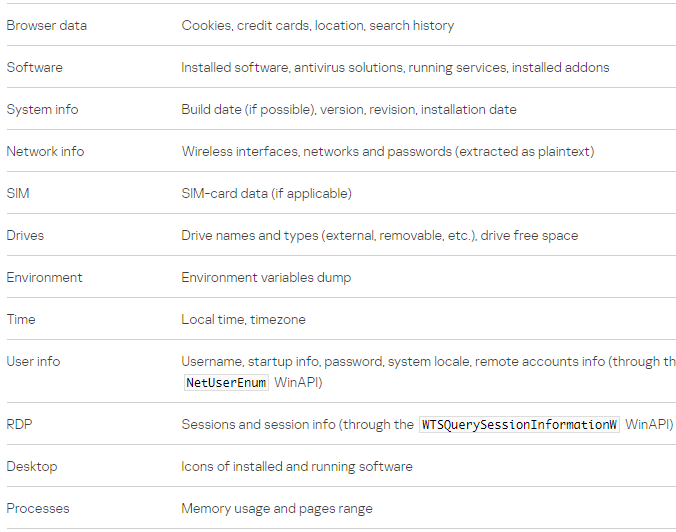
It also activates the info-stealer component that extracts data from 13 web browsers, information about the system, network, and RDP connection.
Source: Kaspersky
The researchers note that SteelFox collects from the browsers data like credit cards, browsing history, and cookies.
Kaspersky says that although the C2 domain SteelFox uses is hardcoded, the threat actor manages to hide it by switching its IP addresses and resolving them through Google Public DNS and DNS over HTTPS (DoH).
SteelFox attacks do not have specific targets but appear to focus on users of AutoCAD, JetBrains, and Foxit PDF Editor. Based on Kaspersky’s visibility, the malware compromises systems in Brazil, China, Russia, Mexico, UAE, Egypt, Algeria, Vietnam, India, and Sri Lanka.
Although SteelFox is fairly new, “it is a full-featured crimeware bundle,” the researchers say. Analysis of the malware indicates that it’s developer is skilled in C++ programming and they managed to create formidable malware by integrating external libraries.



