The Iranian state-sponsored hacking group APT34, aka OilRig, has recently escalated its activities with new campaigns targeting government and critical infrastructure entities in the United Arab Emirates and the Gulf region.
In these attacks, spotted by Trend Micro researchers, OilRig deployed a novel backdoor, targeting Microsoft Exchange servers to steal credentials, and also exploited the Windows CVE-2024-30088 flaw to elevate their privileges on compromised devices.
Apart from the activity, Trend Micro has also made a connection between OilRig and FOX Kitten, another Iran-based APT group involved in ransomware attacks.
Latest OilRig attack chain
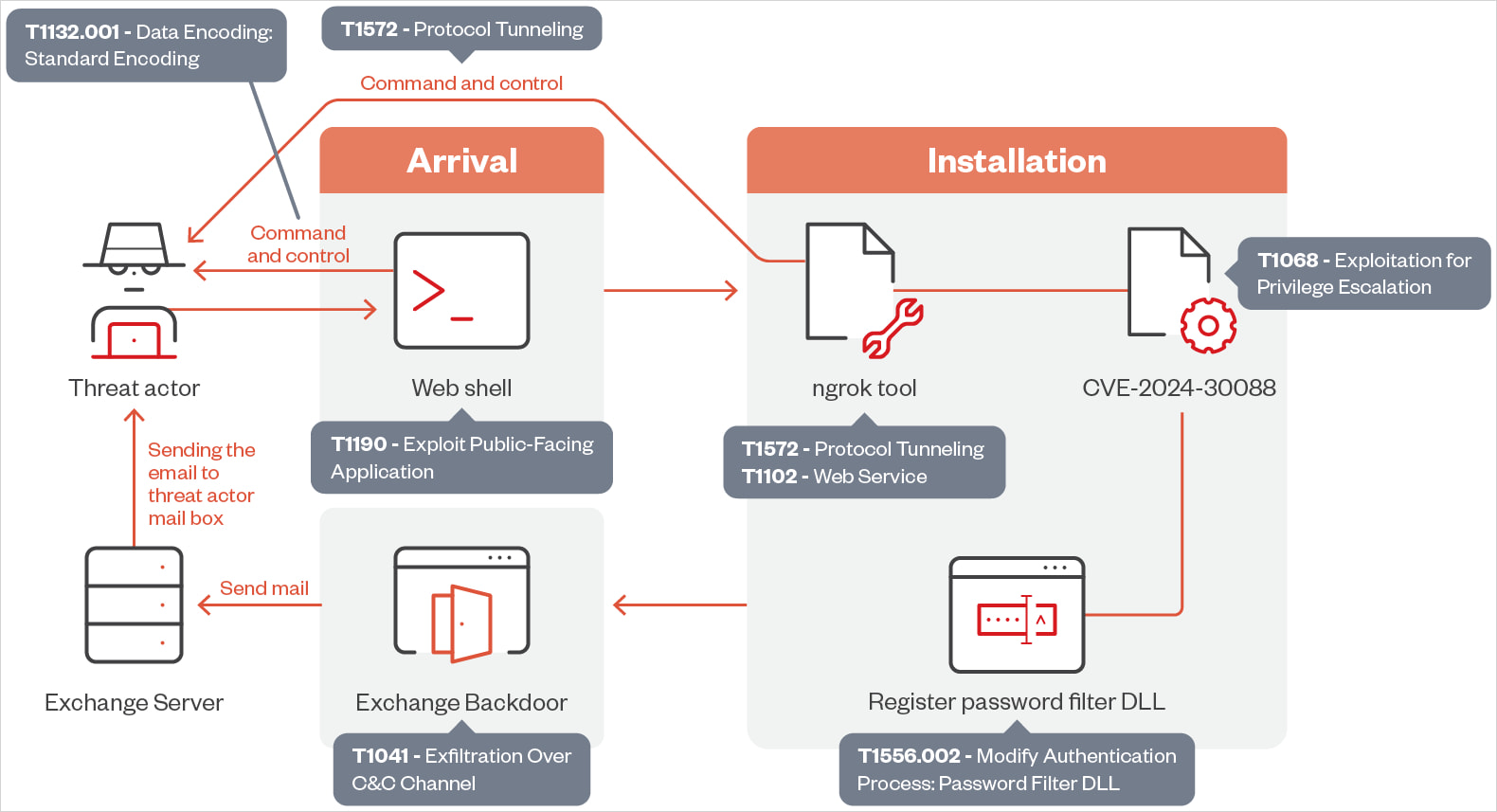
The attacks seen by Trend Micro begin with the exploitation of a vulnerable web server to upload a web shell, giving the attackers the ability to execute remote code and PowerShell commands.
Once the web shell is active, OilRig leverages it to deploy additional tools, including a component designed to exploit the Windows CVE-2024-30088 flaw.
CVE-2024-30088 is a high-severity privilege escalation vulnerability Microsoft fixed in June 2024, enabling attackers to escalate their privileges to the SYSTEM level, giving them significant control over the compromised devices.
Microsoft has acknowledged a proof-of-concept exploit for CVE-2024-30088 but has not yet marked the flaw as actively exploited on its security portal. CISA has also not reported it as previously exploited in ts Known Exploited Vulnerability catalog.
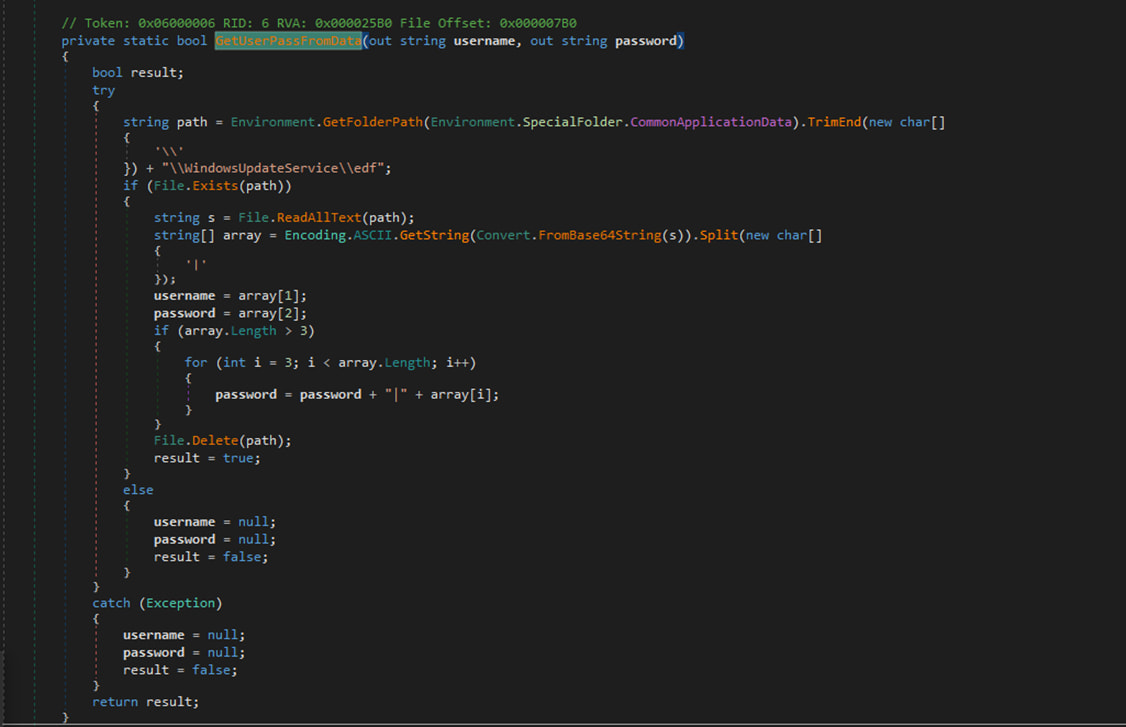
Next, OilRig registers a password filter DLL to intercept plaintext credentials during password change events and then downloads and installs the remote monitoring and management tool ‘ngrok,’ used for stealthy communications through secure tunnels.
Another new tactic by the threat actors is the exploitation of on-premise Microsoft Exchange servers to steal credentials and exfiltrate sensitive data via legitimate email traffic that is hard to detect.
Source: Trend Micro
The exfiltration is facilitated by a new backdoor named ‘StealHook,’ while Trend Micro says government infrastructure is often used as a pivot point to make the process appear legitimate.
“The key objective of this stage is to capture the stolen passwords and transmit them to the attackers as email attachments,” explains Trend Micro in the report.
“Additionally, we observed that the threat actors leverage legitimate accounts with stolen passwords to route these emails through government Exchange Servers.”
Source: Trend Micro
TrendMicro says there are code similarities between StealHook and backdoors OilRig used in past campaigns, like Karkoff, so the latest malware appears to be an evolutionary step rather than a novel creation from scratch.
Also, this is not the first time OilRig has used Microsoft Exchange servers as an active component of their attacks. Almost a year ago, Symantec reported that APT34 installed a PowerShell backdoor dubbed ‘PowerExchange’ on on-premise Exchange servers capable of receiving and executing commands via email.
The threat actor remains highly active in the Middle East region, and its affiliation with FOX Kitten, while unclear at this time, is worrying for the potential of adding ransomware to its attack arsenal.
Since most of the targeted entities are in the energy sector, according to Trend Micro, operational disruptions in these organizations could severely impact many people.



