Experts spotted new variants of the Eagerbee backdoor being used in attacks on government organizations and ISPs in the Middle East.
Kaspersky researchers reported that new variants of the Eagerbee backdoor being used in attacks against Internet Service Providers (ISPs) and government entities in the Middle East.
The Kaspersky’s analysis revealed new attack components, including a service injector for backdoor deployment and plugins for payload delivery, file/system access, and remote control.
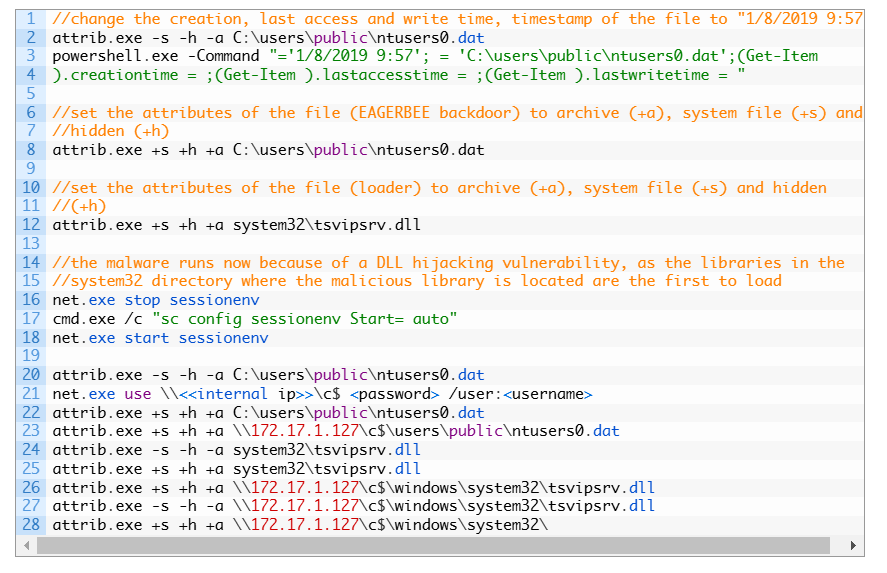
The initial access method is still unknown, but threat actors deployed a backdoor injector, tsvipsrv.dll, and payload ntusers0.dat via the SessionEnv service.
The service injector targets the Themes service, injecting the EAGERBEE backdoor into its memory along with the stub code to decompress the malware. It decompresses and executes the backdoor via a stub, then cleans up by restoring the original handler.
The backdoor, named dllloader1x64.dll, gathers system information, including NetBIOS name, OS details, processor architecture, and IP addresses. It uses a mutex (mstoolFtip32W) to ensure a single instance and includes a time check to plan the execution within a specified weekly schedule. However, it’s configured to run 24/7 in observed cases, checking every 15 seconds if outside the allowed execution window.
The configuration of the malware is stored in a file or hardcoded in the backdoor binary, it includes C2 server details decoded using XOR. The malicious code retrieves proxy settings from the registry, connects via proxy or directly to the C2 server, and supports SSL/TLS if configured. After establishing a TCP connection, it sends system data to the C2, which responds with the Plugin Orchestrator. The backdoor verifies the response and executes the payload without mapping it into memory.
The orchestrator injects itself, gathers additional data (domain name, memory usage, locale, time zone, process details, and plugin IDs), and reports to the C2 server. It also checks for elevated privileges and collects details on all running processes, including process IDs, thread counts, parent processes, and executable paths.
The backdoor uses plugins in the form of DLL files and export three methods using ordinals. The plugin orchestrator starts by invoking the exported method of the plugin with the ordinal number 3.
The method injects the plugin DLL into memory, initializes it via the DllMain method (ordinal 1), and then executes its functionality using the method at ordinal 2.
The orchestrator can send commands to execute to the plugins, the researchers analyzed five plugins used by the backdoor:
- File Manager Plugin: Handles file system operations and can modify file permissions, inject additional payloads into memory, and execute command lines.
- Process Manager Plugin: Manages system processes and can execute command lines or modules in the security context of specific user accounts.
- Remote Access Manager Plugin: Facilitates remote access by enabling RDP sessions, it can also inject command shells into legitimate processes for stealth.
- Service Manager Plugin: Controls system services.
- Network Manager Plugin: Monitors and lists active network connections.
“EAGERBEE was deployed in several organizations in East Asia. Two of these organizations were breached via the infamous ProxyLogon vulnerability (CVE-2021-26855) in Exchange servers, after which malicious webshells were uploaded and utilized to execute commands on the breached servers.” concludes the report. “Because of the consistent creation of services on the same day via the same webshell to execute the EAGERBEE backdoor and the CoughingDown Core Module, and the C2 domain overlap between the EAGERBEE backdoor and the CoughingDown Core Module, we assess with medium confidence that the EAGERBEE backdoor is related to the CoughingDown threat group.”