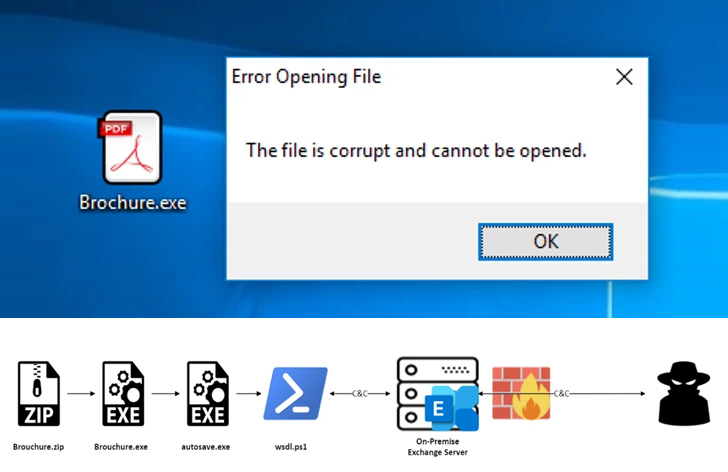
An unnamed government entity associated with the United Arab Emirates (U.A.E.) was targeted by a likely Iranian threat actor to breach the victim’s Microsoft Exchange Server with a “simple yet effective” backdoor dubbed PowerExchange.
According to a new report from Fortinet FortiGuard Labs, the intrusion relied on email phishing as an initial access pathway, leading to the execution of a .NET executable contained with a ZIP file attachment.
The binary, which masquerades as a PDF document, functions as a dropper to execute the final payload, which then launches the backdoor.
PowerExchange, written in PowerShell, employs text files attached to emails for command-and-control (C2) communication. It allows the threat actor to run arbitrary payloads and upload and download files from and to the system.
The custom implant achieves this by making use of the Exchange Web Services (EWS) API to connect to the victim’s Exchange Server and uses a mailbox on the server to send and receive encoded commands from its operator.
“The Exchange Server is accessible from the internet, saving C2 communication to external servers from the devices in the organizations,” Fortinet researchers said. “It also acts as a proxy for the attacker to mask himself.”
That said, it’s currently not known how the threat actor managed to obtain the domain credentials to connect to the target Exchange Server.
Fortinet’s investigation also uncovered Exchange servers that were backdoored with several web shells, one of which is called ExchangeLeech (aka System.Web.ServiceAuthentication.dll), to achieve persistent remote access and steal user credentials.
PowerExchange is suspected to be an upgraded version of TriFive, which was previously used by the Iranian nation-stage actor APT34 (aka OilRig) in intrusions targeting government organizations in Kuwait.
Furthermore, communication via internet-facing Exchange servers is a tried-and-tested tactic adopted by the OilRig actors, as observed in the case of Karkoff and MrPerfectionManager.
“Using the victim’s Exchange server for the C2 channel allows the backdoor to blend in with benign traffic, thereby ensuring that the threat actor can easily avoid nearly all network-based detections and remediations inside and outside the target organization’s infrastructure,” the researchers said.