Identifizieren Sie Ihre IT-Schwachstellen
mit nur einem Klick
- Keine Vorkenntnisse
- No Installation required

Erhalten Sie sofortigen Einblick in Ihre externe Risikooberfläche – keine technischen Kenntnisse erforderlich.
4.8 / 5 Basierend auf 4.109 Bewertungen | DSGVO konform
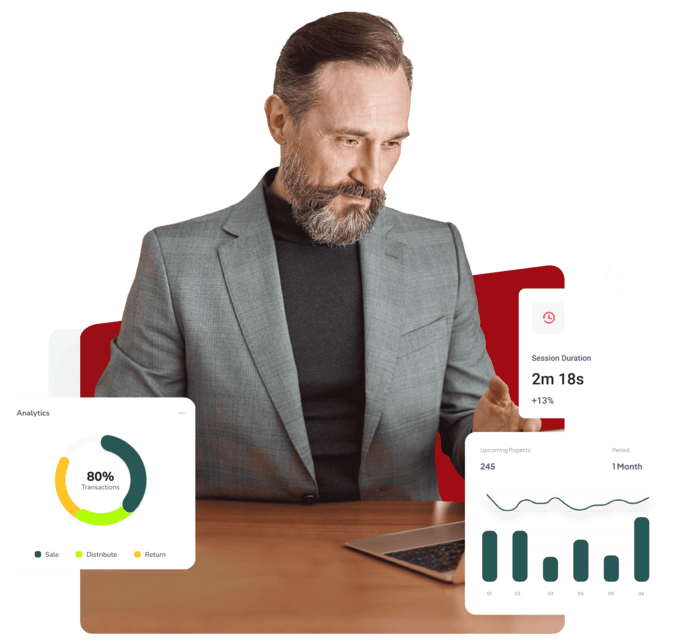







Ein Klick. Vollständige Transparenz.
- Unternehmen/Investoren
- Kreditschutzverbände
- Versicherungsgesellschaften
- Rechnungsprüfer
- Wiederverkäufer
Kennen Sie die Risiken.
Kosten vermeiden.
We help identify critical IT vulnerabilities and provide smart, budget-conscious fixes—so you can stay focused on growth, not security gaps.
See your system from a hacker’s viewpoint

Zero system impact, no service delay

Instant steps to reduce exposure fast

Support for due diligence, on demand



Risiken überwachen.
Erhalten Sie einen Branchenindex.
Credit protection helps manage financial risk—so why not cybersecurity?
Gain insight into their partners’ digital vulnerabilities. In a world of AI-powered phishing, ransomware, and darknet activity, understanding external cyber risk is essential for proactive protection.
Fully Automated Interface with Complete Documentation

Round-the-Clock Service. Data at Your Fingertips.

Dedicated Support • White-Label On Request




Making IT Risks Measurable.
To assess the likelihood and potential impact of risks, we provide aggregated benchmark data for calculations, along with recurring real-time analyses of your own datasets—accessible through a seamless interface.
Insights from Over 28 Million Companies Across the EU

Integration with Insurance Systems

One-Time Assessments or Continuous Monitoring

Complete Historical Data Across All Sets

Real-Time Alerts for New Vulnerabilities




Comprehensive Analysis.
Expert Recommendations.
From quick plausibility checks to in-depth scans and thorough penetration tests—we only need your domain or email. All results are delivered on a single platform, with recurring assessments as needed to maintain top-tier security
Fully White-Labeled, Client-Branded Reports

One-Time or Scheduled Security Testing

Company-Specific Historical & Statistical Insights

Real-Time Alerts for Emerging Vulnerabilities




Verlässliche Partnerschaft.
Solides Wachstum.
The added value for customers is the added value in sales, and we create this together with resellers around the world in order to offer customers more security every day.
Individuelle Analysen oder

Laufende Überwachung aller Kunden in Echtzeit

Professionelle Verkaufsunterlagen

Attraktive Konditionen und gestaffelte Preise




Intelligente Cybersicherheit
Jetzt auf Schwachstellen prüfen
- Keine Berechtigungsnachweise
- Darknet-Überwachung
- Überwachung des Bereichs
- Server-Überwachung
Erschwingliche Preise

25% speichern
Start
€ 130
€ 99
Pro Monat
- 1 Unternehmen
- 100 Assets
- quarterly Abfrageintervall
- Darknet Überwachung
- Domain Überwachung
- Server Überwachung
Am beliebtesten
Business
€ 649
€ 495
Pro Monat
- 3 Companies
- 1000 Assets
- monthly Abfrageintervall
- Darknet Überwachung
- Domain Überwachung
- Server Überwachung
Prämie
€ 2550
€ 1950
Pro Monat
- 10 Companies
- 5000 Assets
- monthly Abfrageintervall
- Darknet Überwachung
- Domain Überwachung
- Server Überwachung
Unternehmen

€ 8500
€ 6500
Pro Monat
- 10 Companies
- 5000 Assets
- monthly Abfrageintervall
- Darknet Überwachung
- Domain Überwachung
- Server Überwachung
Start
€ 115
€ 75
Pro Monat
- 1 Unternehmen
- 100 Assets
- quarterly Abfrageintervall
- Darknet Überwachung
- Domain Überwachung
- Server Überwachung
Am beliebtesten
Business
€ 599
€ 399
Pro Monat
- 3 Companies
- 1000 Assets
- monthly Abfrageintervall
- Darknet Überwachung
- Domain Überwachung
- Server Überwachung
Prämie
€ 2200
€ 1450
Pro Monat
- 10 Companies
- 5000 Assets
- monthly Abfrageintervall
- Darknet Überwachung
- Domain Überwachung
- Server Überwachung
Unternehmen

€ 7500
€ 5500
Pro Monat
- 10 Companies
- 5000 Assets
- monthly Abfrageintervall
- Darknet Überwachung
- Domain Überwachung
- Server Überwachung
Let’s schedule your personalized offer
Jetzt Expertenrat einholen
Erklärung des CEO und Unternehmensvision
IT-Security kann sein
automatisiert
In der heutigen schnelllebigen Arbeitswelt sind IT-Abteilungen – ob intern oder ausgelagert – oft überfordert und agieren wie eine digitale Feuerwehr, die sich darauf konzentriert, Systeme betriebsbereit zu halten und kritische Probleme zu lösen. Daher werden proaktive Dienste wie Cybersicherheit häufig übersehen, weil alles „einfach funktioniert“ – bis es nicht mehr funktioniert. Diese Lücke führt zum Aufstieg der Schatten-IT, bei der Mitarbeiter versuchen, ihre Probleme selbst zu lösen und das Unternehmen so unabsichtlich Sicherheitsrisiken aussetzen. Sie verwenden Passwörter systemübergreifend wieder, manchmal sogar solche, die bei Datenschutzverletzungen kompromittiert wurden, und gefährden so sensible Unternehmensdaten.
We created Risk Monitor as a practical, affordable solution to support IT professionals. It helps Schwachstellen effizient identifizieren, raise awareness among users, and strengthen overall organizational security ohne dass umfangreiche technische Kenntnisse oder große Budgets erforderlich sind.
Testimonials

Optimales Werkzeug für
critical infrastructure.
The analysis also showed us our attack.
Vektoren aus dem Dark Web und von unseren Lieferanten. Unglaublich detailliert.
WERNER LEHNER
CIO, UDB

Sehr nützlich als
Wiederverkäufer für unsere Kunden.
We show customers weak points in the Darknet and monitor all domains and public servers. A lot of work has been done for us, and the benefits are enormous.
CHRISTIAN DICK
Geschäftsführer, bit-Studio
Wahrscheinlich die vielversprechendste
startup I have ever heard of.
The market benefit of this cybersecurity SaaS solution is enormous.
FLORIAN HAAS
MITGLIED DES MARKTBEIRATS, EY

Erweitertes Pentesting für
stärken Sie Ihre IT-Sicherheit
Our system uncovers all vulnerabilities hackers target—whether data breaches, insecure servers, weak passwords, or domain phishing—helping you stay one step ahead.

Keine Voraussetzungen oder technisches Fachwissen erforderlich

Keine Installation, Migration oder Implementierung erforderlich.

Mit nur einem Klick analysieren wir alles – auch das, was Unbefugte entdecken könnten.
Häufig gestellte Fragen
Wir bieten eine intuitive Lösung, die es Unternehmen ermöglicht monitor publicly exposed vulnerabilities and attack vectors—no technical expertise required. Proactively assess and mitigate security risks across your company’s IT systems with ease.
Wir ermöglichen automatisierte IT-Sicherheit durch kontinuierliche Verfolgung von Schwachstellen, bietet klare Einblicke und warnt Sie vor potenziellen Bedrohungen. So können IT-Teams Schwachstellen schnell erkennen und beheben, bevor sie eskalieren.
Für alle konzipiert, kein technischer Hintergrund erforderlich. Unsere Plattform bietet klare und unkomplizierte Einblicke in Schwachstellen und Sicherheitsrisiken, sodass jeder in Ihrem Unternehmen wirksame Maßnahmen ergreifen kann.
Wir verfolgen eine breite Palette von Sicherheitsrisiken, darunter Angriffsvektoren, Datenschutzverletzungen, offengelegte Passwörter, Schatten IT-Risikenund andere Schwachstellen, die von nicht autorisierten Benutzern oder Hackern möglicherweise ausgenutzt werden könnten.
Wir scannen kontinuierlich nach durchgesickerten Anmeldeinformationen, offengelegten Passwörtern und allen Sicherheitsvorfällen, die zu einem Datenschutzverletzung. Es hilft Unternehmen, über kompromittierte Informationen auf dem Laufenden zu bleiben und stellt sicher, dass umgehend Maßnahmen zum Schutz der Konten ergriffen werden.
Absolut! Wir sind ein praktischer und wertvoller Partner für Unternehmen jeder Größe. Unser einfacher, automatisierter Ansatz macht uns zur idealen Wahl für kleine Unternehmen ohne dedizierte Sicherheitsteams oder umfangreiche technische Ressourcen.











