Members of the North Korean hacker group Lazarus posing as recruiters are baiting Python developers with coding test project for password management products that include malware.
The attacks are part of the ‘VMConnect campaign’ first detected in August 2023, where the threat actors targeted software developers with malicious Python packages uploaded onto the PyPI repository.
According to a report from ReversingLabs, which has been tracking the campaign for over a year, Lazarus hackers host the malicious coding projects on GitHub, where victims find README files with instructions on how to complete the test.
The directions are meant to provide a sense professionalism and legitimacy to the whole process, as well as a sense of urgency.
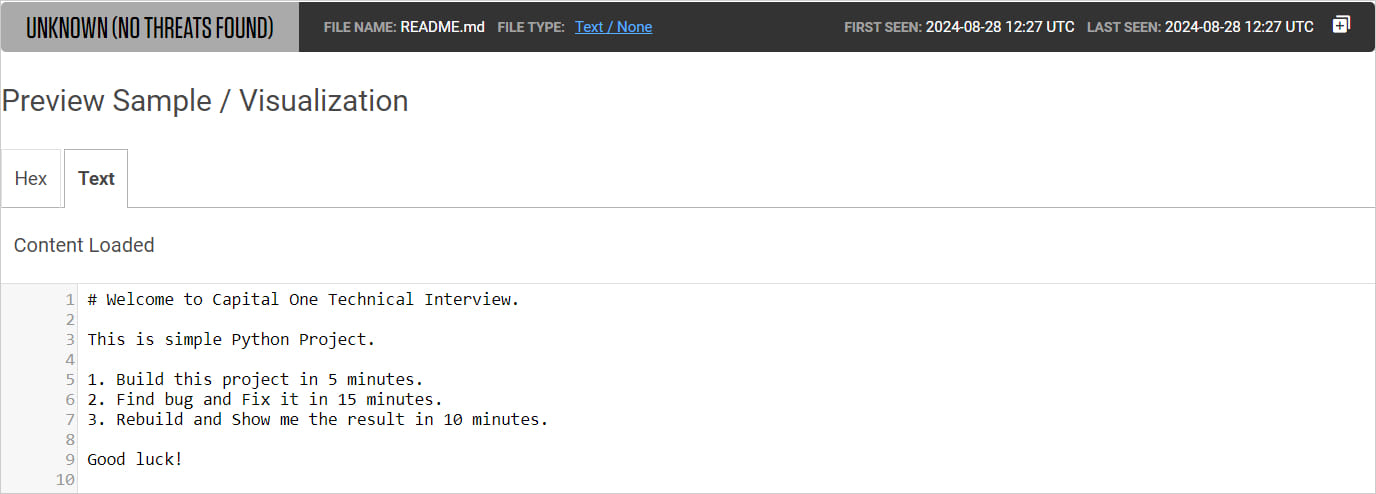
ReversingLabs found that the North Koreans impersonate large U.S. banks like Capital One to attract job candidates, likely offering them an enticing employment package.
Further evidence retrieved from one of the victims suggests that Lazarus actively approaches their targets over LinkedIn, a documented tactic for the group.
Find the bug
The hackers direct candidates to find a bug in a password manager application, submit their fix, and share a screenshot as proof of their work.
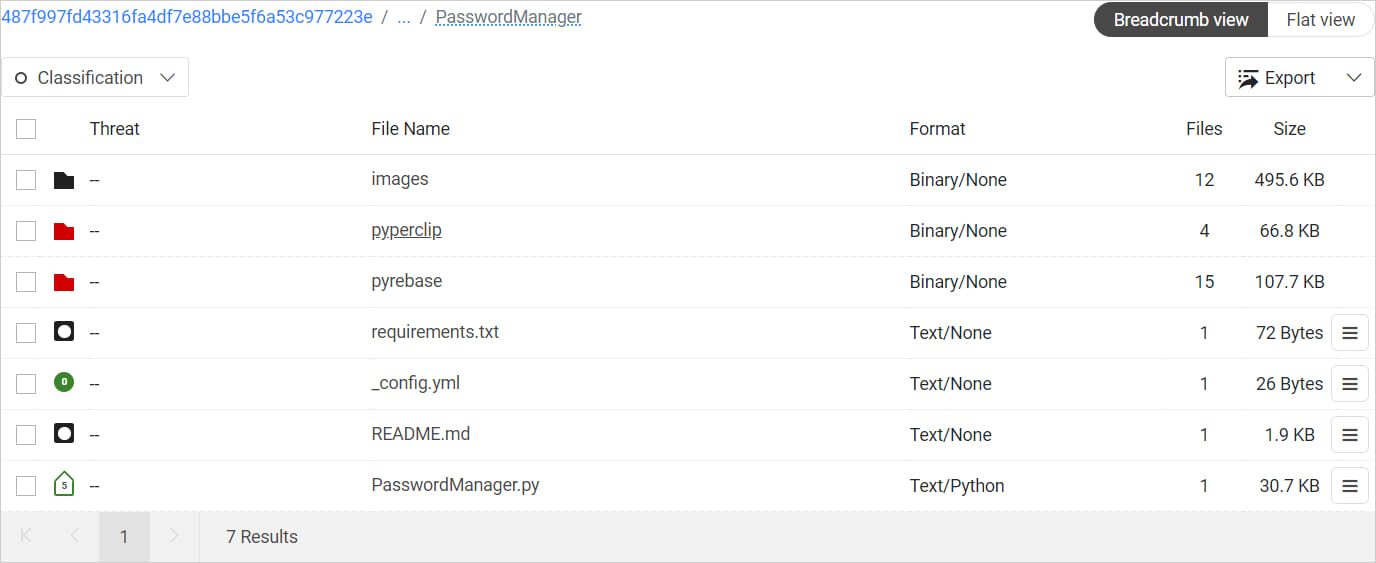
The README file for the project instruct the victim first to execute the malicious password manager application (‘PasswordManager.py’) on their system and then start looking for the errors and fixing them.
Quelle: ReversingLabs
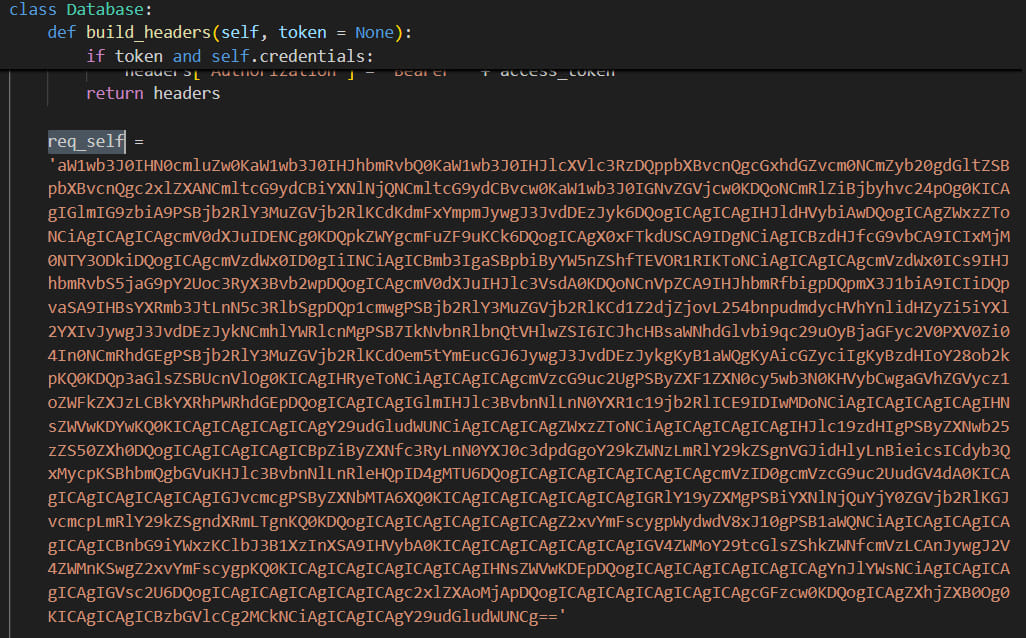
That file triggers the execution of a base64 obfuscated module hidden in the’_init_.py’ files of the ‘pyperclip’ and ‘pyrebase’ libraries.
The obfuscated string is a malware downloader that contacts a command and control (C2) server and awaits for commands. Fetching and running additional payloads is within its capabilities.
Quelle: ReversingLabs
To make sure that the candidates won’t check the project files for malicious or obfuscated code, the README file require the task to be completed quickly: five minutes for building the project, 15 minutes to implement the fix, and 10 minutes to send back the final result.
This is supposed to prove the developer’s expertise in working with Python projects and GitHub, but the goal is to make the victim skip any security checks that may reveal the malicious code.
Quelle: ReversingLabs
ReversingLabs has found evidence that the campaign was still active on July 31 and believe that it is ongoing.
Software developers receiving job application invites from users on LinkedIn or elsewhere should be wary about the possibility of deception and take into consideration that the profiles contacting them could be fake.
Before receiving the assignment, try to verify the other person’s identity and independently confirm with the company that a recruitment round is indeed underway.
Take the time to scan or carefully review the given code and only execute it in safe environments such as virtual machines or sandboxing applications.



