Eine neue Linux-Rootkit-Malware namens Pumakit wurde entdeckt, die Stealth- und fortgeschrittene Privilegienerweiterungstechniken nutzt, um ihre Präsenz auf Systemen zu verbergen.
Die Malware besteht aus mehreren Komponenten, darunter ein Dropper, speicherresidente ausführbare Dateien, ein Kernel-Modul-Rootkit und ein Shared Object (SO) Userland-Rootkit.
Elastic Security entdeckte Pumakit in einer verdächtigen Binärdatei ("cron"), die am 4. September 2024 auf VirusTotal hochgeladen wurde, und meldete, dass sie keinen Einblick darin hat, wer sie verwendet und welche Ziele sie verfolgt.
Im Allgemeinen werden diese Tools von fortschrittlichen Bedrohungsakteuren eingesetzt, die es auf kritische Infrastrukturen und Unternehmenssysteme abgesehen haben, um diese auszuspionieren, Geld zu stehlen und zu stören.
Das Pumakit
Pumakit verwendet einen mehrstufigen Infektionsprozess, der mit einem Dropper namens "cron" beginnt, der eingebettete Nutzdaten ("/memfd:tgt" und "/memfd:wpn") vollständig aus dem Speicher ausführt.
Die Nutzlast "/memfd:wpn", die in einem untergeordneten Prozess ausgeführt wird, führt Umgebungsprüfungen und Kernel-Image-Manipulationen durch und setzt schließlich das LKM-Rootkit-Modul ("puma.ko") im Systemkernel ein.
Eingebettet in das LKM-Rootkit ist Kitsune SO ('lib64/libs.so'), das als Userland-Rootkit fungiert und sich mithilfe von 'LD_PRELOAD' in Prozesse einschleust, um Systemaufrufe auf Benutzerebene abzufangen.
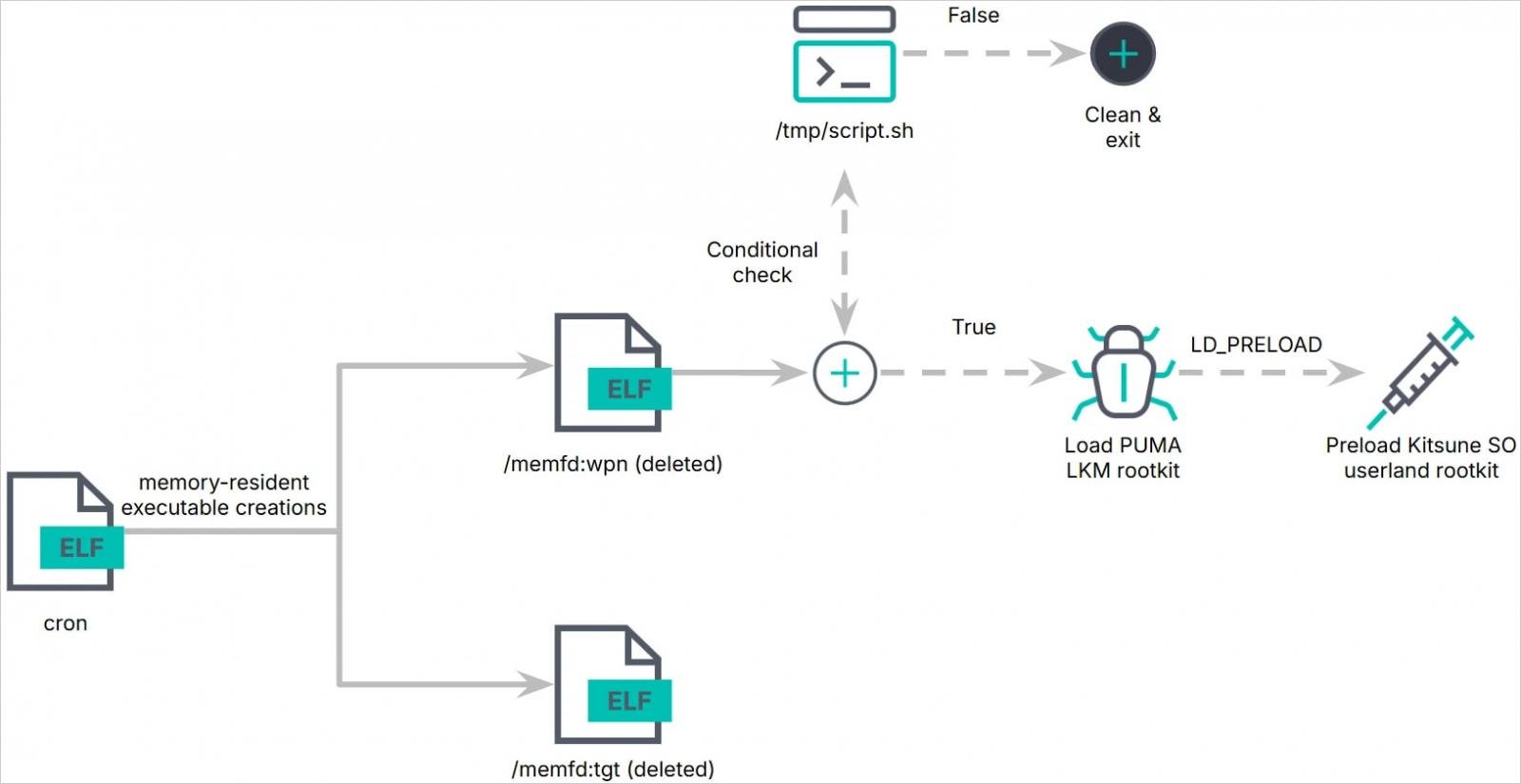
Quelle: Elastic Security
Heimliche Privilegienerweiterung
Das Rootkit folgt einer bedingten Aktivierung und prüft vor dem Laden auf bestimmte Kernel-Symbole, einen sicheren Boot-Status und andere Voraussetzungen.
Elastic zufolge nutzt Puma die Funktion "kallsyms_lookup_name()", um das Systemverhalten zu manipulieren. Dies deutet darauf hin, dass das Rootkit nur für Linux-Kernel vor Version 5.7 entwickelt wurde, da neuere Versionen die Funktion nicht mehr exportieren und daher nicht von anderen Kernel-Modulen verwendet werden können.
"Die Fähigkeit des LKM-Rootkits, das Systemverhalten zu manipulieren, beginnt mit der Verwendung der syscall-Tabelle und seiner Abhängigkeit von kallsyms_lookup_name() für die Symbolauflösung", erklären die Elastic-Forscher Remco Sprooten und Ruben Groenewoud.
"Im Gegensatz zu modernen Rootkits, die auf die Kernel-Versionen 5.7 und höher abzielen, verwendet das Rootkit keine kprobeswas darauf hindeutet, dass es für ältere Kernel konzipiert ist."
Puma hakt 18 Syscalls und mehrere Kernel-Funktionen mit "ftrace" ein, um Privilegien zu erweitern, Befehle auszuführen und Prozesse zu verstecken.
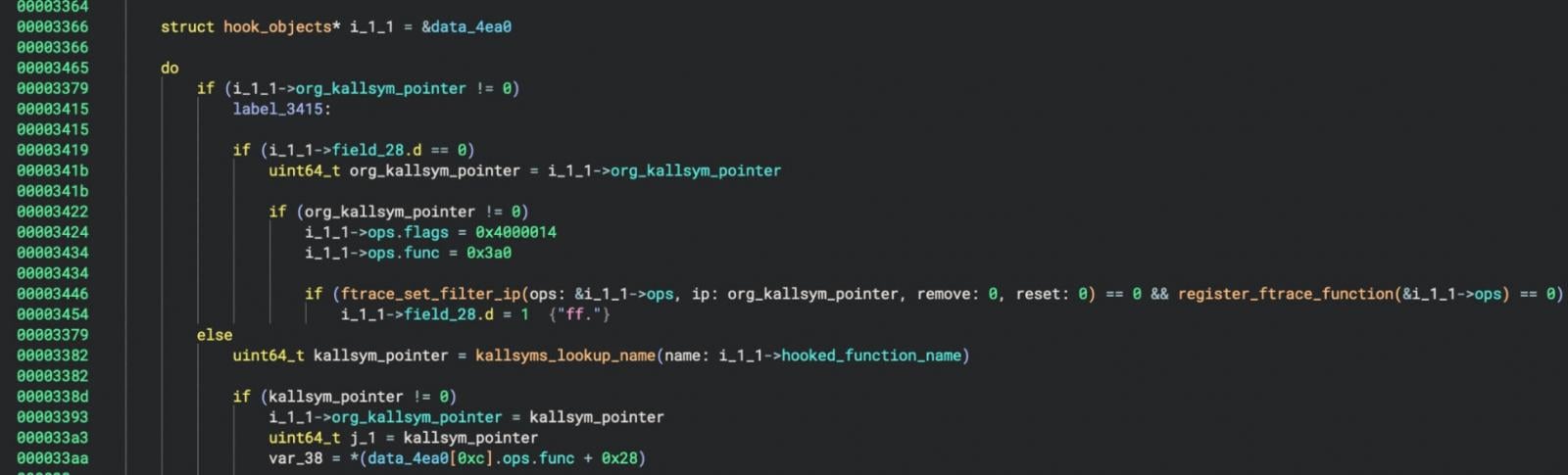
Quelle: Elastic Security
Die Kernel-Funktionen "prepare_creds" und "commit_creds" werden missbraucht, um die Anmeldedaten von Prozessen zu ändern und bestimmten Prozessen Root-Rechte zu gewähren.
Das Rootkit kann seine eigene Präsenz vor Kernelprotokollen, Systemtools und Antivirenprogrammen verbergen und kann auch bestimmte Dateien in einem Verzeichnis und Objekte vor Prozesslisten verbergen.
Wenn die Hooks unterbrochen werden, werden sie vom Rootkit neu initialisiert, wodurch sichergestellt wird, dass seine bösartigen Änderungen nicht rückgängig gemacht werden und das Modul nicht entladen werden kann.
Das Userland-Rootkit Kitsune SO arbeitet in Synergie mit Puma und dehnt seine Stealth- und Kontrollmechanismen auf die Interaktionen mit dem Benutzer aus.
Es fängt Systemaufrufe auf Benutzerebene ab und ändert das Verhalten von Programmen wie ls, ps, netstat, top, htop und cat, um Dateien, Prozesse und Netzwerkverbindungen zu verbergen, die mit dem Rootkit verbunden sind.
Es kann auch dynamisch alle anderen Dateien und Verzeichnisse auf der Grundlage von durch Angreifer definierten Kriterien verbergen und bösartige Binärdateien für Benutzer und Systemadministratoren völlig unsichtbar machen.
Kitsune SO wickelt auch die gesamte Kommunikation mit dem Command-and-Control-Server (C2) ab, leitet Befehle an das LKM-Rootkit weiter und übermittelt Konfigurations- und Systeminformationen an die Betreiber.
Neben Datei-Hashes hat Elastic Security eine YARA-Regel veröffentlicht, die Linux-Systemadministratoren helfen soll, Pumakit-Angriffe zu erkennen.




