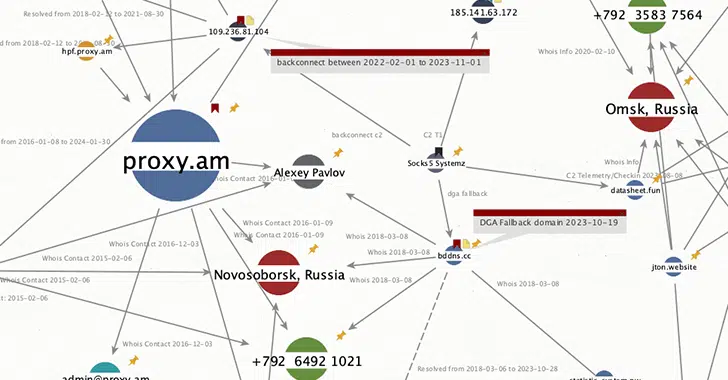
A malicious botnet called Socks5Systemz is powering a proxy service called PROXY.AM, according to new findings from Bitsight.
“Proxy malware and services enable other types of criminal activity adding uncontrolled layers of anonymity to the threat actors, so they can perform all kinds of malicious activity using chains of victim systems,” the company’s security research team said in an analysis published last week.
The disclosure comes merely weeks after the Black Lotus Labs team at Lumen Technologies revealed that systems compromised by another malware known as Ngioweb are being abused as residential proxy servers for NSOCKS.
Socks5Systemz, originally advertised in the cybercrime underground as far back as March 2013, was previously documented by BitSight as being deployed as part of cyber attacks targeting distributing PrivateLoader, SmokeLoader, and Amadey.
The primary objective of the malware is to turn compromised systems into proxy exit nodes, which are then advertised for other actors, typically cybercriminals who are looking to obscure the source of their attacks. The illegal proxy service has been around since 2016.
The top countries with the most number of infected hosts are India, Indonesia, Ukraine, Algeria, Vietnam, Russia, Turkey, Brazil, Mexico, Pakistan, Thailand, the Philippines, Colombia, Egypt, the United States, Argentina, Bangladesh, Morocco, and Nigeria.
By January 2024, the botnet’s size is said to have had mushroomed to a daily average of around 250,000 machines, although current estimates put it anywhere from 85,000 to 100,000. As of writing, the PROXY.AM website claims it has 80,888 proxy nodes available from 31 different countries.
“In December 2023, the threat actor lost control of Socks5Systemz V1 and had to rebuild the botnet from scratch with a completely different [command-and-control] infrastructure — which we call the Socks5Systemz V2 botnet,” Bitsight said, explaining the reasons for the decrease.
“Because Socks5Systemz is dropped by loaders (such as Privateloader, SmokeLoader, or Amadey) that persist on the system, new distribution campaigns were used to replace old infections with new payloads.”
PROXY.AM (proxy[.]am and proxyam[.]one) markets itself as offering “elite, private, and anonymous proxy servers” for anywhere between $126/month (Unlimited Pack) and $700/month (VIP Pack).
The disclosure follows a report from Trend Micro that detailed threat actors’ ongoing attempts to target misconfigured Docker Remote API servers with the Gafgyt botnet malware to help conduct distributed denial-of-service (DDoS) attacks against targets of interest.
While Gafgyt has a track record of targeting vulnerable IoT devices, the malware’s exploitation of weak SSH passwords and Docker instances indicates a widening of its scope.
“We noticed attackers targeting publicly exposed misconfigured Docker remote API servers to deploy the malware by creating a Docker container based on a legitimate ‘alpine’ Docker image,” security researcher Sunil Bharti said. “Along with deployment of Gafgyt malware, attackers used Gafgyt botnet malware to infect the victim.”
Cloud misconfigurations have proven to be an attractive attack surface for threat actors looking to deploy cryptocurrency miners, steal data, and co-opt them into botnets for DDoS attacks.
Per a new empirical analysis by a group of researchers from Leiden University and TU Delft, as many as 215 instances were found exposing sensitive credentials that could potentially grant attackers unauthorized access to services like databases, cloud infrastructure, and third-party APIs.
A majority of the instances were located in the United States, India, Australia, Great Britain, Brazil, and South Korea, spanning several sectors such as information technology (IT), retail, finance, education, media, and healthcare.
“The findings underscore the pressing need for better system administration and vigilant oversight to prevent data leaks,” the Modat Team said. “The impact of leaking these secrets can be immense, ranging from full control of organizations’ security infrastructure to impersonation and infiltration into protected cloud infrastructure.”