The cybersecurity community has renewed its focus on two critical vulnerabilities, collectively dubbed “LDAPNightmare.” While these vulnerabilities—CVE-2024-49112 and CVE-2024-49113—were previously disclosed, SafeBreach Labs’ recent release of a proof-of-concept (PoC) exploit for CVE-2024-49113 has brought them back into the spotlight. These flaws pose serious risks to enterprise networks, with CVE-2024-49112 classified as a zero-click vulnerability.
What Are CVE-2024-49112 and CVE-2024-49113?
CVE-2024-49112: The Zero-Click Vulnerability
CVE-2024-49112 affects the Windows Lightweight Directory Access Protocol (LDAP) service. It is categorized as a remote code execution (RCE) vulnerability and is caused by an integer overflow (CWE-190). Exploitation could allow attackers to crash unpatched Windows servers, including Active Directory Domain Controllers (DCs), potentially disrupting enterprise operations.
With a CVSS score of 9.8, CVE-2024-49112 is particularly concerning due to its zero-click nature, meaning no user interaction is required, and the critical role that Domain Controllers play in enterprise networks. The vulnerability could allow attackers to disrupt core business operations without any user engagement.
CVE-2024-49113: Denial of Service in LDAP
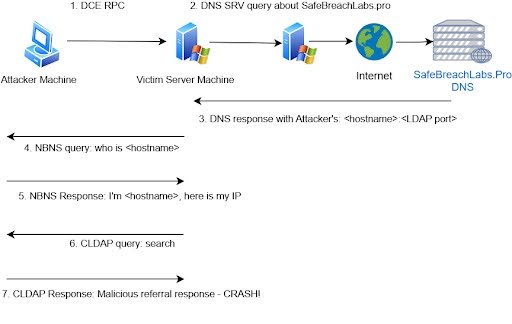
CVE-2024-49113 is a Denial of Service (DoS) vulnerability in the Windows Lightweight Directory Access Protocol (LDAP). The flaw arises from an out-of-bounds read (CWE-125), which allows attackers to crash unpatched servers, including those hosting Active Directory Lightweight Directory Tools (AD LDS).
According to the SafeBreach Labs blog, a recently released PoC exploit demonstrates how attackers could take advantage of this flaw to crash enterprise environments.
Technical Highlights
CVE-2024-49112:
- Affected Component: Windows Lightweight Directory Access Protocol (LDAP) service.
- Impact: Remote code execution via integer overflow, leading to potential system crashes.
- Exploitation Requirements: Zero-click; no user interaction required.
- Mitigation: Apply patches and limit LDAP access to trusted hosts.
CVE-2024-49113:
- Affected Component: Windows Lightweight Directory Access Protocol (LDAP).
- Impact: Denial of Service via out-of-bounds read, causing server crashes.
- Exploitation Requirements: Requires specially crafted LDAP requests.
- Mitigation: Patch affected systems and enforce strict access controls.
How Attackers Might Exploit These Vulnerabilities
Attackers could exploit CVE-2024-49112 and CVE-2024-49113 in the following ways:
CVE-2024-49112 (Zero-Click):
- Disruption of Services: By sending malicious LDAP requests, attackers could crash Domain Controllers, leading to significant downtime for enterprise operations.
- Denial of Service (DoS): Exploiting this vulnerability could create a persistent DoS scenario, making critical directory services unavailable.
- Precursor to Further Attacks: While this vulnerability is primarily disruptive, attackers could leverage the downtime to exploit other weaknesses in the network.
CVE-2024-49113 (DoS):
- Service Disruption: Attackers could leverage this vulnerability to take down critical LDAP services, disrupting enterprise workflows.
- Attack Amplification: By crashing essential services, attackers could create opportunities for additional exploitation or reconnaissance.
Why LDAPNightmare Matters
The combination of CVE-2024-49112 and CVE-2024-49113 poses a dual threat to enterprise networks:
- Zero-Click Exploitation: CVE-2024-49112 requires no user interaction, making it easier for attackers to execute without detection.
- Denial of Service: CVE-2024-49113 could enable attackers to cause widespread disruptions by crashing critical LDAP services.
These vulnerabilities highlight the importance of maintaining updated systems and monitoring LDAP traffic to detect potential exploitation attempts.
Mitigation
SafeBreach Labs’ GitHub repository provides detailed insights into CVE-2024-49113, while additional resources focus on mitigating CVE-2024-49112.
Mitigation Steps:
- Apply Patches: Microsoft has released updates addressing both vulnerabilities. Organizations should prioritize these patches to mitigate risks.
- Restrict LDAP Access: Limit LDAP service exposure to trusted hosts and enforce network segmentation.
- Monitor Network Traffic: Implement monitoring tools to detect unusual LDAP activity and potential exploitation attempts.
- Harden Systems: Use secure configurations for Domain Controllers and LDAP services to reduce exposure.
LDAPNightmare, encompassing CVE-2024-49112 and CVE-2024-49113, serves as a stark reminder of the critical importance of securing directory services. With one vulnerability allowing zero-click exploitation and the other enabling Denial of Service attacks, organizations must act swiftly to protect their networks.
For detailed technical insights and to explore the PoC exploits, visit the SafeBreach Labs blog and the GitHub repository. Stay vigilant and proactive to safeguard your systems against these critical threats.



