A sophisticated Mirai-based botnet is leveraging zero-day exploits and custom vulnerabilities to compromise industrial routers and smart home devices. First observed in February 2024, this botnet has rapidly evolved, exploiting both n-day und zero-day flaws, including a critical vulnerability, CVE-2024-12856, in Four-Faith industrial routers.
Emerging Exploitation Activity
Researchers from Chainxin X Lab reported that exploitation of CVE-2024-12856 began in late December 2024, shortly after its discovery by VulnCheck. This vulnerability, combined with custom exploits for flaws in Neterbit routers und Vimar smart home devices, has expanded the botnet’s infection capabilities.
Botnet Profile
The botnet, whose name contains offensive language, is built on a Mirai-based framework and maintains an average of 15,000 active daily bot nodes across the following countries:
- China
- Vereinigte Staaten
- Russia
- Türkei
- Iran
Key Features:
- Attack Objectives: Primarily used for DDoS attacks targeting hundreds of entities daily. Activity peaked in October and November 2024.
- Propagation Mechanism: Combines public and private exploits for over 20 vulnerabilities to infect diverse devices.
- Brute Force Module: Targets devices with weak Telnet passwords.
- Custom Malware Attributes: Implements Mirai-like commands, uses custom UPX packing, and scans for additional vulnerabilities across networks.
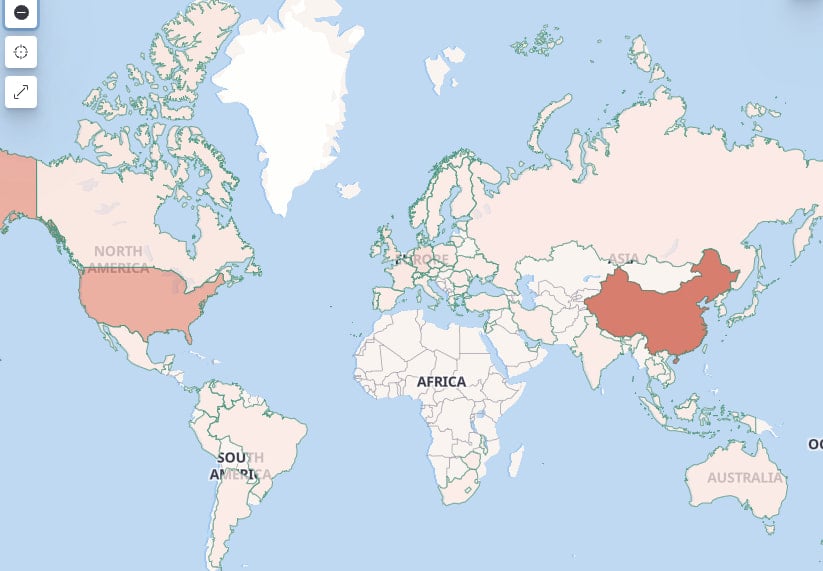 Targeted countries
Targeted countries
Source: X Lab
Siehe auch: Du willst also ein Hacker werden?
Offensive Sicherheit, Bug Bounty Kurse
Entdecken Sie Ihr schwächstes Glied. Seien Sie proaktiv, nicht reaktiv. Cyberkriminelle brauchen nur eine Schwachstelle, um zuzuschlagen.
Targeted Devices and Vulnerabilities
The botnet exploits vulnerabilities in a wide range of devices, including:
| Device Type | Exploits Used |
|---|---|
| ASUS routers | N-day exploits |
| Huawei routers | CVE-2017-17215 |
| Neterbit routers | Custom exploit |
| LB-Link routers | CVE-2023-26801 |
| Four-Faith routers | CVE-2024-12856 (zero-day) |
| PZT cameras | CVE-2024-8956, CVE-2024-8957 |
| Kguard DVRs | Remote code execution vulnerabilities |
| Lilin DVRs | RCE exploits |
| Vimar smart home devices | Likely undisclosed vulnerabilities |
| 5G/LTE devices | Weak credentials and misconfigurations |
The botnet actively infects DVRs, routersund smart home devices, further highlighting the vulnerabilities present in internet-exposed systems.
DDoS Attack Characteristics
X Lab’s telemetry revealed that the botnet’s DDoS attacks are:
- Short in Duration: Lasting between 10-30 seconds.
- High in Intensity: Surpassing 100 Gbps of traffic, capable of disrupting even robust infrastructures.
- Global in Reach: Attack targets span China, the US, Deutschland, the UKund Singapur, affecting various industries.
Botnet attack volumes
Source: X Lab
Trending: Top 10 Things to Do After Installing Kali Linux
Trending: Network Security Tool: Sara (RouterOS Security Inspector)
Mitigation Recommendations
To defend against this botnet, users should:
- Install Updates: Apply the latest firmware updates to patch known vulnerabilities.
- Replace EOL Devices: Upgrade end-of-life devices to models receiving regular security updates.
- Secure Configurations:
- Change default credentials to strong, unique passwords.
- Disable unnecessary remote access interfaces.
- Network Monitoring: Use intrusion detection systems to identify anomalous behavior.
Trending: Kali Linux 2024.4: 14 New Tools, Python 3.12, and Raspberry Pi Enhancements
Sind Sie ein Sicherheitsforscher? Oder ein Unternehmen, das Artikel über Cybersicherheit, offensive Sicherheit (im Zusammenhang mit Informationssicherheit im Allgemeinen) schreibt, die zu unserem speziellen Publikum passen und es wert sind, geteilt zu werden? Wenn Sie Ihre Idee in einem Artikel ausdrücken möchten, kontaktieren Sie uns hier für ein Angebot: [email protected]



