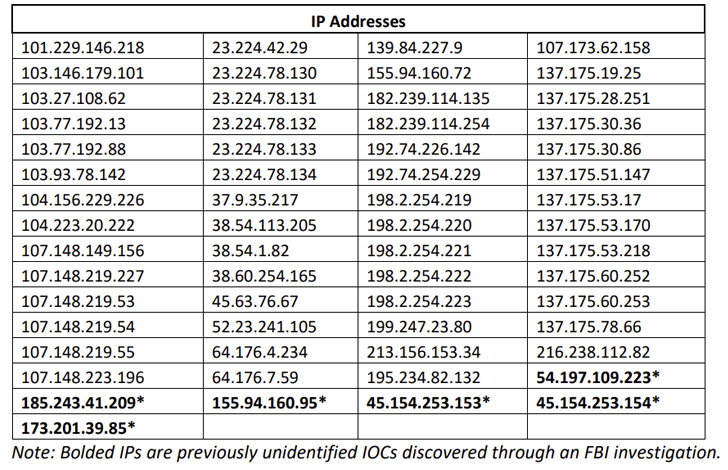
The U.S. Federal Bureau of Investigation (FBI) is warning that Barracuda Networks Email Security Gateway (ESG) appliances patched against a recently disclosed critical flaw continue to be at risk of potential compromise from suspected Chinese hacking groups.
It also deemed the fixes as “ineffective” and that it “continues to observe active intrusions and considers all affected Barracuda ESG appliances to be compromised and vulnerable to this exploit.”
Tracked as CVE-2023-2868 (CVSS score: 9.8), the zero-day bug is said to have been weaponized as early as October 2022, more than seven months before the security hole was plugged. Google-owned Mandiant is tracking the China-nexus activity cluster under the name UNC4841.
The remote command injection vulnerability, impacting versions 5.1.3.001 through 9.2.0.006, allows for unauthorized execution of system commands with administrator privileges on the ESG product.
In the attacks observed so far, a successful breach acts as a conduit to deploy multiple malware strains such as SALTWATER, SEASIDE, SEASPY, SANDBAR, SEASPRAY, SKIPJACK, WHIRLPOOL, and SUBMARINE (aka DEPTHCHARGE) that allow for the execution of arbitrary commands and defense evasion.
“The cyber actors utilized this vulnerability to insert malicious payloads onto the ESG appliance with a variety of capabilities that enabled persistent access, email scanning, credential harvesting, and data exfiltration,” the FBI said.
The threat intelligence firm has characterized UNC4841 as both aggressive and skilled, demonstrating a flair for sophistication and quickly adapting their custom tooling to employ additional persistence mechanisms and maintain their foothold into high priority targets.
The federal agency is recommending customers to isolate and replace all affected ESG devices with immediate effect, and scan the networks for suspicious outgoing traffic.
Update
When reached for comment, Barracuda Networks shared the below statement with The Hacker News –
Barracuda’s guidance remains consistent for customers. Out of an abundance of caution and in furtherance of our containment strategy, we recommend impacted customers replace their compromised appliance. If a customer received the User Interface notification or has been contacted by a Barracuda Technical Support Representative, the customer should contact support@barracuda[.]com to replace the ESG appliance. Barracuda is providing the replacement product to impacted customers at no cost.
We have notified customers impacted by this incident. If an ESG appliance is displaying a notification in the User Interface, the ESG appliance had indicators of compromise. If no notification is displayed, we have no reason to believe that the appliance has been compromised at this time. Again, only a subset of ESG appliances were impacted by this incident.