An ongoing cyber attack campaign has set its sights on Korean-speaking individuals by employing U.S. Military-themed document lures to trick them into running malware on compromised systems.
Cybersecurity firm Securonix is tracking the activity under the name STARK#MULE. The scale of the attacks is currently not known, and it’s not clear if any of these attack attempts turned out to be successful.
Based on the source and likely targets, these types of attacks are on par with past attacks stemming from typical North Korean groups such as APT37 as South Korea has historically been a primary target of the group, especially its government officials, security researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov said in a report shared with The Hacker News.
APT37, also known by the names Nickel Foxcroft, Reaper, Ricochet Chollima, and ScarCruft, is a North Korean nation-state actor that’s known to exclusively focus on targets in its southern counterpart, specifically those involved in reporting on North Korea and supporting defectors.
Attack chains mounted by the group have historically relied on social engineering to phish victims and deliver payloads such as RokRat onto target networks. That said, the adversarial collective has expanded its offensive arsenal with a variety of malware families in recent months, including a Go-based backdoor called AblyGo.
A notable trait of the new campaign is the use of compromised Korean e-commerce websites for staging payloads and command-and-control (C2) in an attempt to fly under the radar of security solutions installed on the systems.
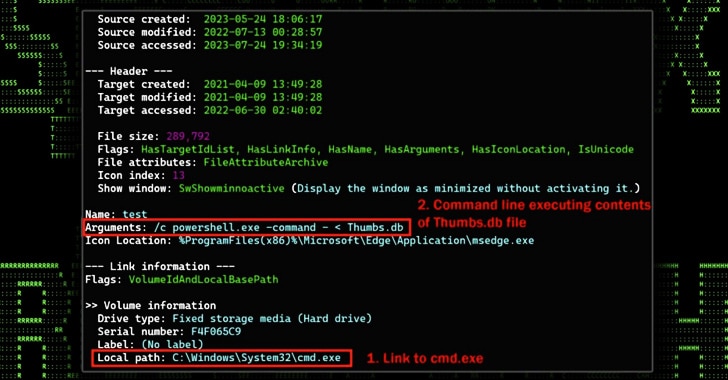
The phishing emails that act as the progenitor make use of U.S. Army recruitment messages to convince recipients into opening a ZIP archive file, which contains a shortcut file that appears under the guise of a PDF document.
The shortcut file, when launched, displays a decoy PDF, but also surreptitiously activates the execution of a rogue Thumbs.db file present in the archive file.
This file performs several functions which include downloading further stagers and leveraging schtasks.exe to establish persistence, the researchers explained.
Two of the next-stage modules – lsasetup.tmp and winrar.exe – are retrieved from a compromised e-commerce website named www.jkmusic.co[.]kr, the latter of which is used to extract and run the contents of lsasetup.tmp, an obfuscated binary that reaches out to a second e-commerce site named www.notebooksell[.]kr.
Once the connection was established, the attackers were able to acquire system details such as system MAC, Windows version, [and] IP address, the researchers said. Both websites are registered in Korea [and] only utilize the HTTP protocol.
The disclosure comes as APT37 has also been observed making use of CHM files in phishing emails impersonating security emails from financial institutes and insurance companies to deploy information-stealing malware and other binaries, according to the AhnLab Security Emergency Response Center (ASEC).
In particular, malware that targets specific users in Korea may include content on topics of interest to the user to encourage them to execute the malware, so users should refrain from opening emails from unknown sources and should not execute their attachments, ASEC said.
APT37 is one of the many North Korean state-sponsored groups that have drawn attention for executing attacks that are designed to perpetrate financial theft – including the recent attacks on Alphapo and CoinsPaid – and gather intelligence in pursuit of the regime’s political and national security objectives.
This also comprises the notorious Lazarus Group and its sub-clusters Andariel and BlueNoroff, with the actors leveraging a new backdoor dubbed ScoutEngine and a fully revamped version of a malware framework called MATA (MATAv5) in intrusions aimed at defense contractors in Eastern Europe in September 2022.
This sophisticated malware, completely rewritten from scratch, exhibits an advanced and complex architecture that makes use of loadable and embedded modules and plugins, Kaspersky said in its APT trends report for Q2 2023.
The malware leverages Inter-Process Communication (IPC) channels internally and employs a diverse range of commands, enabling it to establish proxy chains across various protocols, including within the victim’s environment.