Threat actors have been found deploying never-before-seen post-compromise implants in VMware’s virtualization software to seize control of infected systems and evade detection.
Google‘s Mandiant threat intelligence division referred to it as a “novel malware ecosystem” that impacts VMware ESXi, Linux vCenter servers, and Windows virtual machines, allowing attackers to maintain persistent access to the hypervisor as well as execute arbitrary commands.
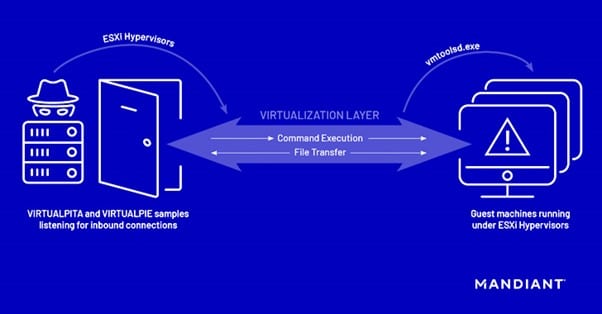
Die hyperjacking attacks, per the cybersecurity vendor, involved the use of malicious vSphere Installation Bundles (VIBs) to sneak in two implants, dubbed VIRTUALPITA and VIRTUALPIE, on the ESXi hypervisors.
“It is important to highlight that this is not an external remote code execution vulnerability; the attacker needs admin-level privileges to the ESXi hypervisor before they can deploy malware,” Mandiant researchers Alexander Marvi, Jeremy Koppen, Tufail Ahmed, and Jonathan Lepore said in an exhaustive two-part Bericht.
There is no evidence that a zero-day vulnerability was exploited to gain access to ESXi servers. That said, the use of trojanized VIBs, a software package format used to facilitate software distribution and virtual machine management, points to a new level of sophistication.
“The threat actor had prior access to the victim environments through attack techniques unrelated to VMware,” Marvi told The Hacker News. “With their established network access, they identified and stole VMware administrator credentials and used it to log into the ESXi servers and deploy the malicious VIB files.”
“This malware differs in that it supports remaining both persistent and covert, which is consistent with the goals of larger threat actors and APT groups who target strategic institutions with the intention of dwelling undetected for some time,” VMware disclosed.
While VIRTUALPITA comes with capabilities to execute commands as well as carry out file upload and download, VIRTUALPIE is a Python backdoor with support for command line execution, file transfer, and reverse shell features.
Also uncovered is a malware sample called VIRTUALGATE in Windows guest virtual machines, which is a C-based utility program that executes an embedded payload capable of using VMware’s virtual machine communication interface (VMCI) sockets to run commands on a guest virtual machine from a hypervisor host.
According to Marvi, the malware is said to have been deployed at fewer than ten organizations, although the number is expected to grow as companies begin to inspect their VMware infrastructure. Given the low infection count, it’s not clear if the attacks are targeting a specific sector at this point in time.
Mandiant also warned that the campaign’s techniques to get around traditional security controls by exploiting virtualization software represent a new attack surface that’s likely to be picked up by other hacker groups.
The attacks have been attributed to an uncategorized, emerging threat cluster codenamed UNC3886, whose motivation is likely to be espionage-driven considering the highly targeted nature of the intrusions. It further assessed with low confidence that UNC3886 has a China-nexus.
https://thehackernews.com/2022/09/new-malware-families-found-targeting.html