Amazon has seized domains used by the Russian APT29 hacking group in targeted attacks against government and military organizations to steal Windows credentials and data using malicious Remote Desktop Protocol connection files.
APT29, also known as “Cozy Bear” and “Midnight Blizzard,” is a Russian state-sponsored cyber-espionage group linked to Russia’s Foreign Intelligence Service (SVR).
Amazon clarifies that although the phishing pages APT29 used were made to appear as AWS domains, neither Amazon, nor credentials for its cloud platform were the direct targets of these attacks.
“Some of the domain names they used tried to trick the targets into believing the domains were AWS domains (they were not), but Amazon wasn’t the target, nor was the group after AWS customer credentials,” reads the announcement.
“Rather, APT29 sought its targets’ Windows credentials through Microsoft Remote Desktop.”
“Upon learning of this activity, we immediately initiated the process of seizing the domains APT29 was abusing which impersonated AWS in order to interrupt the operation.”
The threat actors are known for highly sophisticated attacks targeting governments, think tanks, and research institutions globally, often using phishing and malware to steal sensitive information.
Targeting organizations worldwide
Although APT29’s recent campaign had a significant impact in Ukraine, where it was first discovered, it was broad in scope, targeting multiple countries considered Russian adversaries.
Amazon notes that in this particular campaign, APT29 sent phishing emails to a much larger number of targets than they usually do, following the opposite approach of their typical “narrow targeting” strategy.
Ukraine’s Computer Emergency Response Team (CERT-UA) published an advisory about these “Rogue RDP” attachments to warn about the mass email activity, which they track under ‘UAC-0215.’
The messages used the topic of addressing ‘integration’ issues with Amazon and Microsoft services and implementing a ‘zero trust’ cybersecurity architecture (Zero Trust Architecture, ZTA).
The emails included RDP (Remote Desktop Protocol) connection files with names like “Zero Trust Security Environment Compliance Check.rdp” that automatically initiated connections to malicious servers when opened.
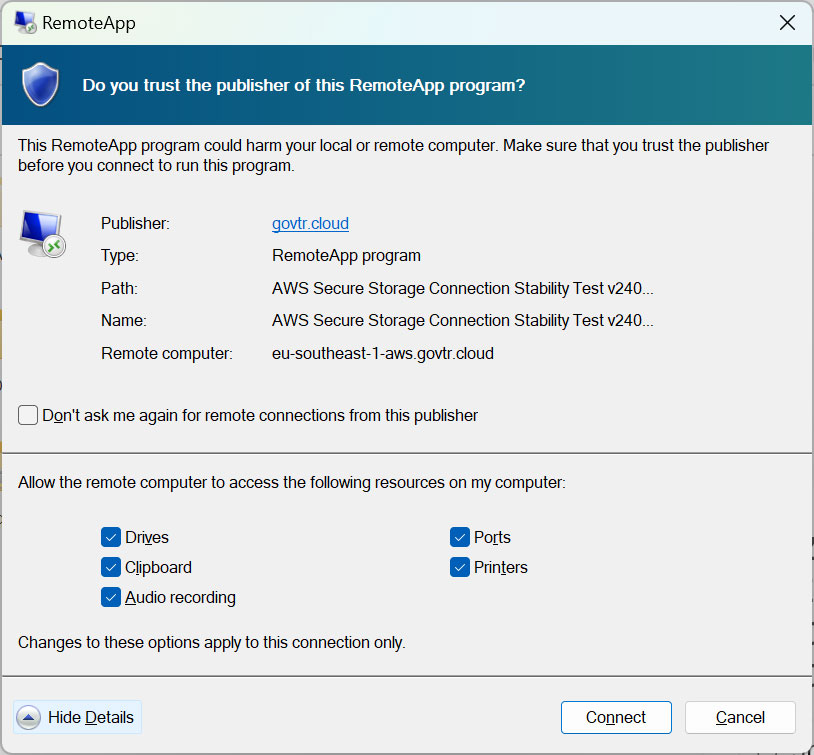
Quelle: BleepingComputer
As can be seen from the image of one of these RDP connection profiles above, they shared all local resources with the attacker-controlled RDP server, including:
- Local disks and files
- Network resources
- Printers
- COM ports
- Audio devices
- Clipboard
Moreover, UA-CERT says they can also be used to execute unauthorized programs or scripts on the compromised device.
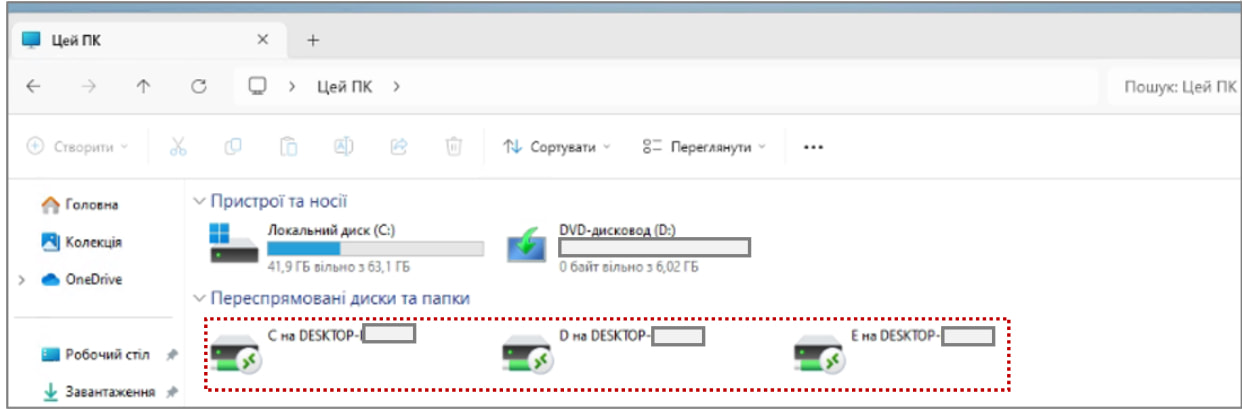
Source: CERT-UA
While Amazon says that this campaign was utilized to steal Windows credentials, as the target’s local resources were shared with the attacker’s RDP server, it would also have allowed the threat actors to steal data directly from the shared devices.
This includes all data stored on the target’s hard drives, Windows clipboard, and mapped network shares.
CERT-UA recommends scrutinizing network interaction logs for IP addresses shared in the IoC section of their bulletin to detect possible signs of attacks or a breach.
Additionally, the below measures are recommended for reducing the attack surface:
- Block’ .rdp’ files at the mail gateway.
- Prevent users from launching any ‘.rdp’ files when not needed.
- Configure firewall settings to restrict RDP connections from the mstsc.exe program to external network resources.
- Configure group policies to disable resource redirection via RDP (‘Remote Desktop Services’ -> ‘Remote Desktop Session Host’ -> ‘Device and Resource Redirection’ -> ‘Do not allow…’).
APT29 remains one of Russia’s most capable cyber threats, recently becoming known for using exploits only available to spyware vendors.
In the past year, it was revealed that the threat actors hacked important software vendors like TeamViewer, Microsoft, and Hewlett Packard Enterprise.
Western intelligence services warned earlier this month about APT29 leveraging Zimbra and JetBrains TeamCity servers flaws “en masse,” to breach important organizations worldwide.



