Over 28,000 people from Russia, Turkey, Ukraine, and other countries in the Eurasian region were impacted by a large-scale cryptocurrency-stealing malware campaign.
The malware campaign disguises itself as legitimate software promoted via YouTube videos and fraudulent GitHub repositories where victims download password-protected archives that initiate the infection.
According to cybersecurity firm Dr. Web, the campaign uses pirated office-related software, game cheats and hacks, and even automated trading bots to deceive users into downloading malicious files.
“In total, this malware campaign has affected more than 28,000 people, the vast majority of whom are residents of Russia,” said Dr. Web.
“Significant numbers of infections have also been observed in Belarus, Uzbekistan, Kazakhstan, Ukraine, Kyrgyzstan and Turkey.”
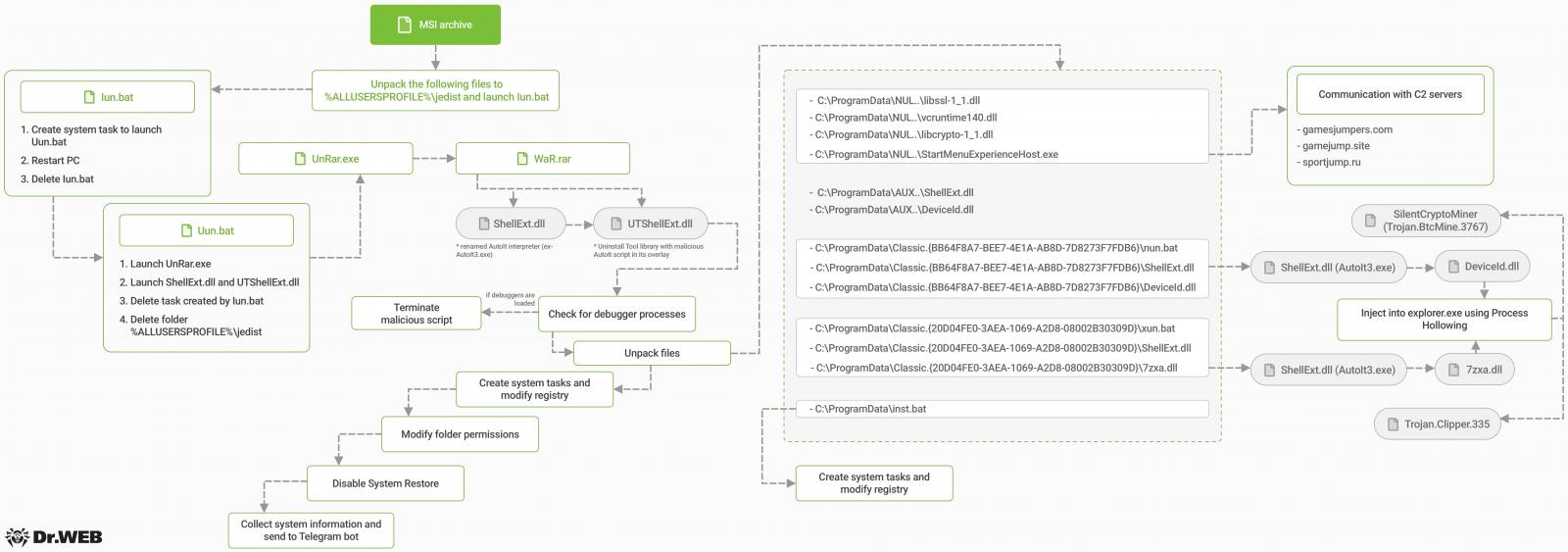
Infection chain
The infection begins with opening a self-extracting archive that evades antivirus scans when downloaded as it’s password-protected.
After the victim enters the provided password, the archive drops various obfuscated scripts, DLL files, and an AutoIT interpreter used to launch the digitally signed loader of the main payload.
The malware checks for the presence of debugging tools to see if it’s running on an analyst’s environment and terminates if any are found.
Next, it extracts the files required for the subsequent stages of the attack and then uses the Image File Execution Options (IFEO) technique to modify the Windows Registry for persistence.
In short, it hijacks legitimate Windows system services as well as Chrome’s and Edge’s update processes with malicious ones, so the malware files are executed upon the launch of these processes.
The Windows Recovery Service is disabled, and the “delete” and “modify” permissions on the malware’s files and folders are revoked to prevent attempted cleanups.
From there on, the Ncat network utility is employed to establish communication with the command and control (C2) server.
The malware can also collect system information, including running security processes, which it exfiltrates via a Telegram bot.
Source: Dr. Web
Financial impact
The campaign delivers two key payloads onto the victims’ machines. The first one is “Deviceld.dll,” a modified .NET library used to execute the SilentCryptoMiner, which mines cryptocurrency using the victim’s computational resources.
The second payload is “7zxa.dll,” a modified 7-Zip library that acts as a clipper, monitoring the Windows clipboard for copied wallet addresses and replacing them with addresses under the attacker’s control.
Dr. Web did not specify in the report the potential mining profits from the 28,000 infected machines but found that the clipper alone had hijacked $6,000 worth of transactions, diverting the amount onto the attacker’s addresses.
To avoid unexpected financial losses, only download software from the project’s official website and block or skip promoted results on Google Search.
Furthermore, be careful of shared links on YouTube or GitHub, as the legitimacy of these platforms does not guarantee the download destination’s safety.



