UK’s National Cyber Security Centre (NCSC) has published an analysis of a Linux malware named “Pigmy Goat” created to backdoor Sophos XG firewall devices as part of recently disclosed attacks by Chinese threat actors.
Last week, Sophos published a series of reports dubbed “Pacific Rim” that detailed five-year attacks by Chinese threat actors on edge networking devices.
One of the custom malware used in these attacks is a rootkit that closely impersonated Sophos product file naming conventions.
The malware, which is designed for compromising network devices, features advanced persistence, evasion, and remote access mechanisms and has a rather complex code structure and execution paths.
Although the NCSC report does not attribute the observed activity to known threat actors, it underlines similar techniques, tactics, and procedures (TTPs) to the “Castletap” malware, which Mandiant has associated with a Chinese nation-state actor.
Sophos has also disclosed the same malware in its Pacific Rim report, stating the rootkit was used in 2022 attacks linked to a Chinese threat actor known as “Tstark.”
“X-Ops identified two copies of libsophos.so, both deployed using CVE-2022-1040 — one on a high-level government device and the other on a technology partner to the same government department,” shared Sophos.
A goat in the firewall
The ‘Pygmy Goat’ malware is an x86-32 ELF shared object (‘libsophos.so’) providing threat actors with backdoor access to Linux-based networking devices such as the Sophos XG firewalls.
It uses the LD_PRELOAD environment variable to load its payload into the SSH daemon (sshd), allowing it to hook into the daemon’s functions and override the accept function, which processes incoming connections.
Pygmy Goat monitors SSH traffic for a specific sequence of “magic bytes” in the first 23 bytes of each package.
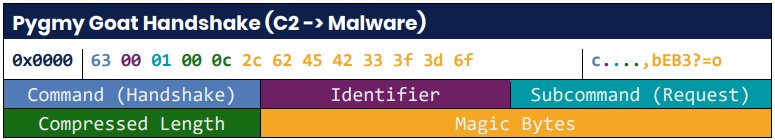
Source: NCSC
Once that sequence is found, the connection is identified as a backdoor session, and the malware redirects it to an internal Unix socket (/tmp/.sshd.ipc) to establish communication with its Command and Control (C2).
The malware also listens on a raw ICMP socket, waiting for packets with an AES-encrypted payload that holds IP and port information for C2 communication, which triggers a connect-back attempt over TLS.
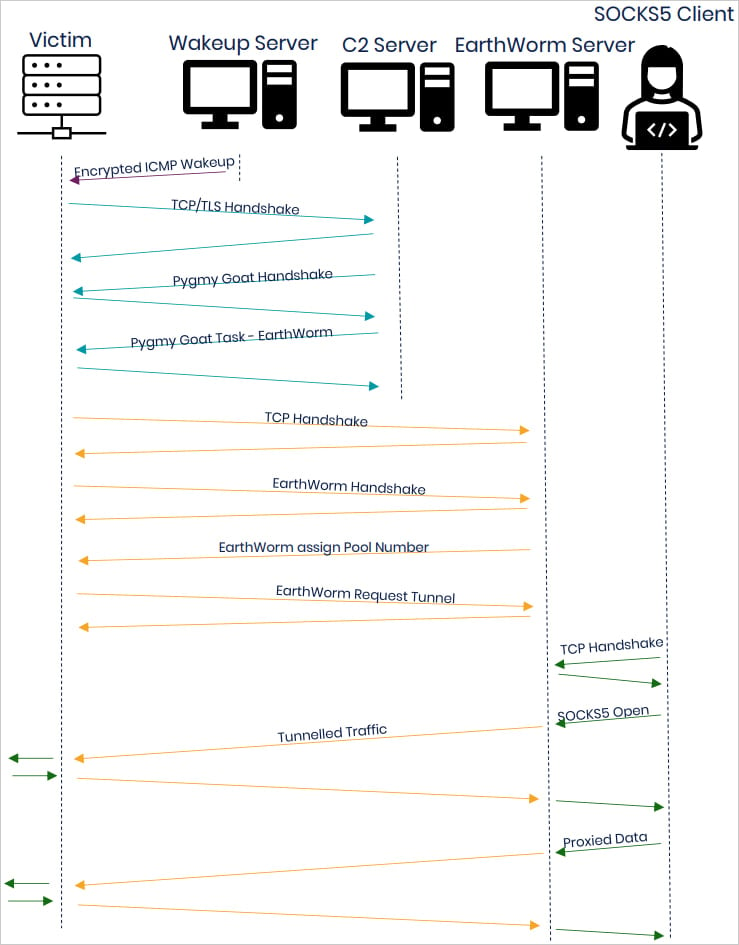
Source: NCSC
Pygmy Goat communicates with the C2 over TLS, using an embedded certificate mimicking Fortinet’s “FortiGate” CA, a potential cover for blending into network environments where Fortinet devices are common.
When an SSH connection is established, a fake handshake with pre-set responses is triggered to create a false image of legitimacy on network monitors.
The C2 server can send Pygmy Goat commands for execution on the device, including the following:
- Open either a /bin/sh or /bin/csh shell.
- Start capturing network traffic via libpcap, forwarding results to C2.
- Manage cron tasks using BusyBox to schedule activities when the actor isn’t actively connected.
- Use the EarthWorm open-source toolkit to establish a SOCKS5 reverse proxy, allowing C2 traffic to traverse the network unseen.
Detection and defense
The NCSC report contains file hashes and YARA and Snort rules that detect the magic byte sequences and fake SSH handshake, so defenders can use them to catch Pygmy Goat activity early on.
Additionally, manual checks for /lib/libsophos.so, /tmp/.sshd.ipc, /tmp/.fgmon_cli.ipc, /var/run/sshd.pid, and /var/run/goat.pid, can reveal an infection.
It is also advisable to set up monitoring for encrypted payloads in ICMP packets and use of ‘LD_PRELOAD’ in the environment of the ‘ssdh’ process, which is unusual behavior that may indicate Pygmy Goat activity.



