A relatively unknown advanced persistent threat (APT) group named ‘GoldenJackal’ has been targeting government and diplomatic entities in Asia since 2019 for espionage.
The threat actors have maintained a low profile for stealthiness, carefully selecting their victims and keeping the number of attacks at a minimum to reduce the likelihood of exposure.
Kaspersky has been tracking GoldenJackal since 2020, and today reports that the threat actors have had notable activity in Afghanistan, Azerbaijan, Iran, Iraq, Pakistan, and Turkey.
“GoldenJackal is an APT group, active since 2019, that usually targets government and diplomatic entities in the Middle East and South Asia,” explains Kaspersky.
“Despite the fact that they began their activities years ago, this group is generally unknown and, as far as we know, has not been publicly described.”
The infection vectors of the APT are unknown. However, the researchers have observed signs of phishing operations with malicious documents that employ the remote template injection technique to exploit the Microsoft Office Follina vulnerability.
Additionally, Kaspersky has seen a case of trojanized ‘Skype for Business’ installers that drop a trojan alongside a legitimate copy of the software.
While Kaspersky’s analysts have noticed code and TTP (techniques, tactics, and procedures) similarities with Turla, they track GoldenJackal as a separate activity cluster.
Rich custom ‘Jackal’ toolset
According to Kaspersky, GoldenJackal employs a set of custom .NET malware tools that provide various functions, including credential dumping, data stealing, malware loading, lateral movement, file exfiltration, and more.
The primary payload used first to infect a system is ‘JackalControl,’ which gives the attackers remote control over the infected computer.
The malware can be run as a program or a Windows service and can establish persistence by adding Registry keys, Windows scheduled tasks, or Windows services.
It receives encoded commands from the C2 server via HTTP POST requests, which concern the execution of arbitrary programs, exfiltration of files, or fetching additional payloads from the C2.
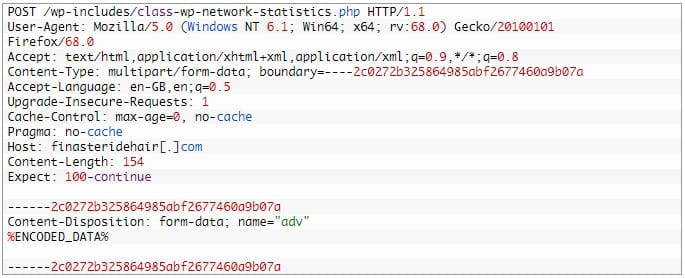
The second tool used by the hackers is ‘JackalSteal,’ an implant devoted to data exfiltration from all logical drives on the compromised computer, including remote shares and even newly connected USB drives.
The attackers can execute the stealer with arguments determining the targeted file types, paths, sizes, when files were last used, and exclude specific paths that security tools might monitor.
All files matching the set parameters are encrypted using AES, RSA, or DES, then compressed with GZIP, and eventually transmitted to the C2 server.
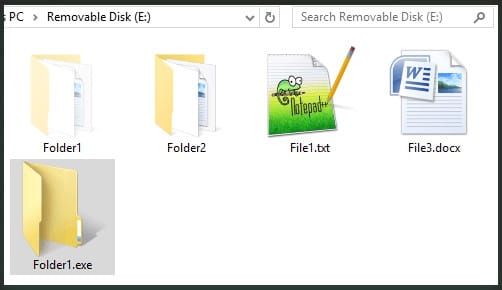
The third tool in GoldenJackal’s arsenal is ‘JackalWorm,’ which infects USB drives to spread on potentially other valuable computers.
“When the malware detects a removable USB storage device, it will copy itself onto it,” reads the Kaspersky report.
“It will create a copy of itself on the drive root using the same directory name and change the directory’s attribute to “hidden.” This will result in the actual directory being hidden and replaced with a copy of the malware with the directory name.”
To obfuscate its nature and trick the victim into executing it, ‘JackalWorm’ uses a Windows directory icon on the removable drive.
If that happens, the worm will infect the host system, establish persistence by creating a scheduled task, and then wipe its copy from the USB drive.
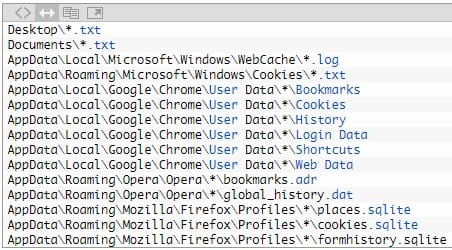
The fourth tool used by the Golden Jackal APT is ‘JacklPerInfo,’ a basic system information collector with the additional capabilities of identifying and exfiltrating browsing history and credentials stored in web browsers.
Serving like a typical info-stealer malware, JacklPerInfo can also exfiltrate files from the Desktop, Documents, Downloads, and AppDataRoamingMicrosoftWindowsRecent directories.
The fifth and final malware tool presented in Kaspersky’s report is the ‘JackalScreenWatcher,’ which is used for snapping screenshots on the infected device.
The operators can specify the resolution and image-capturing time intervals, and the tool will send the media to the C2 via HTTP POST requests in the form of encrypted payloads.
In conclusion, GoldenJackal has been carefully using an extensive set of custom tools against a limited number of victims to carry out what Kaspersky believes are long-term espionage operations.
Although few things are known about the APT’s operational tactics, the diversity in the observed infection chains combined with highly capable malware tools leaves no doubt that this is a sophisticated threat actor.


