The new ‘Helldown’ ransomware operation is believed to target vulnerabilities in Zyxel firewalls to breach corporate networks, allowing them to steal data and encrypt devices.
French cybersecurity firm Sekoia is reporting this with medium confidence based on recent observations of Helldown attacks.
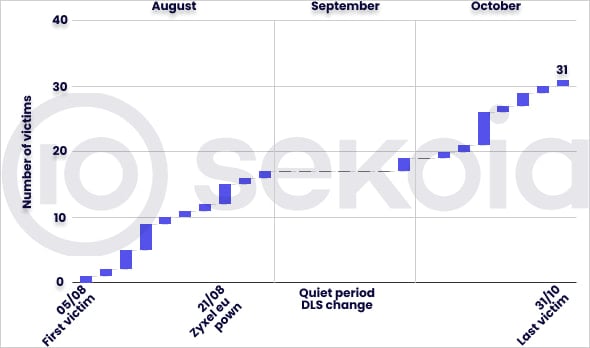
Although not among the major players in the ransomware space, Helldown has quickly grown since its launch over the summer, listing numerous victims on its data extortion portal.
Source: Sekoia
Helldown discovery and overview
Helldown was first documented by Cyfirma on August 9, 2024, and then again by Cyberint on October 13, both briefly describing the new ransomware operation.
The first report of a Linux variant of the Helldown ransomware targeting VMware files came from 360NetLab security researcher Alex Turing on October 31.
The Linux variant features code to list and kill VMs to encrypt images, however, its functions are only partially invoked, indicating that it might still be under development.
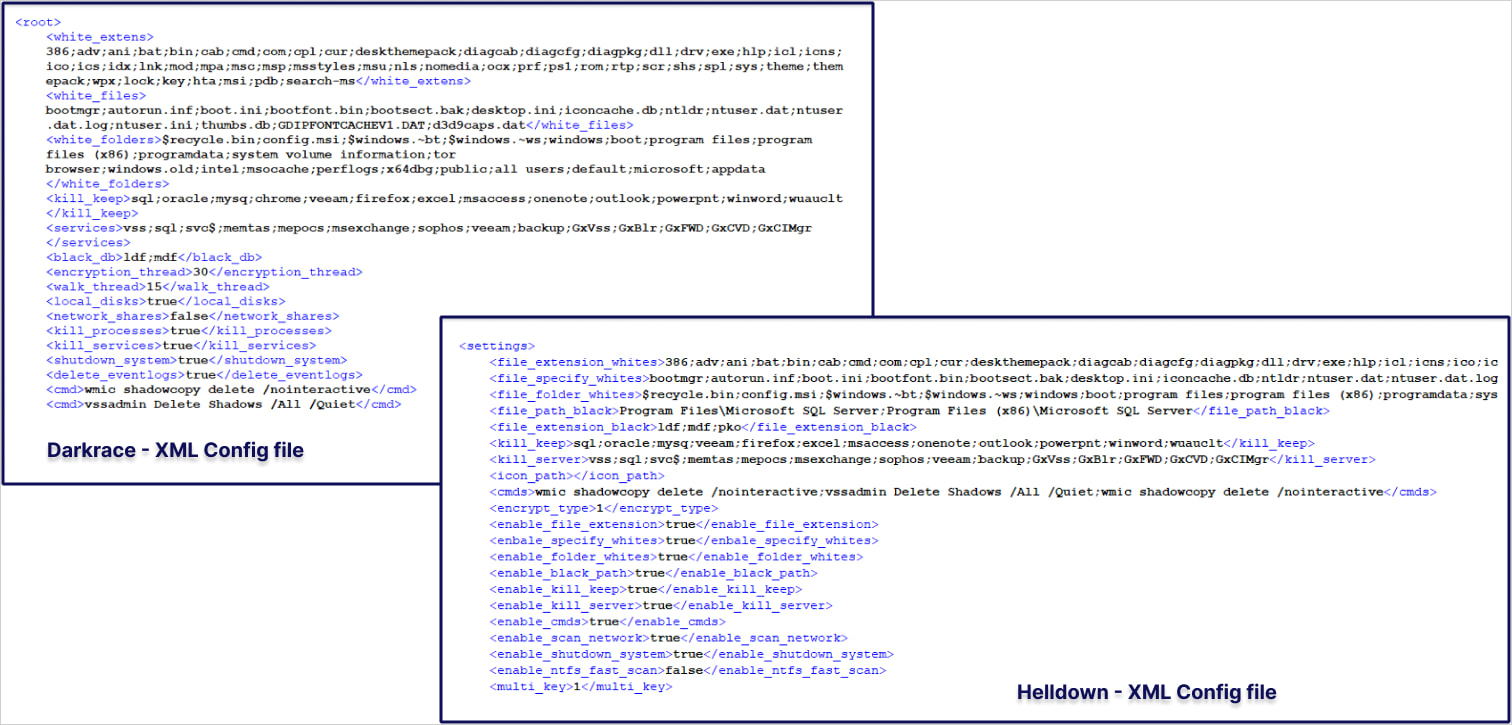
Sekoia reports that Helldown for Windows is based on the leaked LockBit 3 builder and features operational similarities to Darkrace and Donex. However, no definitive connection could be made based on the available evidence.
Source: Sekoia
As of November 7, 2024, the threat group listed 31 victims on its recently-renewed extortion portal, primarily small and medium-sized firms based in the United States and Europe. As of today, the number has decreased to 28, potentially indicating some had paid a ransom.
Sekoia says Helldown isn’t as selective in the data it steals as other groups following more efficient tactics and publishes large data packs on its website, reaching up to 431GB in one instance.
One of the victims listed is Zyxel Europe, a networking and cybersecurity solutions provider.
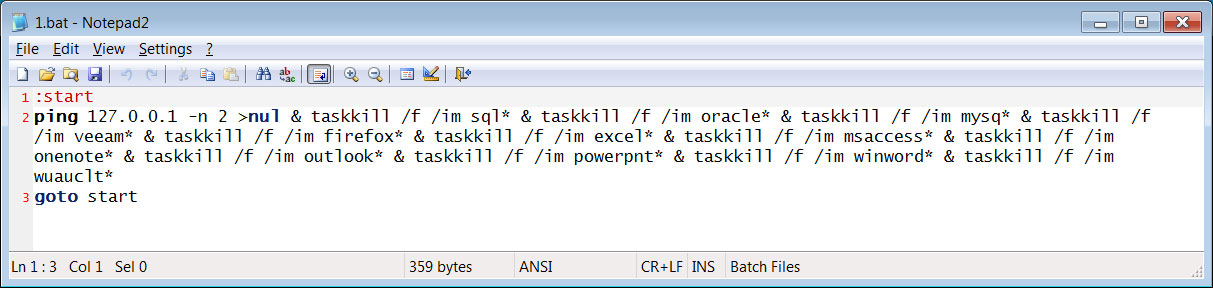
The group’s encryptors do not appear very advanced, with the threat actors utilizing batch files to end tasks rather than incorporating this functionality directly into the malware.
Source: BleepingComputer
When encrypting files, the threat actors will generate a random victim string, such as “FGqogsxF,” which will be used as the extension for encrypted files. The ransom note also uses this victim string in its filename, like “Readme.FGqogsxF.txt”.
Source: BleepingComputer
Evidence pointing to Zyxel exploitation
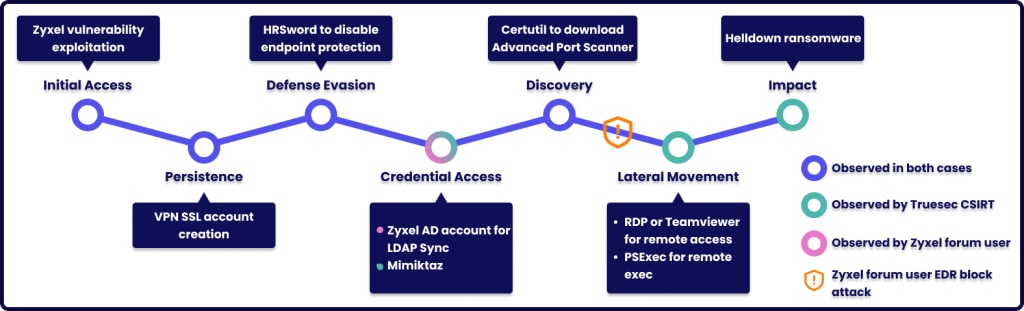
Working its way from a Zyxel Europe lead, Sekoia found that at least eight victims listed on the Helldown website used Zyxel firewalls as IPSec VPN access points at the time of their breach.
Next, Sekoia noticed that a Truesec report from November 7 mentions the use of a malicious account named ‘OKSDW82A’ in Helldown attacks and also a configuration file (‘zzz1.conf’) used as part of an attack targeting MIPS-based devices, possibly Zyxel firewalls.
The threat actors used this account to establish a secure connection via SSL VPN into the victim’s networks, access domain controllers, move laterally, and turn off endpoint defenses.
By investigating further, Sekoia found reports of the creation of suspicious user account ‘OKSDW82A’ and configuration file ‘zzz1.conf’ on Zyxel forums, where the device’s admins reported they were using firmware version 5.38.
Source: Sekoia
Based on the version, Sekoia’s researchers hypothesize that Helldown might be using CVE-2024-42057, a command injection in IPSec VPN that allows an unauthenticated attacker to execute OS commands with a crafted long username in User-Based-PSK mode.
In addition, Sekoia also considers a separate undocumented vulnerability on Zyxel, the details of which it shared with the vendor’s PSIRT.
CVE-2024-42057 was fixed on September 3 with the release of firmware version 5.39, and exploitation details have not been made public as of yet, so Helldown is suspected of having access to private n-day exploits.
Furthermore, Sekoia discovered payloads uploaded to VirusTotal from Russia between October 17 and 22, but the payload was incomplete.
“It contains a base64-encoded string which, when decoded, reveals an ELF binary for the MIPS architecture,” explains Sekoia researcher Jeremy Scion.
“The payload, however, appears to be incomplete. Sekoia assess with medium confidence this file is likely connected to the previously mentioned Zyxel compromise.”
BleepingComputer contacted Zyxel with questions about these attacks but has not received a response at this time.
Update 11/21 – Zyxel has issued a bulletin addressing the concerns that arose from Sekoia’s report, assuring customers that firmware version 5.39 is protected against those attacks.


.png)

