A relatively new ransomware operation named Interlock attacks organizations worldwide, taking the unusual approach of creating an encryptor to target FreeBSD servers.
Launched at the end of September 2024, Interlock has since claimed attacks on six organizations, publishing stolen data on their data leak site after a ransom was not paid. One of the victims is Wayne County, Michigan, which suffered a cyberattack at the beginning of October.
Not much is known about the ransomware operation, with some of the first information coming from incident responder Simo in early October, who found a new backdoor [VirusTotal] deployed in an Interlock ransomware incident.
Soon after, cybersecurity researcher MalwareHunterTeam found what was believed to be a Linux ELF encryptor [VirusTotal] for the Interlock operation. Sharing the sample with BleepingComputer, we attempted to test it on a virtual machine, where it immediately crashed.
Examining the strings within the executable indicated that it was compiled specifically for FreeBSD, with the Linux “File” command further confirming it was compiled on FreeBSD 10.4.
interlock.elf: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), statically linked, BuildID[sha1]=c7f876806bf4d3ccafbf2252e77c2a7546c301e6, for FreeBSD 10.4, FreeBSD-style, not strippedHowever, even when testing the sample on a FreeBSD virtual machine, BleepingComputer was unable to get the sample to properly execute.
While it is common to see Linux encryptors created to target VMware ESXi servers and virtual machines, it is rare to see ones created for FreeBSD. The only other ransomware operation known to have created FreeBSD encryptors is the now-defunct Hive ransomware operation, which was disrupted by the FBI in 2023.
This week, researchers from cybersecurity firm Trend Micro shared on X that they found an additional sample of the FreeBSD ELF encryptor [VirusTotal] and a sample of the operation’s Windows encryptor [VirusTotal].
Trend Micro further said that the threat actors likely created a FreeBSD encryptor as the operating system is commonly used in critical infrastructure, where attacks can cause widespread disruption.
“Interlock targets FreeBSD as it’s widely utilized in servers and critical infrastructure. Attackers can disrupt vital services, demand hefty ransoms, and coerce victims into paying,” explains Trend Micro.
It goes without saying that the Interlock ransomware operation is not linked to the cryptocurrency token of the same name.
The Interlock ransomware
While BleepingComputer could not get the FreeBSD encryptor working, the Windows version ran without a problem on our virtual machine.
According to Trend Micro, the Windows encryptor will clear Windows event logs, and if self-deletion is enabled, will use a DLL to delete the main binary using rundll32.exe.
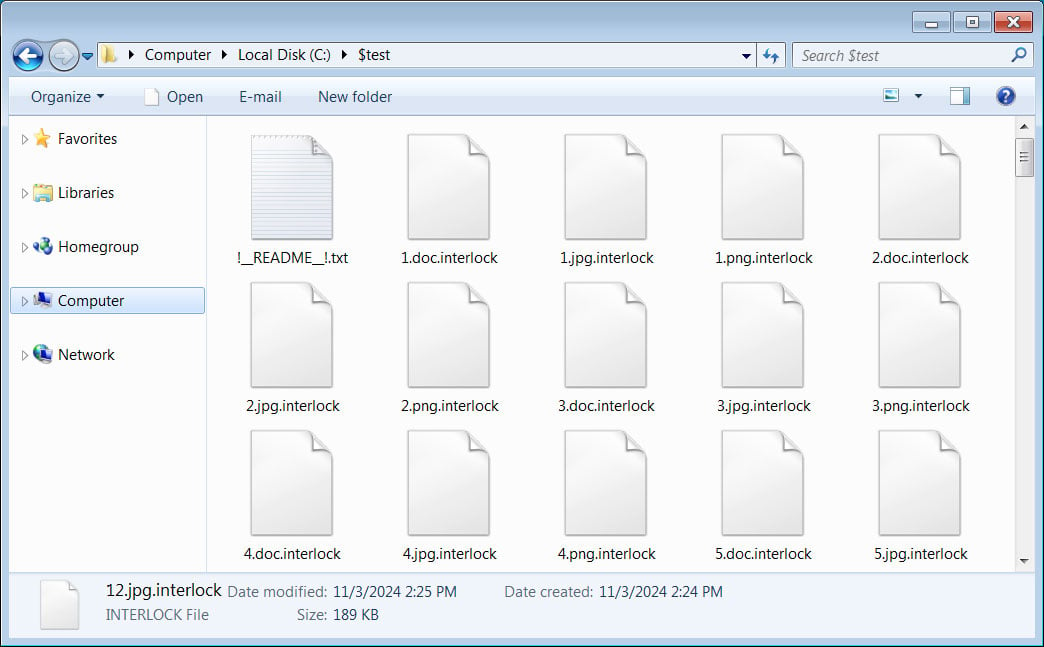
When encrypting files, the ransomware will append the .interlock extension to all encrypted file names, and create a ransom note in each folder.
Quelle: BleepingComputer
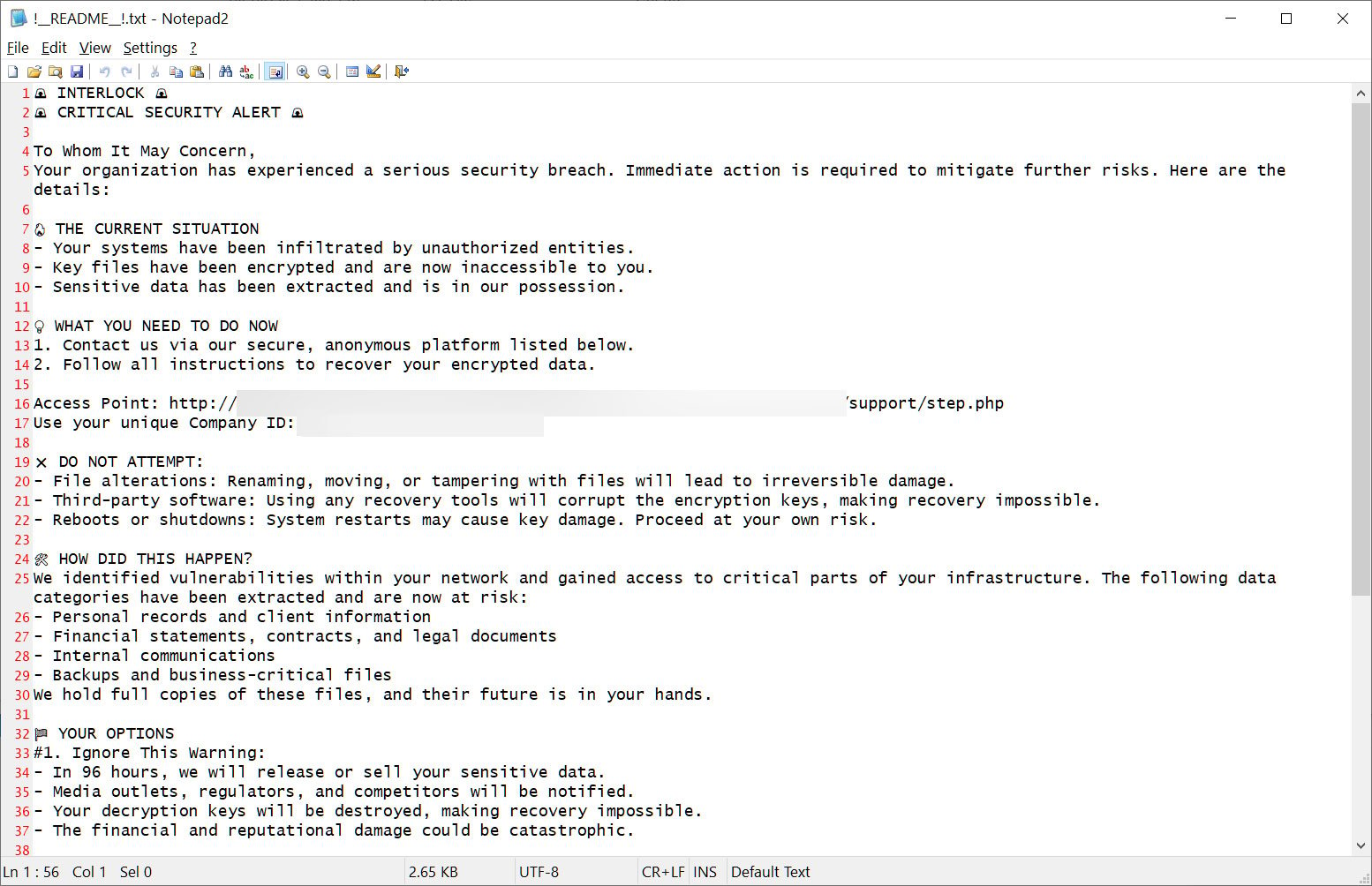
This ransom note is named !__README__!.txt and briefly describes what happened to the victim’s files, makes threats, and links to the Tor negotiation and data leak sites.
Quelle: BleepingComputer
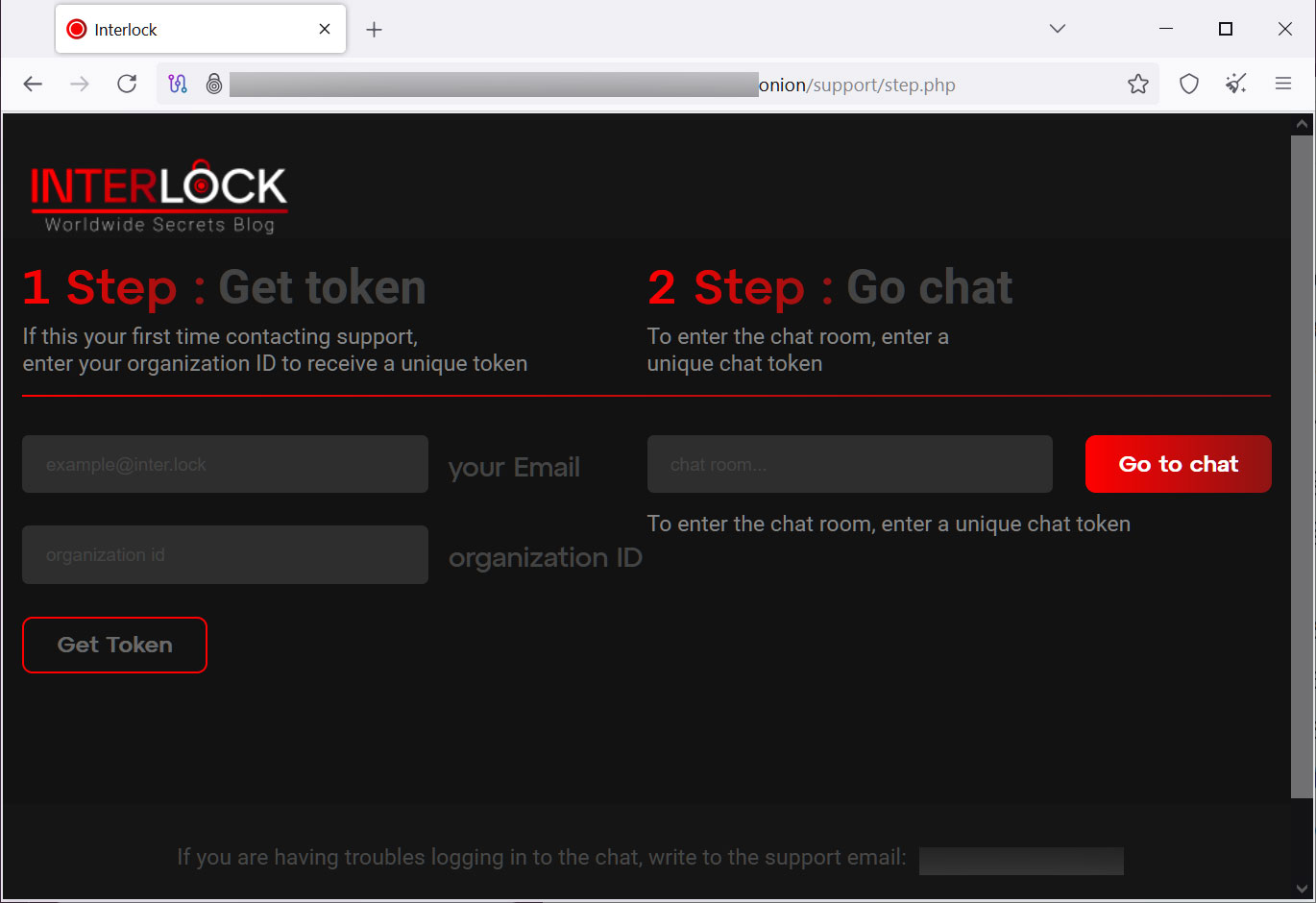
Each victim has a unique “Company ID” that is used along with an email address to register on the threat actor’s Tor negotiation site. Like many other recent ransomware operations, the victim-facing negotiation site just includes a chat system that can be used to communicate with the threat actors.
Trend Micro further said that the threat actors likely created a FreeBSD encryptor as the operating system is commonly used in critical infrastructure, where attacks can cause widespread disruption.
“Interlock targets FreeBSD as it’s widely utilized in servers and critical infrastructure. Attackers can disrupt vital services, demand hefty ransoms, and coerce victims into paying,” explains Trend Micro.
It goes without saying that the Interlock ransomware operation is not linked to the cryptocurrency token of the same name.
The Interlock ransomware
While BleepingComputer could not get the FreeBSD encryptor working, the Windows version ran without a problem on our virtual machine.
According to Trend Micro, the Windows encryptor will clear Windows event logs, and if self-deletion is enabled, will use a DLL to delete the main binary using rundll32.exe.
When encrypting files, the ransomware will append the .interlock extension to all encrypted file names, and create a ransom note in each folder.

Quelle: BleepingComputer
This ransom note is named !__README__!.txt and briefly describes what happened to the victim’s files, makes threats, and links to the Tor negotiation and data leak sites.

Quelle: BleepingComputer
Each victim has a unique “Company ID” that is used along with an email address to register on the threat actor’s Tor negotiation site. Like many other recent ransomware operations, the victim-facing negotiation site just includes a chat system that can be used to communicate with the threat actors.
When conducting attacks, Interlock will breach a corporate network and steal data from servers while spreading laterally to other devices. When done, the threat actors deploy the ransomware to encrypt all of the files on the network.
The stolen data is used as part of a double-extortion attack, where the threat actors threaten to publicly leak it if a ransom is not paid.
BleepingComputer has learned that the ransomware operation demands ransoms ranging from hundreds of thousands of dollars to millions, depending on the size of the organization.
Trend Micro further said that the threat actors likely created a FreeBSD encryptor as the operating system is commonly used in critical infrastructure, where attacks can cause widespread disruption.
“Interlock targets FreeBSD as it’s widely utilized in servers and critical infrastructure. Attackers can disrupt vital services, demand hefty ransoms, and coerce victims into paying,” explains Trend Micro.
It goes without saying that the Interlock ransomware operation is not linked to the cryptocurrency token of the same name.
The Interlock ransomware
While BleepingComputer could not get the FreeBSD encryptor working, the Windows version ran without a problem on our virtual machine.
According to Trend Micro, the Windows encryptor will clear Windows event logs, and if self-deletion is enabled, will use a DLL to delete the main binary using rundll32.exe.
When encrypting files, the ransomware will append the .interlock extension to all encrypted file names, and create a ransom note in each folder.

Quelle: BleepingComputer
This ransom note is named !__README__!.txt and briefly describes what happened to the victim’s files, makes threats, and links to the Tor negotiation and data leak sites.

Quelle: BleepingComputer
Each victim has a unique “Company ID” that is used along with an email address to register on the threat actor’s Tor negotiation site. Like many other recent ransomware operations, the victim-facing negotiation site just includes a chat system that can be used to communicate with the threat actors.