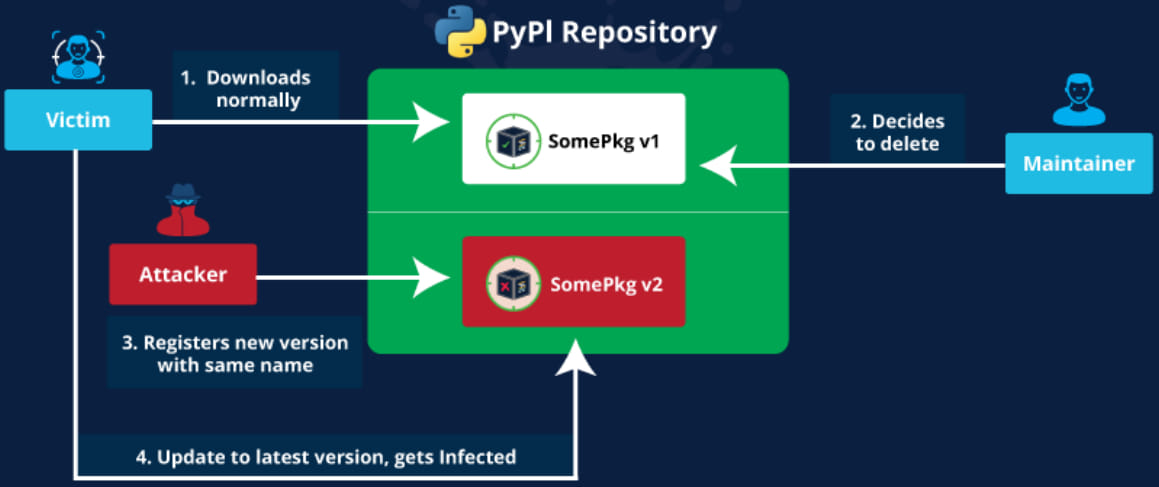
Threat actors are utilizing an attack called “Revival Hijack,” where they register new PyPi projects using the names of previously deleted packages to conduct supply chain attacks.
The technique “could be used to hijack 22K existing PyPI packages and subsequently lead to hundreds of thousands of malicious package downloads,” the researchers say.
Hijacking popular projects
“Revival Hijack” is an attack vector that involves registering a new project with the name of a package that has been removed from the PyPI platform. By doing so, a threat actor could push malicious code to developers pulling updates.
The attack is possible because PyPI makes immediately available for registration the names of deleted Python projects.
Source: JFrog
Developers who decide to delete a project from PyPI only receive a warning about the potential consequences, including the Revival Hijack attack scenario.
“Deleting this project will make the project name available to any other PyPI user,” cautions the dialog.
“This user will be able to make new releases under this project name, so long as the distribution filenames do not match filenames from a previously released distribution.”
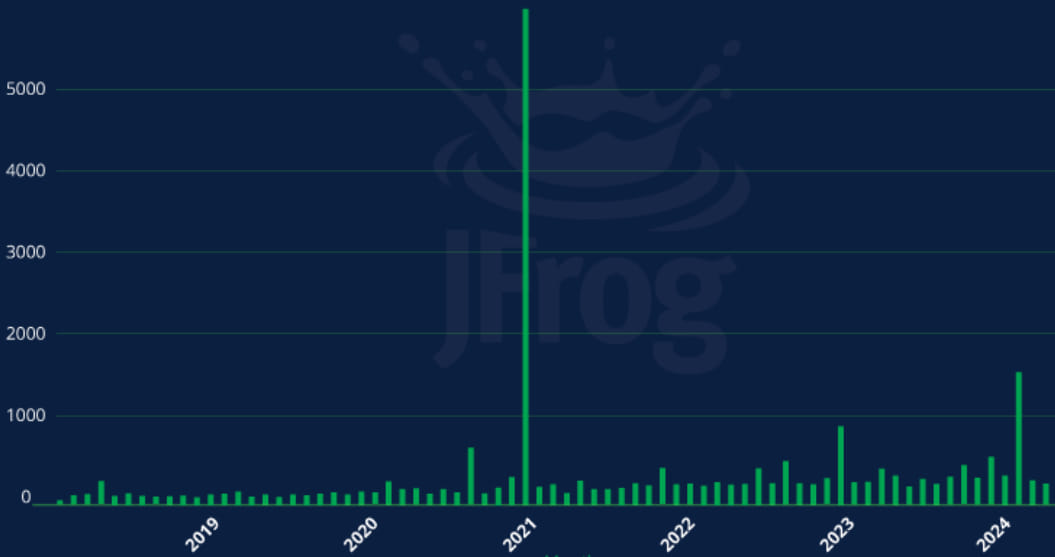
According to researchers at JFrog, a software supply chain platform, there are more than 22,000 deleted packages on PyPI that are vulnerable to the Revival Hijack attack, and some of them quite popular.
The researchers say that the monthly average of packages deleted on PyPI is 309, indicating a steady stream of fresh opportunities for attackers.
Source: JFrog
JFrog says that a developer may decide to remove their package for a variety of reasons that range from the script no longer being needed to re-writing a tool and publishing it under a new name.
In some cases, the package becomes redundant because its functionality is introduced in official libraries or built-in APIs.
The case of “pingdomv3”
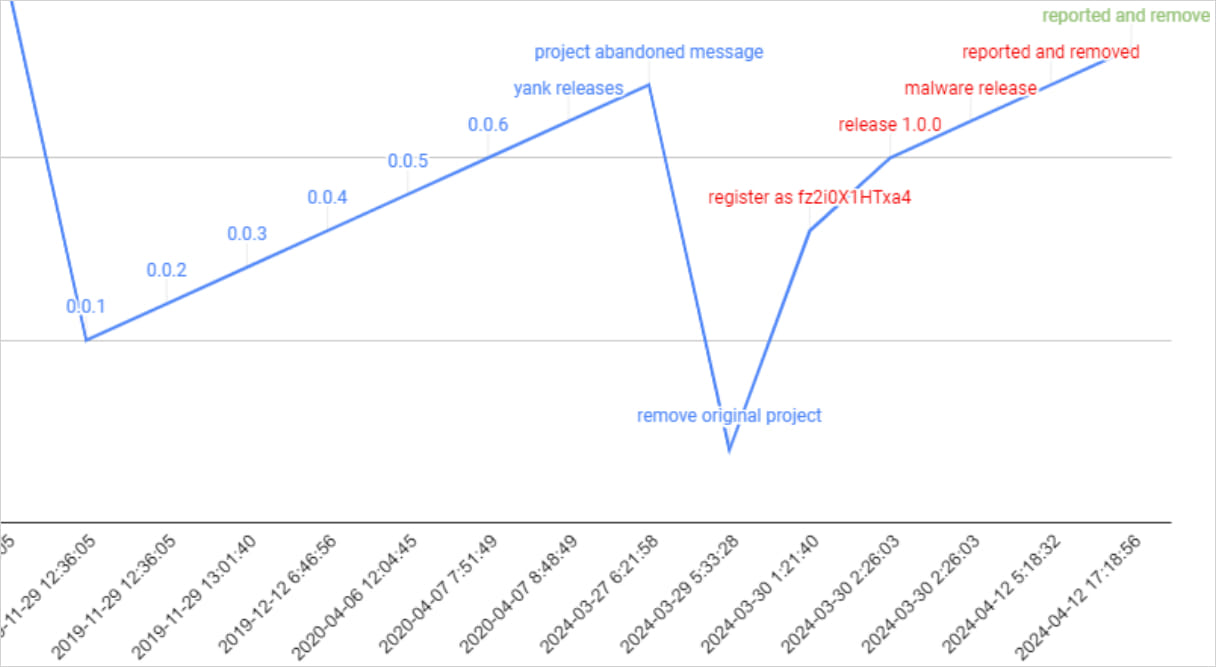
In mid-April, JFrog observed Revival Hijack leveraged in the wild, when a threat actor targeted the “pingdomv3” – an implementation of the Pingdom API website monitoring service.
The package was deleted on March 30 but a new developer hijacked the name and published an update on the same day, indicating that the attackers knew about the issue.
In a subsequent update, the package included a Python trojan that was obfuscated using Base64 and targeted Jenkins CI/CD environments.
Source: JFrog
JFrog leaps to the rescue
JFrog researchers took action to mitigate the risk of Revival Hijack attacks by creating new Python projects with the names of most popular already deleted packages.
JFrog explains that PyPI maintains a non-public blocklist that prevents certain names from being registered on new projects, but most deleted packages don’t make it on that list.
This led the security firm to take indirect action to mitigate the “Revival Hijack” threat and registered the most popular of the deleted/vulnerable packages under an account named security_holding.
The abandoned packages are empty, and the researchers changed the version numbers to 0.0.0.1, to make sure that active users don’t pull an update.
This action essentially reserves the package names and prevents malicious actors from hijacking them for nefarious purposes.
Three months later, JFrog noticed that the packages in their repository had close to 200,000 downloads from automated scripts and user mistypes.
The case of “Revival Hijack” is far more dangerous than the standard typosquatting attacks on PyPI, as users pulling an update for their selected projects don’t make a mistake.
To mitigate the threat, users and organizations can use package pinning to stay on specified, known to be trustworthy versions, verify package integrity, audit its contents, and look out for changes in package ownership or atypical update activity.




