Forty new variants of the TrickMo Android banking trojan have been identified in the wild, linked to 16 droppers and 22 distinct command and control (C2) infrastructures, with new features designed to steal Android PINs.
This is being reported by Zimperium, following an earlier report by Cleafy that looked into some, but not all variants currently in circulation.
TrickMo was first documented by IBM X-Force in 2020, but it is thought to have been used in attacks against Android users since at least September 2019.
Fake lock screen steals Android PINs
Key features of the new TrickMo version include one-time password (OTP) interception, screen recording, data exfiltration, remote control, and more.
The malware attempts to abuse the powerful Accessibility Service permission to grant itself additional permissions and tap on prompts automatically as needed.
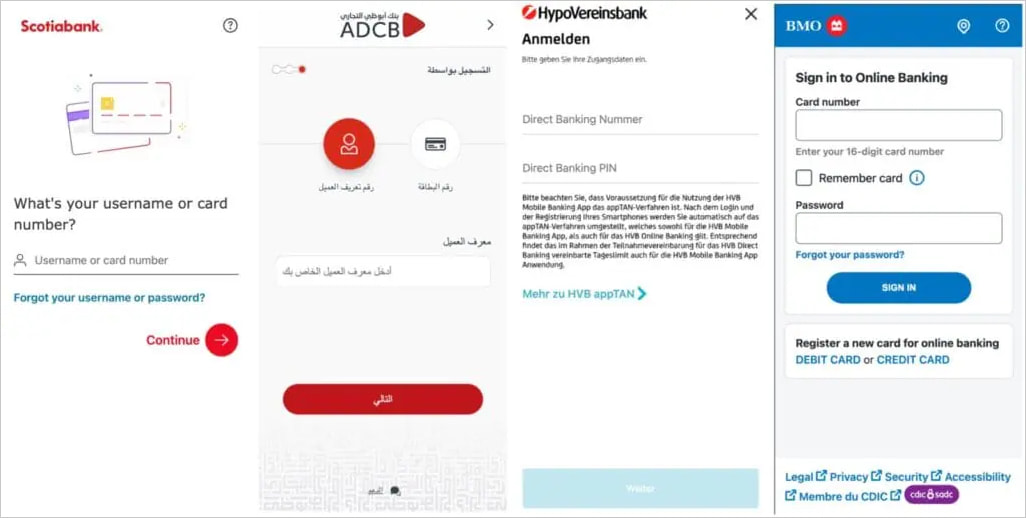
As a banking trojan, it serves users overlays of phishing login screens to various banks and financial institutes to steal their account credentials and enable the attackers to perform unauthorized transactions.
Source: Zimperium
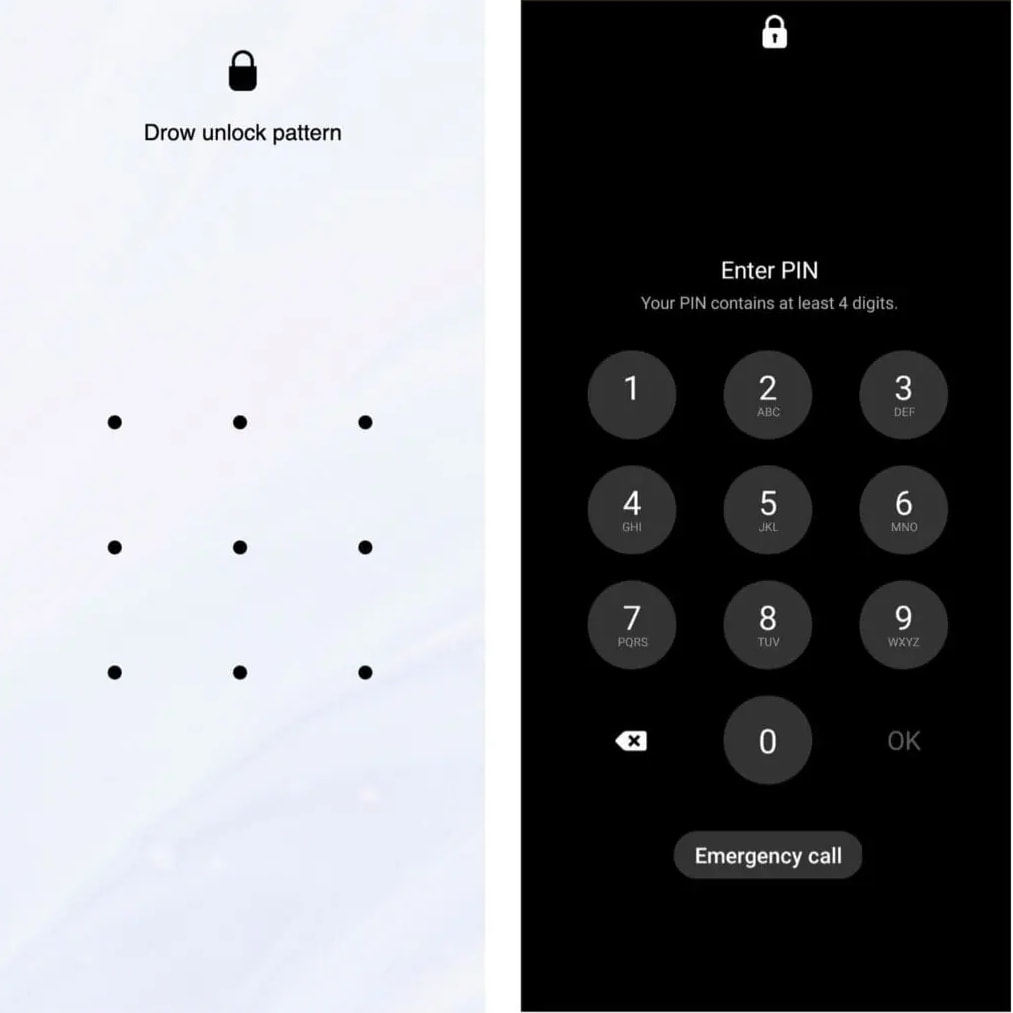
Zimperium analysts dissecting these new variants also report a new deceptive unlock screen mimicking the real Android unlock prompt, designed to steal the user’s unlock pattern or PIN.
Fake lock screen steals Android PINs
Key features of the new TrickMo version include one-time password (OTP) interception, screen recording, data exfiltration, remote control, and more.
The malware attempts to abuse the powerful Accessibility Service permission to grant itself additional permissions and tap on prompts automatically as needed.
As a banking trojan, it serves users overlays of phishing login screens to various banks and financial institutes to steal their account credentials and enable the attackers to perform unauthorized transactions.

Source: Zimperium
Zimperium analysts dissecting these new variants also report a new deceptive unlock screen mimicking the real Android unlock prompt, designed to steal the user’s unlock pattern or PIN.
Source: Zimperium
Stealing the PIN allows the attackers to unlock the device when it’s not actively monitored, possibly in late hours, to perform on-device fraud.
Exposed victims
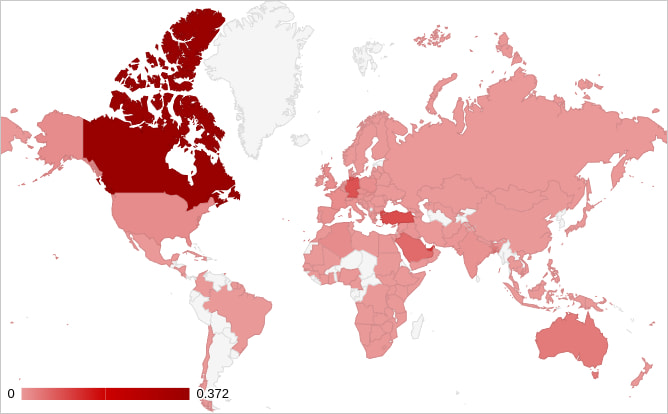
Due to improperly secured C2 infrastructure, Zimperium was also able to determine that at least 13,000 victims, most located in Canada and significant numbers also found in the United Arab Emirates, Turkey, and Germany, are impacted by this malware.
Source: Zimperium
This number corresponds to “several C2 servers,” according to Zimperium, so the total number of TrickMo victims is likely higher.
“Our analysis revealed that the IP list file is regularly updated whenever the malware successfully exfiltrates credentials,” explains Zimperium.
“We discovered millions of records within these files, indicating the extensive number of compromised devices and the substantial amount of sensitive data accessed by the Threat Actor.”
Cleafy previously withheld indicators of compromise from the public due to the misconfigured C2 infrastructure that could expose victim data to the broader cybercrime community. Zimperium has now opted to post everything in this GitHub repository.
However, TrickMo’s targeting scope appears broad enough to encompass app types (and accounts) beyond banking, including VPN, streaming platforms, e-commerce platforms, trading, social media, recruitment, and enterprise platforms.
Cleafy previously withheld indicators of compromise from the public due to the misconfigured C2 infrastructure that could expose victim data to the broader cybercrime community, but Zimperium now opted to post everything on this GitHub repository.
TrickMo is currently spreading through phishing, so to minimize the likelihood of infection, avoid downloading APKs from URLs sent via SMS or direct messages by people you don’t know.
Google Play Protect identifies and blocks known variants of TrickMo, so ensuring it’s active on the device is crucial in defending against the malware.



