Executive Summary
This article provides a practical guide to developing a detection strategy for Lightweight Directory Access Protocol (LDAP)-based attacks. We analyze real-world examples of nation-state and cybercriminal threat actors abusing LDAP attributes. We also examine common LDAP enumeration queries and assess their potential risks.
LDAP is a powerful protocol for accessing and managing directory services like Active Directory. LDAP is commonly used by criminals for lateral movement and critical assets enumeration in on-premises cyberattacks. Threat actors also frequently use tools like BloodHound and SharpHound, which leverage LDAP for malicious purposes.
Distinguishing benign from malicious LDAP activity within an organization is challenging. The high volume of benign event logs generated by a domain controller makes collecting as well as detecting malicious LDAP activity extremely difficult.
Palo Alto Networks customers are better protected against LDAP-based attacks through Cortex XDR, XSIAM and Xpanse, which we detail further in the Conclusion.
If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team.
| Related Unit 42 Topics | Cybercrime, Ransomware |
What Is LDAP?
LDAP is a fundamental protocol used across nearly every Windows environment, enabling administrators to access directory services like Active Directory. This protocol is used for managing users and groups, as well as allowing applications to query directory data in the background. Although developed by Microsoft and primarily used in Windows environments, LDAP is vendor-agnostic and can be used on non-Windows systems like macOS and Linux.
Threat actors often use LDAP because its functionality is so useful. Advanced persistent threat (APT) groups and other adversaries often use LDAP for network enumeration during the discovery phase of an attack. Attackers query directories to extract sensitive information such as user accounts, group memberships and permissions, which they then use to escalate privileges and target critical assets.
The Evolution of LDAP Protocols and Tools
LDAP has evolved significantly since its introduction in the early 1990s, adapting to the changing needs of directory services and security challenges. Below are two examples of changes in the more recent versions of LDAP:
- LDAP over SSL (LDAPS): This secure version of LDAP encrypts data in transit, protecting sensitive information from interception during communication.
- Active Directory Web Services (ADWS): This provides a more RESTful approach to interacting with directory services. Notably, ADWS tools often operate under the radar of traditional monitoring systems, as they do not generate direct LDAP traffic.
Tools like BloodHound and its C# data collector, SharpHound, have evolved alongside these protocols to visualize and analyze Active Directory environments. SOAPHound builds on these advancements by using ADWS to enumerate Active Directory data.
LDAP Logs: Visibility and Challenges
The high volume of log data generated by LDAP can overwhelm detection systems and make it difficult to identify malicious activity. It generates so much log data because it is used by many systems and applications.
Common processes like Outlook generate LDAP logs for example, highlighting the protocol’s extensive role in directory services. This pervasive use means that malicious LDAP activity can get lost amid the noise of normal operations.
To manage LDAP log volume effectively, focus on filtering relevant data, such as:
- Prioritize filtering: Focus on logs based on the type of account or service generating them to reduce noise.
- Exclude system-generated queries: Filter out queries that are unlikely to indicate user-initiated actions.
To address these challenges, Windows offers native logging of LDAP activity from the following sources:
- Microsoft-Windows-LDAP-Client – Event ID 30: System administrators can enable debug logging for LDAP clients to track activity on the initiating host. This logs details such as the initiating process, search entry, filter and search scope when LDAP is accessed via the LDAP client API through wldap32.dll. Figure 1 shows an Event ID 30 entry from the debug logs of an LDAP client.
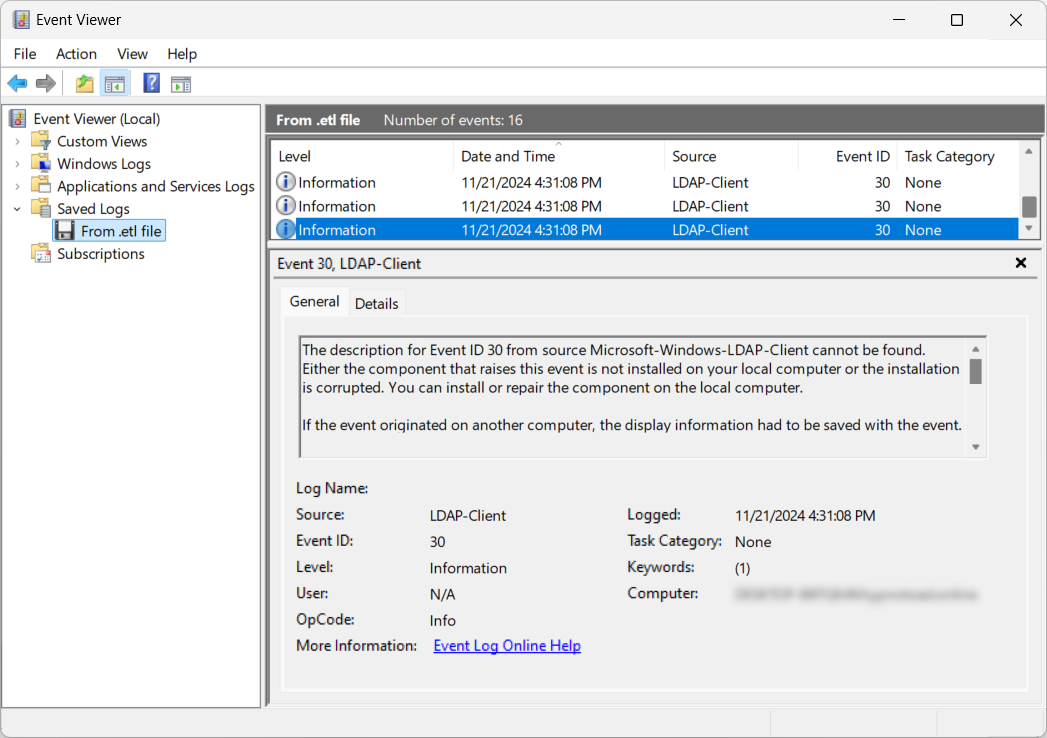
- Microsoft-Windows-ActiveDirectory_DomainService – Event ID 1644: This captures expensive, inefficient or slow LDAP queries made to domain controllers from all interacting hosts. Note that this Event ID is not enabled by default and requires updates to the Windows registry for activation. Figure 2 shows an Event ID 1644 entry seen in Event Viewer.
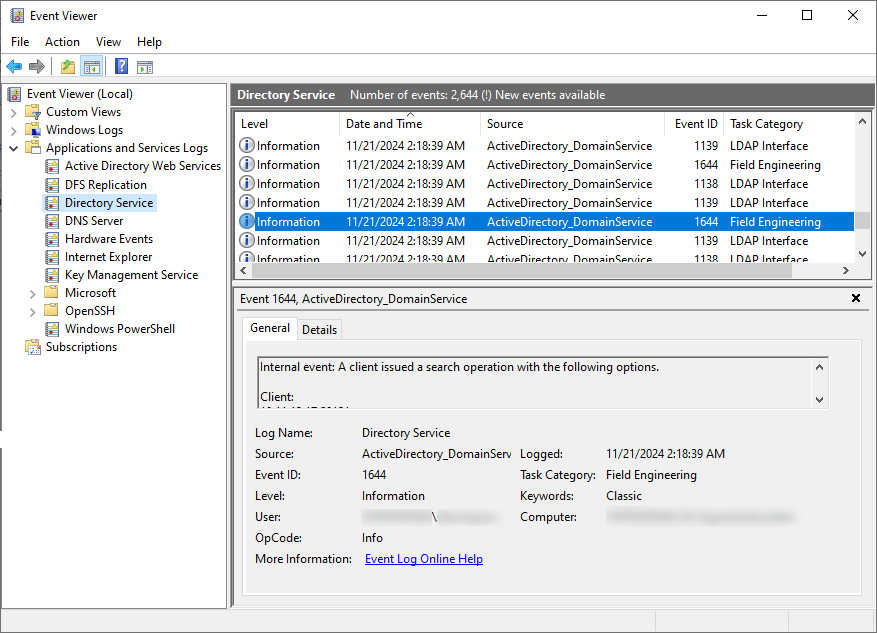
Real-World Scenarios of LDAP Enumeration
This section provides real-world examples of attackers using LDAP enumeration tools against Active Directory environments.
Stately Taurus Linked to Use of AdFind in Attacks Against Southeast Asian Government
As part of a campaign targeting government entities in Southeast Asia from 2021 to 2023, Stately Taurus was linked to the use of AdFind during the reconnaissance stage of the attack.
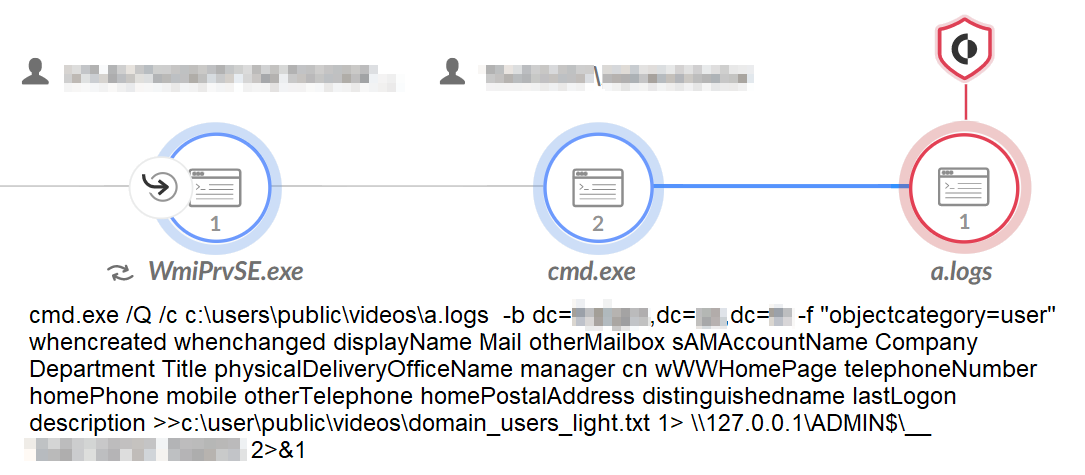
AdFind is a command-line query tool that can be used for LDAP enumeration by gathering information from an Active Directory domain controller. During the attack, threat actors renamed the tool from adfind.exe to a.logs in an attempt to evade detection.
Figure 3 shows a screenshot from a Cortex XDR alert in which the threat actor attempted to save the results of an AdFind query to the following filenames:
- Domain_users_light.txt
- Domain_computers_light.txt
- Domain_groups_light.txt
Ambitious Scorpius Wielded ADRecon in Ransomware Operations
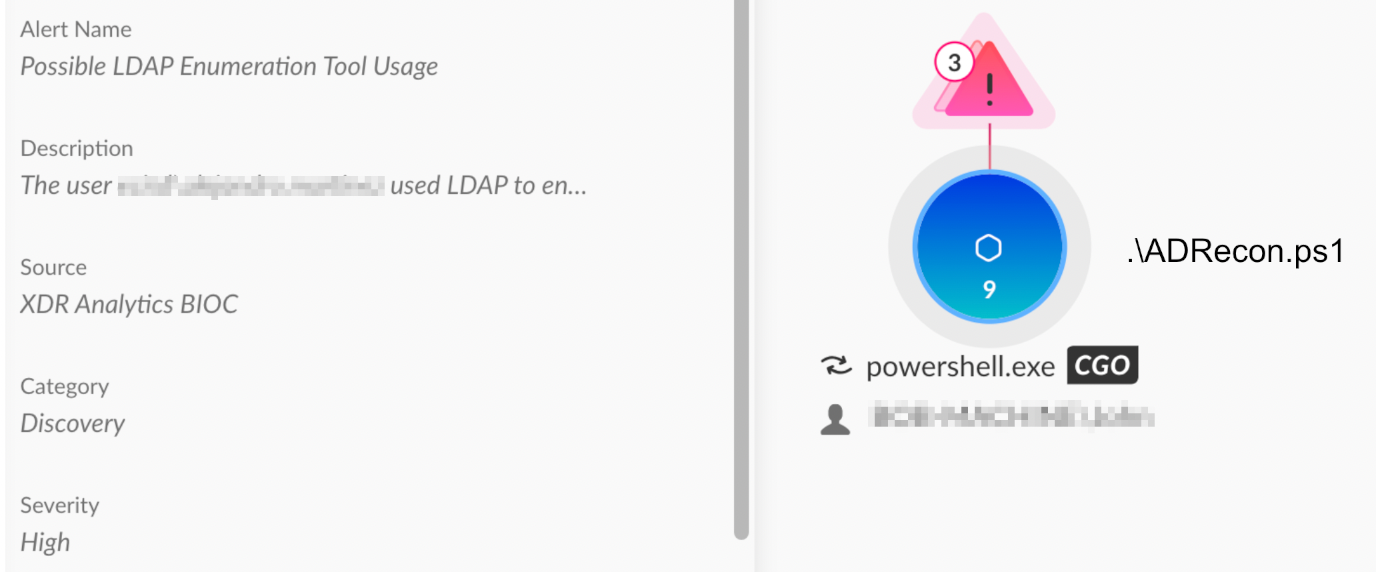
Affiliates of the BlackCat (ALPHV) ransomware group, which we track as Ambitious Scorpius, have used ADRecon in multiple intrusions. ADRecon is a PowerShell script that uses LDAP to gather information about an Active Directory environment and generates a report that provides a snapshot of the targeted network.
Due to this group’s continued use of ADRecon, we assess that the tool could be a part of the Ambitious Scorpius playbook. Figure 4 shows a Cortex XDR alert on the detection and prevention of ADRecon activity.
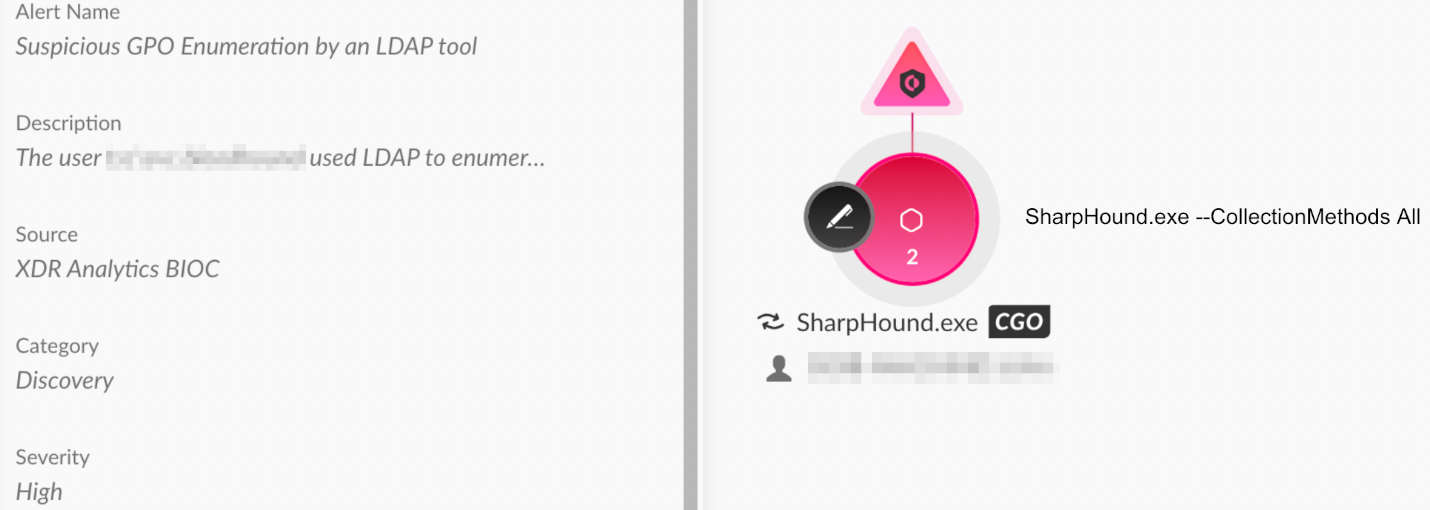
SharpHound Used in an IcedID and Dagon Locker Ransomware Operation
In April 2024, The DFIR Report described an intrusion that involved IcedID malware and Dagon Locker ransomware. During this intrusion, the attackers used SharpHound to collect data about the Active Directory environment.
SharpHound is a data collector component of BloodHound. It uses Windows API and LDAP functions to collect data from domain controllers and Windows systems that are part of the domain. Figure 5 shows the detection and prevention of SharpHound in Cortex XDR.
Detection Strategies for LDAP-Based Attacks
Detecting LDAP-based attacks effectively involves monitoring LDAP logs for suspicious activity. Event logs capture crucial data, including:
- Visited entries: This represents the total number of LDAP queries made.
- Returned entries: This indicates the actual results returned from those queries or their count.
Legitimate LDAP queries typically target specific objects or attributes, resulting in fewer visited and returned entries. On the other hand, enumeration attempts use broader queries as attackers seek to collect as much information as possible by querying all users, computers or groups.
Below are key detection strategies to help identify and mitigate LDAP enumeration attempts:
1. Visited and returned entries
Review logs for Event ID 1644 events for both visited and returned entries.
- Low “visited to returned” ratio: This low ratio is typical of legitimate queries targeting a wide range of objects.
- High sum of returned entries: This indicates an attempt to gather large amounts of directory data. This is a possible indicator of enumeration by an attacker.
2. User context
Analyzing LDAP queries for user context can also reveal enumeration activity:
- User title or role: Consider whether the LDAP activity fits the user’s typical role. For example, service accounts and IT personnel might legitimately perform extensive LDAP queries. However, if a user outside these roles engages in a similar activity, this could indicate potential enumeration.
- Search scope anomalies: Users who suddenly expand their search scope beyond typical patterns could be conducting reconnaissance.
3. Baseline and anomalies
Establishing a baseline for LDAP query data can help reveal anomalies or deviations from standard user and machine behavior. This strategy has three components:
- Normalization: Standardize query data to identify patterns and deviations
- Distribution: Track how many machines executed a query
- User diversity: Monitor how many users have run a query
4. LDAP query filters
Since attackers use diverse LDAP query filters to extract directory data, a wide variety of these filters in LDAP query logs often point to enumeration activity. The type of LDAP query filter can reveal the type of enumeration. Some common types of LDAP enumeration that are important to monitor include:
- Admin enumeration: Queries targeting administrative accounts and privileges
- Service accounts enumeration: Identification of service accounts and their configurations
- GPO enumeration: Retrieval of Group Policy Objects and their settings
- Domain machine enumeration: Gathering information about machines under the same domain
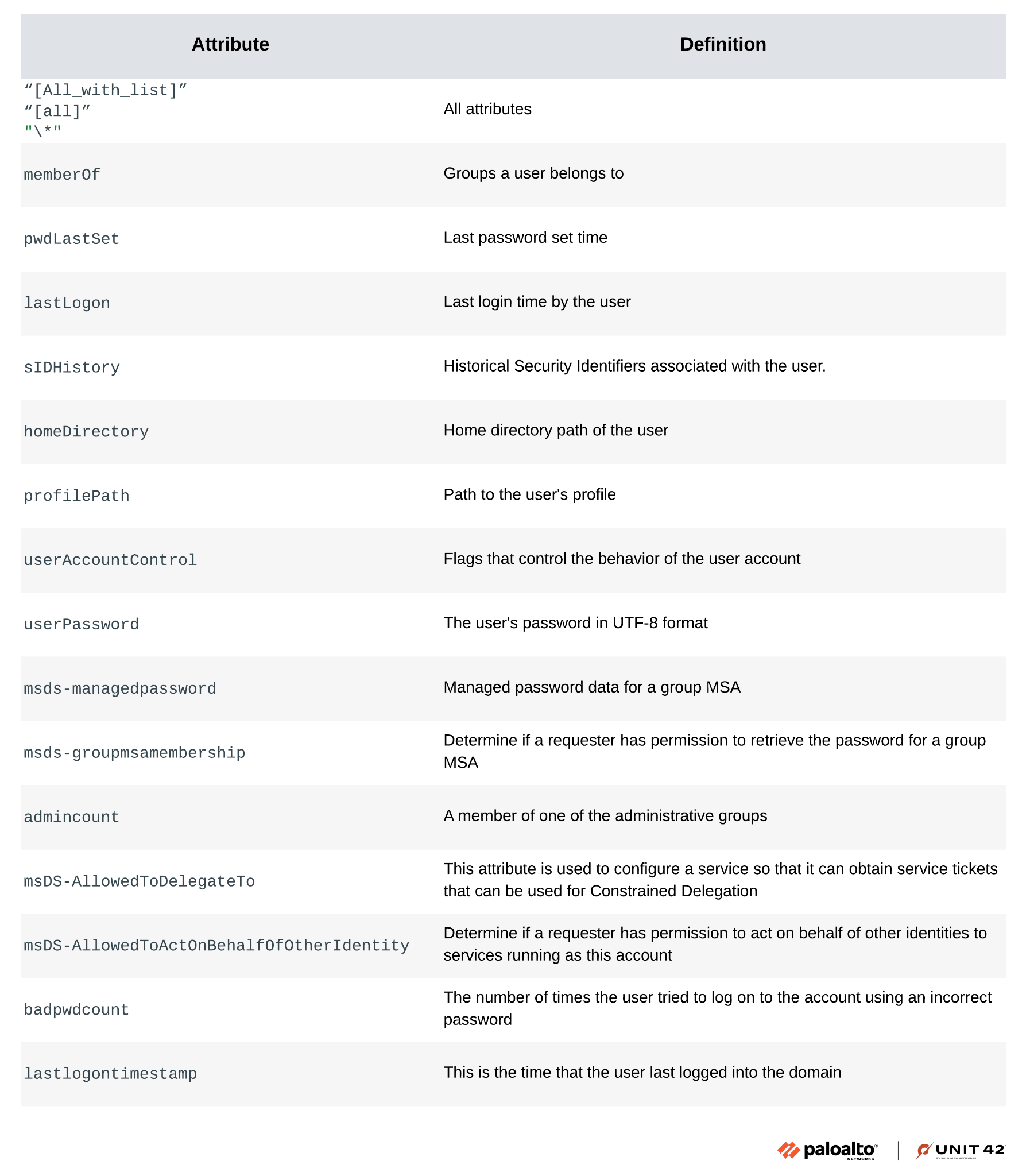
5. Suspicious Attributes
Monitoring queries for specific attributes like memberOf, pwdLastSet, lastLogon, and admincount can help detect suspicious activity.
Attackers commonly use the following attributes in LDAP queries:
- admincount
- badpwdcount
- homeDirectory
- lastLogon
- memberOf
- msDS-AllowedToActOnBehalfOfOtherIdentity
- msDS-AllowedToDelegateTo
- msds-groupmsamembership
- msds-managedpassword
- profilePath
- pwdLastSet
- sIDHistory
- userAccountControl
- userPassword
Appendix A shows an example of an XQL query in Cortex XDR to track the above LDAP attributes.
Figure 6 displays a table detailing examples of LDAP attributes, including their definitions and potential implications for security.
Conclusion
LDAP is a double-edged sword in Active Directory. It is essential for administration yet vulnerable to exploitation. While LDAP simplifies directory management, attackers can exploit its powerful querying capabilities to gather sensitive information.
This article highlights the challenges of detecting malicious LDAP activity. It also provides real-world examples of LDAP enumeration attacks, along with practical detection tips.
Understanding and monitoring LDAP enumeration, coupled with robust detection strategies, is essential to mitigating risks and securing directory services.
Protections and Mitigations
For Palo Alto Networks customers, our products and services provide the following coverage:
- Cortex XDR and XSIAM are designed to:
- Protect against exploitation of different vulnerabilities as well as against malicious behaviors, through Behavioral Threat Protection.
- Detect user and credential-based threats by analyzing user activity from multiple data sources including endpoints, network firewalls, Active Directory, identity and access management solutions and cloud workloads. Cortex builds behavioral profiles of user activity over time with machine learning. It detects anomalous activity indicative of credential-based attacks by comparing new activity to past activity, peer activity and the expected behavior of the entity.
- Detect LDAP network attacks, including those mentioned in this article, with behavioral analytics, through Cortex XDR Pro and XSIAM.
- Help protect against post-exploitation activities using the multi-layer approach.
- Cortex XSIAM has released a Suspicious LDAP Search Query Playbook to enhance the response to analytics LDAP alerts. This playbook evaluates the risk score of the entities involved, examines the prevalence of the related processes, and checks the executed command line for suspicious parameters. If any suspicious activity is detected during the investigation phase, the playbook will terminate the causality process as a remediation action.
- Cortex Xpanse and the ASM module for XSIAM are capable of detecting Internet-exposed LDAP servers.
If you think you might have been impacted or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Palo Alto Networks has shared these findings, including file samples and indicators of compromise, with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Additional Resources
- Cyberespionage Attacks Against Southeast Asian Government Linked to Stately Taurus, Aka Mustang Panda – Unit 42, Palo Alto Networks
- The Anatomy of a BlackCat (ALPHV) Attack – Sygnia
- The many lives of BlackCat ransomware – Microsoft
- From IcedID to Dagon Locker Ransomware in 29 Days – The DFIR Report
- SharpHound — BloodHound 4.3.1 documentation – BloodHound
Appendix A
The following XQL query in Cortex tracks LDAP query attributes commonly targeted by attackers:
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
|
dataset = xdr_data // Using the xdr dataset
| filter event_type = ENUM.EVENT_LOG and action_evtlog_event_id in (1644, 30)
| alter
evtlog_ldap_domain_service_attributes = json_extract_scalar(action_evtlog_data_fields, “$.param7”),
ldap_attribute_list = json_extract_scalar(action_evtlog_data_fields, “$.AttributeList”),
ldap_1644_search_filter = json_extract_scalar(action_evtlog_data_fields, “$.param2”),
ldap_30_search_filter = json_extract_scalar(action_evtlog_data_fields, “$.SearchFilter”)
| alter
attribute_list = lowercase(coalesce(evtlog_ldap_domain_service_attributes, ldap_attribute_list)),
search_filter = lowercase(coalesce(ldap_30_search_filter, ldap_1644_search_filter))
| alter attribute_regex_check = regextract(
attribute_list,
“All_with_list|all|memberOf|pwdLastSet|lastLogon|sIDHistory|homeDirectory|profilePath|userAccountControl|userPassword|msds-managedpassword|msds-groupmsamembership|admincount|msDS-AllowedToDelegateTo|badpwdcount|msDS-AllowedToActOnBehalfOfOtherIdentity”
)
| filter attribute_regex_check != Null
// Filter out spamming queries
| filter search_filter != “(objectclass=*)”
| filter search_filter != “(objectcategory=*)”
| fields attribute_list, attribute_regex_check, action_evtlog_data_fields, actor_process_image_name, search_filter
|
Appendix B
A Dive into LDAP Queries and Tools
Basics of LDAP Query Filters
LDAP queries retrieve directory objects like users, groups or computers based on specific filters. This section provides examples of query filters that system administrators can use for legitimate purposes, but that adversaries could also use for malicious purposes.
For example, to find all user accounts in an Active Directory environment, we can use the following query filter:
|
1
|
(&(objectClass=user)(objectCategory=person))
|
Additionally, we can refine queries to target specific needs by adding more attributes to the query filter. For example, to find users in privileged groups, we can use this LDAP query filter:
|
1
|
(&(objectClass=user)(objectCategory=person)(adminCount=1))
|
The above examples use the & symbol, which is a logical AND operator and means all the specified conditions must be met. LDAP supports logical operators for advanced filtering:
- AND (&): Ensures all specified conditions must be met
- OR (|): Allows any one of the conditions to be met
- NOT (!): Excludes objects that match a certain condition
Tools for LDAP Enumeration
Attackers have an array of tools at their disposal for LDAP enumeration. Figure 7 depicts some of these key tools. Figure 7 also shows examples of queries each tool can execute:
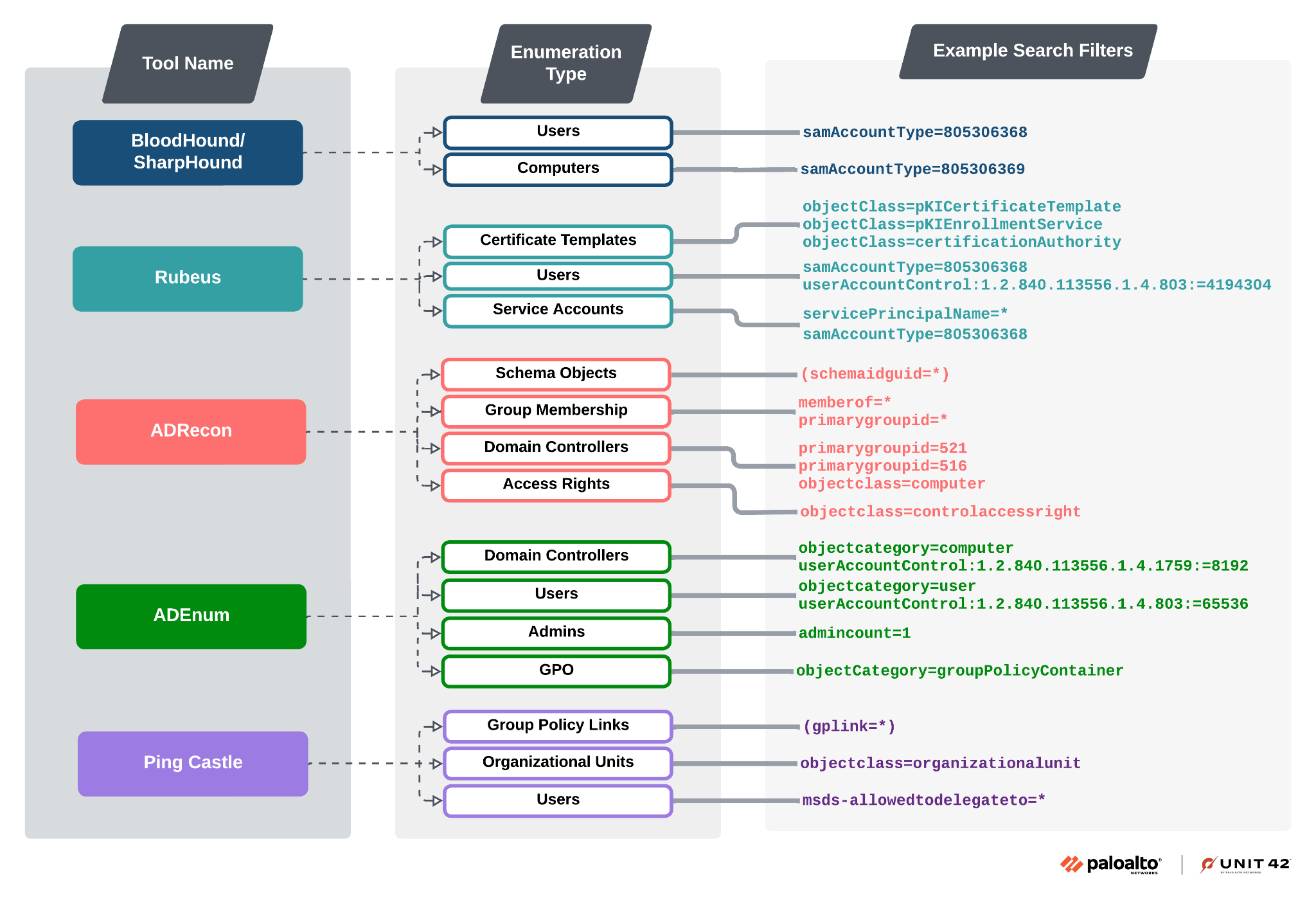
Each tool facilitates different types of LDAP queries that attackers use to map Active Directory environments, helping them identify key targets such as service accounts and privileged users.
Analysis of LDAP Enumeration Query Attributes
Understanding the nature of LDAP enumeration queries that attackers use is critical for detecting malicious activity in Active Directory environments. Here are some common queries and their potential risks:
Users With Kerberos Pre-authentication Disabled
|
1
|
userAccountControl:1.2.840.113556.1.4.803:=4194304
|
- Description: The userAccountControl attribute is used to identify user accounts that have Kerberos pre-authentication disabled. This setting is a key condition for the AS-REP roasting attack.
- Risk: Attackers can request and potentially crack AS-REP tickets from these accounts, which can lead to unauthorized access.
Service Accounts
|
1
|
servicePrincipalName=*
|
- Description: Identifies user accounts that have any service principal name (SPN) entries.
- Risk: SPNs are used in Kerberos authentication to associate service instances with user accounts. Attackers use this information to perform Kerberoasting attacks, where they attempt to crack service tickets.
Enumerate Active Directory Users
|
1
|
samAccountType=805306368
|
- Description: The samAccountType attribute with the value 805306368 specifies Active Directory user accounts.
- Risk: An LDAP query with this attribute provides a list of all user accounts, which can be used for further enumeration or to identify targets for attacks.



