Researchers from Claroty’s Team82 arm have obtained a sample of a custom-built IoT/OT malware called IOCONTROL used by the Iran-affiliated attackers to attack Israel- and U.S.-based OT/IoT devices. IOCONTROL has been used to attack IoT and SCADA/OT (supervisory control and data acquisition/operational technology) devices of various types including IP cameras, routers, PLCs (programmable logic controllers), HMIs (human-machine interfaces), firewalls, and other similar devices. Some of the affected vendors include Baicells, D-Link, Hikvision, Red Lion, Orpak, Phoenix Contact, Teltonika, Unitronics, and others.
“We’ve assessed that IOCONTROL is a cyberweapon used by a nation-state to attack civilian critical infrastructure,” Team82 researchers disclosed in a blog post this week. “Our analysis of IOCONTROL includes an in-depth look at the malware’s capabilities and unique communication channels to the attackers’ command-and-control infrastructure.”
Based on a generic OT/IoT malware framework for embedded Linux-based devices that are utilized and compiled against specific targets as needed, the IOCONTROL malware communicates with a C2 over a secure MQTT channel and supports basic commands including arbitrary code execution, self-delete, port scan, and more. This functionality is enough to control remote IoT devices and perform lateral movement if needed. In addition, IOCONTROL has a basic persistence mechanism over a daemon installation and stealth mechanism, for example, the initial payload uses modified UPX packing and the malware uses DNS over HTTPS to hide its C2 infrastructure as much as possible.
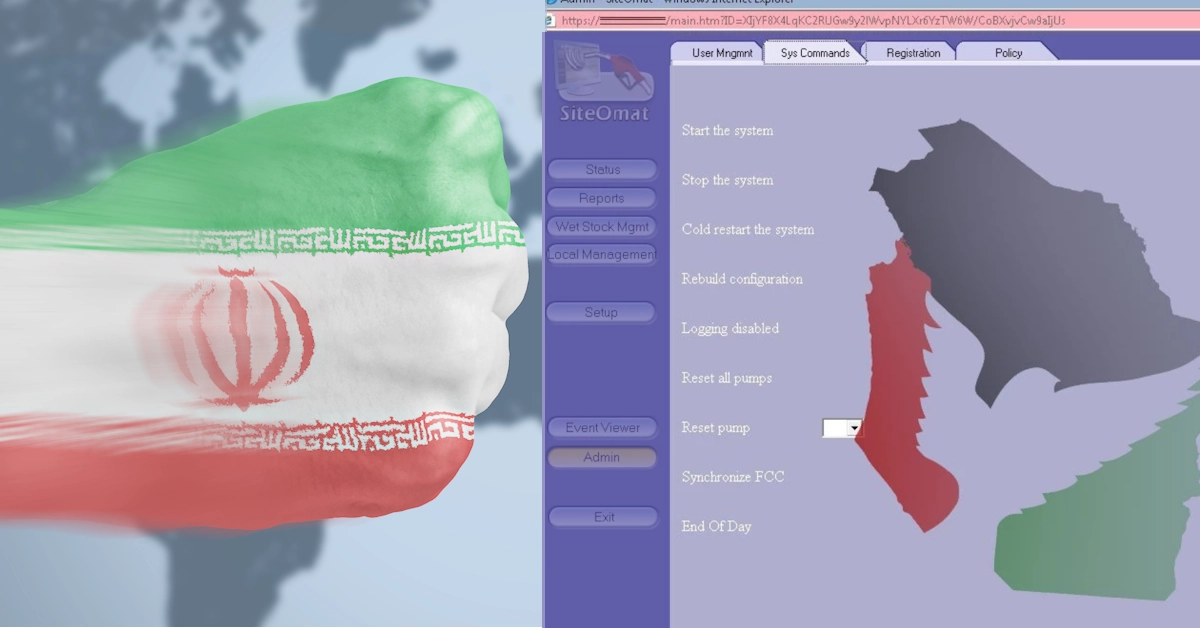
The specific sample was extracted from a Gasboy/ORPAK device, which is a fuel system platform. However, IOCONTROL was used to attack IoT and SCADA devices of various types including IP cameras, routers, PLCs, HMIs, firewalls, and more.
Team82 detailed that IOCONTROL malware is believed to be part of a global cyber operation against western IoT and OT devices. Affected devices include routers, PLCs, HMIs, firewalls, and other Linux-based IoT/OT platforms. While the malware is believed to be custom-built by the threat actor, it seems that the malware is generic enough that it is able to run on a variety of platforms from different vendors due to its modular configuration.
Team82 has analyzed a malware sample extracted from a fuel management system that was allegedly compromised by a threat actor group linked to Iran known as the CyberAv3ngers, which is also believed to be responsible for the Unitronics attack last fall.
One particular IOCONTROL attack wave involved the compromise of several hundred Israel-made Orpak Systems and U.S.-made Gasboy fuel management systems in Israel and the United States. The malware is essentially custom built for IoT devices but also has a direct impact on OT such as the fuel pumps that are heavily used in gas stations.
The attacks are another extension of the geopolitical conflict between Israel and Iran.
Team82 reported that “IOCONTROL was hiding inside Gasboy’s Payment Terminal, called OrPT. An attacker with full control over the payment terminal means they had the ability to shut down fuel services and potentially steal credit card information from customers.”
The so-called CyberAv3ngers are believed to be part of the Islamic Revolutionary Guard Corps Cyber Electronic Command (IRGC-CEC) and have been vocal on Telegram sharing screenshots, and other information about the compromises of these fuel systems.
In February, the U.S. Department of the Treasury announced sanctions against six IRGC-CEC officials linked to the CyberAv3ngers and offered a $10 million USD bounty for information leading to the identification or location of anyone involved in the attacks.
“Our analysis of the sample we obtained from VirusTotal (21 detections as of Dec. 10, 2024, after a period of time when there were still zero detections as of September 2024) concludes that the malware is essentially a cyberweapon used by a nation-state to attack civilian critical infrastructure; at least one of the victims were the Orpak and Gasboy fuel management systems,” Team82 reported. “For secure communication between compromised devices and the attackers, IOCONTROL leverages the MQTT protocol as a dedicated IoT communication channel. The attackers were able to disguise traffic over MQTT to and from the attackers’ command-and-control infrastructure.”
The CyberAv3ngers, meanwhile, have implicitly stated they will continue to target Israel-made technology in critical infrastructure. In October 2023, water treatment facilities in the U.S. and Israel were attacked by the group. Integrated Unitronics Vision series PLC/HMI devices were targeted inside these facilities; the attacks resulted in the defacement of these OT devices. The attacks were likely projections of power from the CyberAv3ngers, demonstrating their access to the devices and hoping to instill fear regarding the quality of water in affected areas.
Team82 noted that around the same time of the attacks against water facilities, the CyberAv3ngers published on Telegram claims it had attacked 200 gas stations in Israel and the U.S., specifically targeting Orpak systems. The attackers released screenshots of the main management portal of the attacked gas stations, as well as databases of information about their targets and leaked data. “Following up on the CyberAv3ngers’ claim of compromising Orpak systems, we found WHOIS records indicating registration of a domain name ‘tylarion867mino[dot]com’ on Nov. 23, 2023. This domain would be used by the attackers to set up a command-and-control infrastructure in order to manage all the compromised devices.”
The blog added that last December, an Israeli-associated hacking group called Gonjeshke Darande claimed to have attacked and compromised 70 percent of Iran’s gas stations, claiming it was ‘in response to the aggression of the Islamic Republic and its proxies in the region.’
“While the reports about these attacks by CyberAv3ngers against Orpak devices span from mid-October 2023 to late January 2024, our team obtained a publicly available sample of IOCONTROL from VirusTotal, indicating the group relaunched their targeted campaign in July and August,” Team82 added. “Our research blog presents our analysis of the attack against multiple IoT/OT devices, including Orpak and Gasboy devices. In addition, we will analyze the IOCONTROL malware used in the attacks, the attacker’s command and control infrastructure, and communications over the MQTT protocol.”
Team82 added that “static analysis took far too long and too much effort, therefore we decided to pivot our efforts toward dynamic analysis of the malware sample. This meant we were going to have to execute the malware sample safely and debug it. The approach we took to execute and unpack the malware executable was emulation, specifically using the Python-based Unicorn CPU emulation engine.”
The researchers chose this path due to the malware sample being written for an archaic ARM 32-bit BE CPU architecture, which made emulation the best candidate for a solution to execute and unpack the malware sample, and they needed to find a way to execute the malware in a safe and controlled environment that would not potentially infect setup or perform malicious activity on systems.
“Unicorn gave us more granular control over the emulation than other engines such as QEMU; it not only allowed us to carefully inspect the malware execution flow but also allowed us to have full control over the capabilities of the malware with regards to syscall invocations and OS interactions,” the researchers added. “Emulating the sample was a gradual process in which we closely inspected the execution flow of the malware. This included tracing the executed code and saving memory mappings along each emulation round.”
In the beginning, each round of emulation was terminated abruptly, shortly after initiating the execution of the sample. This was caused most often by an attempt to invoke a syscall for OS interaction by the malware. Unicorn provides the capability to execute emulated CPU instructions in various architectures and variations. Yet it doesn’t facilitate specific OS infrastructure such as syscall implementations of specific operating systems such as Linux or Windows.
After unpacking the malware, Team82 researchers were left with two artifacts: an encrypted data section and an executable. “When examining the executable in IDA, we noticed that in many different locations in the code, it uses data from the encrypted section, using it for different operations such as a path for a file, IP address to connect to, etc.”
They then managed to discover that this encrypted section was the encrypted configuration of the malware. “In order to decrypt the configuration of the malware, it uses a decryption function, which receives an index specifying which configuration it wants decrypted from a list. This technique allows minimizing the possibility of extracting decrypted configuration entries from the process memory during the malware runtime.”
Also, in this decryption function, the malware fetches the first byte from the encrypted configuration entry. This value is used to tell how long that specific encrypted configuration entry is, after reading the encrypted entry raw bytes, the malware uses the AES-256-CBC decryption scheme to extract the actual configuration entry. Prior to decryption, the malware extracts the key and IV pair from a GUID stored in one of its strings, which the malware uses for many purposes.
Last month, Censys data revealed over 145,000 exposed ICS (industrial control systems) services globally, with more than 48,000 in the U.S. alone. Researchers analyzed this exposure to aid the cybersecurity community in understanding and protecting the global ICS attack surface. Of the exposed ICS services, 38 percent are in North America, 35 percent in Europe, and 22 percent in Asia, with the U.S. alone accounting for over one-third of global exposures.