A new software-based power side-channel attack called ‘Collide+Power’ was discovered, impacting almost all CPUs and potentially allowing data to leak. However, the researchers warn that the flaw is low-risk and will likely not be used in attacks on end users.
The flaw was discovered by researchers at the Graz University of Technology and exploits weaknesses in the CPU hardware to leak potentially sensitive data.
Even though the discovered vulnerability (CVE-2023-20583) holds research significance, it is practically very challenging to exploit in most real-world cases; hence it was assigned a low severity.
Collide+Power details
The main concept of Collide+Power is to leak data from measured CPU power consumption values when a data “collision” between the attacker’s dataset and data sent by other applications to overwrite the former happens in CPU cache memory.
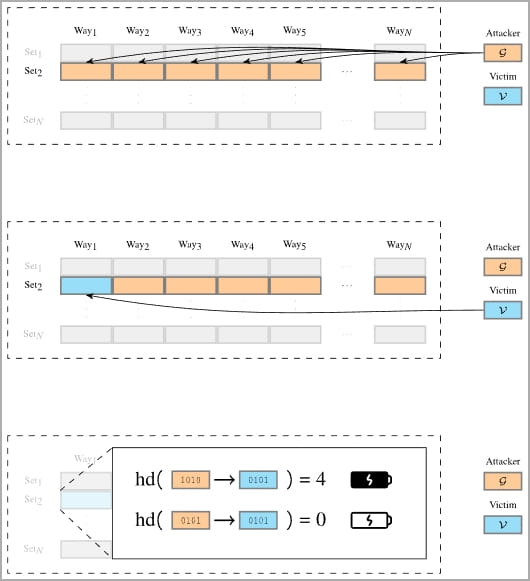
Collide+Power comprises two variants that create data collisions between the user’s sensitive data and the attacker’s data inside the CPU cache.
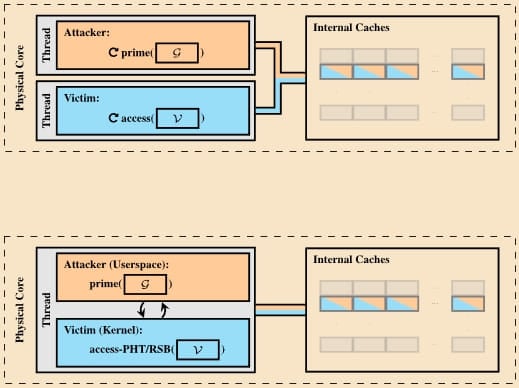
The first method requires enabling hyperthreading and the victim to access the targeted secrets, like a decryption key.
The second variant abuses the “prefetch gadget” in the OS to load the target data onto the CPU cache and collide it with the attacker’s data without involving the victim.
The researchers say Collide+Power can also enhance other software-based power side-channel attacks like PLATYPUS and Hertzbleed.
Impact and vendor responses
Collide+Power impacts processors made by Intel, AMD, and those using ARM architectures. However, the researchers have not disclosed specific models, so it is unclear if all modern CPUs are affected.
“Nevertheless, we assume that nearly all CPUs are affected by Collide+Power as the exploited leakage is fundamentally a result of how we build CPUs,” explains the Collide+Power disclosure site.
Despite the potentially broad impact, the developers of the attack clearly state that users “do not need to worry” about it as the data leakage rates are relatively low, and the attack requires lengthy physical access to the target device as well as specialized knowledge to carry out.
AMD has made a similar statement on its security bulletin about CVE-2023-20583, playing down the practical importance of the attack for the average user.
AMD stated that its EPYC server processors have a performance determinism mode that helps mitigate this data leakage, while Ryzen series processors can have their core boost function disabled to reduce frequency changes and make it harder to leak data from CPU memory.
ARM has also posted a security advisory to track developments and new findings around Collide+Power.
As for mitigating the problem, the Graz team says data collisions are complicated to address given the prevalence of specific design techniques underpinning almost all modern CPUs, constituting the basis for Collide+Power.
“Preventing data collisions in hardware is a highly complex redesign of general-purpose CPUs, which we think is unlikely to happen in the near future due to the number of shared hardware components in a CPU,” explain the researchers.
“Therefore, the more realistic mitigation is preventing an attacker from observing the power-related signal.”
The source code for the Collide+Power attack is expected to be uploaded to this GitHub repository soon.




