The Qilin ransomware group has been using a new tactic and deploys a custom stealer to steal account credentials stored in Google Chrome browser.
The credential-harvesting techniques has been observed by the Sophos X-Ops team during incident response engagements and marks an alarming change on the ransomware scene.
Attack overview
The attack that Sophos researchers analyzed started with Qilin gaining access to a network using compromised credentials for a VPN portal that lacked multi-factor authentication (MFA).
The breach was followed by 18 days of dormancy, suggesting the possibility of Qilin buying their way into the network from an initial access broker (IAB).
Possibly, Qilin spent time mapping the network, identifying critical assets, and conducting reconnaissance.
After the first 18 days, the attackers moved laterally to a domain controller and modified Group Policy Objects (GPOs) to execute a PowerShell script (‘IPScanner.ps1’) on all machines logged into the domain network.
The script, executed by a batch script (‘logon.bat’) that was also included in the GPO, was designed to collect credentials stored in Google Chrome.
The batch script was configured to run (and trigger the PS script) every time a user logged into their machine, while stolen credentials were saved on the ‘SYSVOL’ share under the names ‘LD’ or ‘temp.log.’
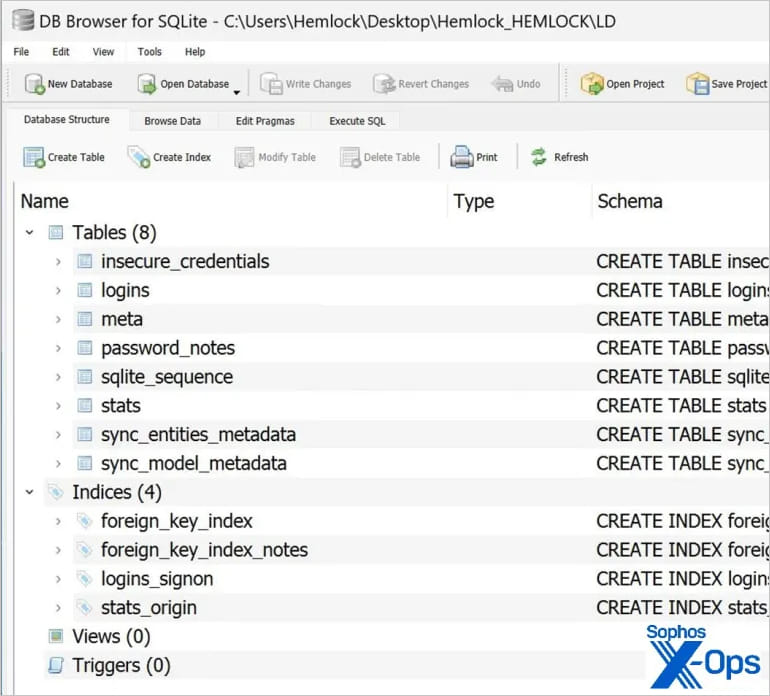
Source: Sophos
After sending the files to Qilin’s command and control (C2) server, the local copies and related event logs were wiped, to conceal the malicious activity. Eventually, Qilin deployed their ransomware payload and encrypted data on the compromised machines.
Another GPO and a separate batch file (‘run.bat’) were used to download and execute the ransomware across all machines in the domain.
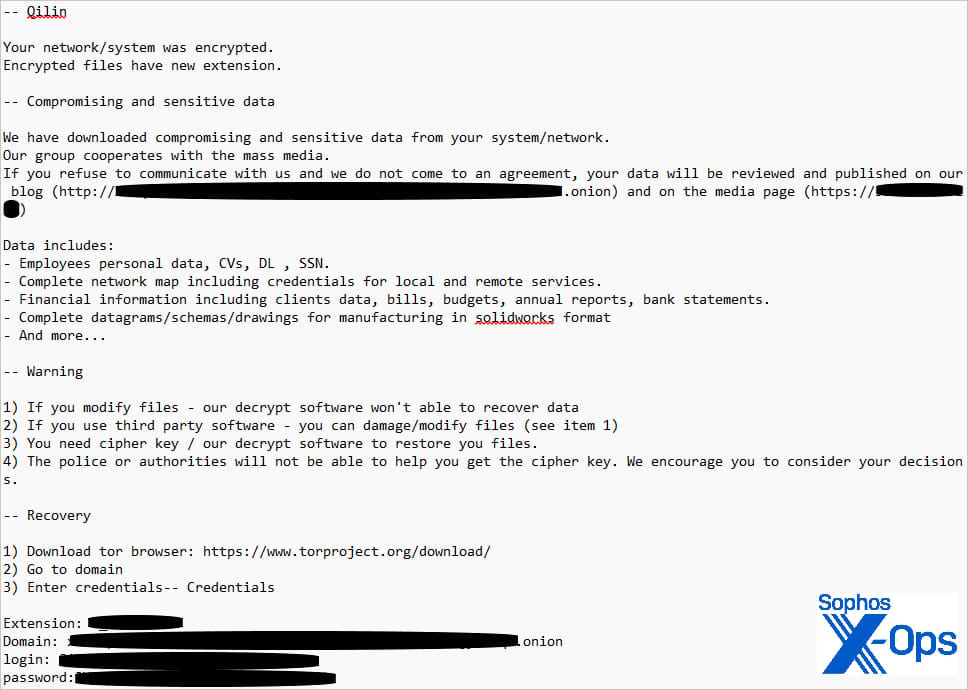
Source: Sophos
Defense complexity
Qilin’s approach to target Chrome credentials creates a worrying precedent that could make protecting against ransomware attacks even more challenging.
Because the GPO applied to all machines in the domain, every device that a user logged into was subject to the credential harvesting process.
This means that the script potentially stole credentials from all machines across the company, as long as those machines were connected to the domain and had users logging into them during the period the script was active.
Such extensive credential theft could enable follow-up attacks, lead to widespread breaches across multiple platforms and services, make response efforts a lot more cumbersome, and introduce a lingering, long-lasting threat after the ransomware incident is resolved.
Organizations can mitigate this risk by imposing strict policies to forbid the storage of secrets on web browsers.
Additionally, implementing multi-factor authentication is key in protecting accounts against hijacks, even in the case of credential compromises.
Finally, implementing the principles of least privilege and segmenting the network can significantly hamper a threat actor’s ability to spread on the compromised network.
Given that Qilin is an unconstrained and multi-platform threat with links to the Scattered Spider social engineering experts, any tactical change poses a significant risk to organizations.



