The persistent threat actors behind the SolarMarker information-stealing malware have established a multi-tiered infrastructure to complicate law enforcement takedown efforts, new findings from Recorded Future show.
“The core of SolarMarker’s operations is its layered infrastructure, which consists of at least two clusters: a primary one for active operations and a secondary one likely used for testing new strategies or targeting specific regions or industries,” the company said in a report published last week.
“This separation enhances the malware’s ability to adapt and respond to countermeasures, making it particularly difficult to eradicate.”
SolarMarker, known by the names Deimos, Jupyter Infostealer, Polazert, and Yellow Cockatoo, is a sophisticated threat that has exhibited a continuous evolution since its emergence in September 2020. It has the capability to steal data from several web browsers and cryptocurrency wallets, as well as target VPN and RDP configurations.
Among the top targeted verticals are education, government, healthcare, hospitality, and small and medium-sized enterprises, per data gathered since September 2023. This includes prominent universities, government departments, global hotel chains, and healthcare providers. A majority of the victims are located in the U.S.
Over the years, the malware authors have focused their development efforts on making it more stealthy through increased payload sizes, the use of valid Authenticode certificates, novel Windows Registry changes, and the ability to run it directly from memory rather than disk.
Infection pathways typically involve hosting SolarMarker on bogus downloader sites advertising popular software that can be visited by a victim either inadvertently or due to search engine optimization (SEO) poisoning, or via a link in a malicious email.
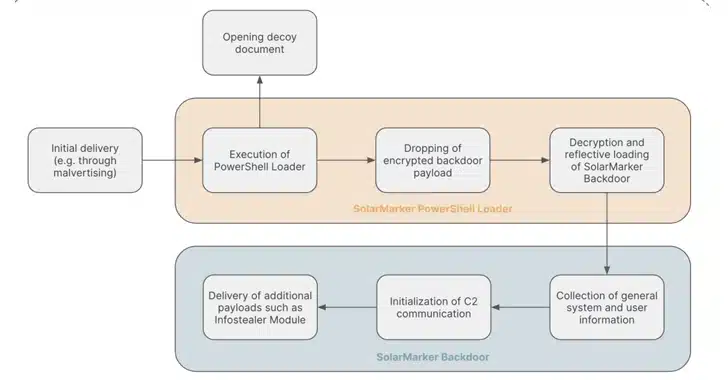
The initial droppers take the form of executables (EXE) and Microsoft Software Installer (MSI) files that, when launched, lead to the deployment of a .NET-based backdoor that’s responsible for downloading additional payloads for facilitating information theft.
Alternate sequences leverage the counterfeit installers to drop a legitimate application (or a decoy file), while simultaneously launching a PowerShell loader for delivering and executing the SolarMarker backdoor in memory.
SolarMarker attacks over the past year have also involved the delivery of a Delphi-based hVNC backdoor called SolarPhantom that allows for remotely controlling a victim machine without their knowledge.
“In recent cases, SolarMarker’s threat actor has alternated between Inno Setup and PS2EXE tools to generate payloads,” cybersecurity firm eSentire noted in February 2024.
As recently as two months ago, a new PyInstaller version of the malware was spotted in the wild propagated using a dishwasher manual as a decoy, according to a malware researcher who goes by the name Squiblydoo and has extensively documented SolarMarker over the years.
There is evidence to suggest that SolarMarker is the work of a lone actor of unknown provenance, although prior research from Morphisec has alluded to a possible Russian connection.
Recorded Future’s investigation into the server configurations linked to the command-and-control (C2) servers has uncovered a multi-tiered architecture that is part of two broad clusters, one of which is likely used for testing purposes or for targeting specific regions or industries.
The layered infrastructure includes a set of Tier 1 C2 servers that are in direct contact with victim machines. These servers connect to a Tier 2 C2 server via port 443. Tier 2 C2 servers, similarly communicate with Tier 3 C2 servers via port 443, and Tier 3 C2 servers consistently connect to Tier 4 C2 servers via the same port.
“The Tier 4 server is considered the central server of the operation, presumably used for effectively administering all downstream servers on a long-term basis,” the cybersecurity firm said, adding it also observed the Tier 4 C2 server communicating with another “auxiliary server” via port 8033.
“Although the precise purpose of this server remains unknown, we speculate that it is used for monitoring, possibly serving as a health check or backup server.”