The China-linked threat actor known as MirrorFace has been attributed to a new spear-phishing campaign mainly targeting individuals and organizations in Japan since June 2024.
The aim of the campaign is to deliver backdoors known as NOOPDOOR (aka HiddenFace) and ANEL (aka UPPERCUT), Trend Micro said in a technical analysis.
“An interesting aspect of this campaign is the comeback of a backdoor dubbed ANEL, which was used in campaigns targeting Japan by APT10 until around 2018 and had not been observed since then,” security researcher Hara Hiroaki said.
It’s worth noting that MirrorFace’s use of ANEL was also documented by ESET last month as part of a cyber attack targeting a diplomatic organization in the European Union using lures related to the World Expo.
MirrorFace, also known as Earth Kasha, is the name given to a Chinese threat actor that’s known for its persistent targeting of Japanese entities. It’s assessed to be a sub-cluster within APT10.
The latest campaign is a departure from the hacking group’s intrusions observed during 2023, which primarily sought to exploit security flaws in edge devices from Array Networks and Fortinet for initial access.
The switch to spear-phishing email messages is intentional, per Trend Micro, and a decision motivated by the fact that the attacks are designed to single out individuals rather than enterprises.
“Additionally, an analysis of the victim profiles and the names of the distributed lure files suggests that the adversaries are particularly interested in topics related to Japan’s national security and international relations,” Hiroaki pointed out.

The digital missives, sent from either free email accounts or compromised accounts, contain a link to Microsoft OneDrive. They aim to lure recipients into downloading a booby-trapped ZIP archive using themes related to interview requests and Japan’s economic security from the perspective of current U.S.-China relations.
Trend Micro said the contents of the ZIP archive vary depending on the targets, adding it uncovered three different infection vectors that have been used to deliver a malicious dropper dubbed ROAMINGMOUSE –
- A macro-enabled Word document
- A Windows shortcut file that executes a self-extracting archive (SFX), which then loads a macro-enabled template document
- A Windows shortcut file that executes PowerShell responsible for dropping an embedded cabinet archive, which then loads a macro-enabled template document
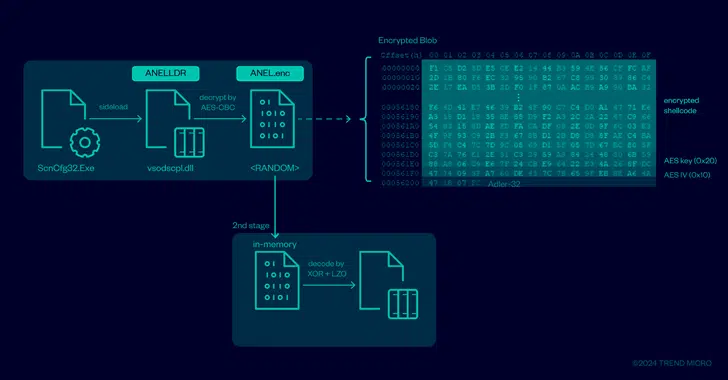
The macro-enabled document, ROAMINGMOUSE, acts as a dropper for components related to ANEL and ultimately launches the backdoor, while simultaneously incorporating evasion techniques that hide it from security programs and make detection challenging.
One of the modules deployed via the dropper is ANELLDR, a loader that’s designed to execute ANEL in memory. It’s launched using a known method called DLL side-loading, after which it decrypts and runs the final-stage backdoor.
A 32-bit HTTP-based implant, ANEL was actively developed between 2017 and 2018 as a way to capture screenshots, upload/download files, load executables, and run commands via cmd.exe. The 2024 campaign employs an updated version that introduces a new command to run a specified program with elevated privileges.
Furthermore, the attack chains leverage the backdoor to collect information from the infected environments and selectively deploy NOOPDOOR against targets of special interest.
“Many of the targets are individuals, such as researchers, who may have different levels of security measures in place compared to enterprise organizations, making these attacks more difficult to detect,” Hiroaki said. “It is essential to maintain basic countermeasures, such as avoiding opening files attached to suspicious emails.”