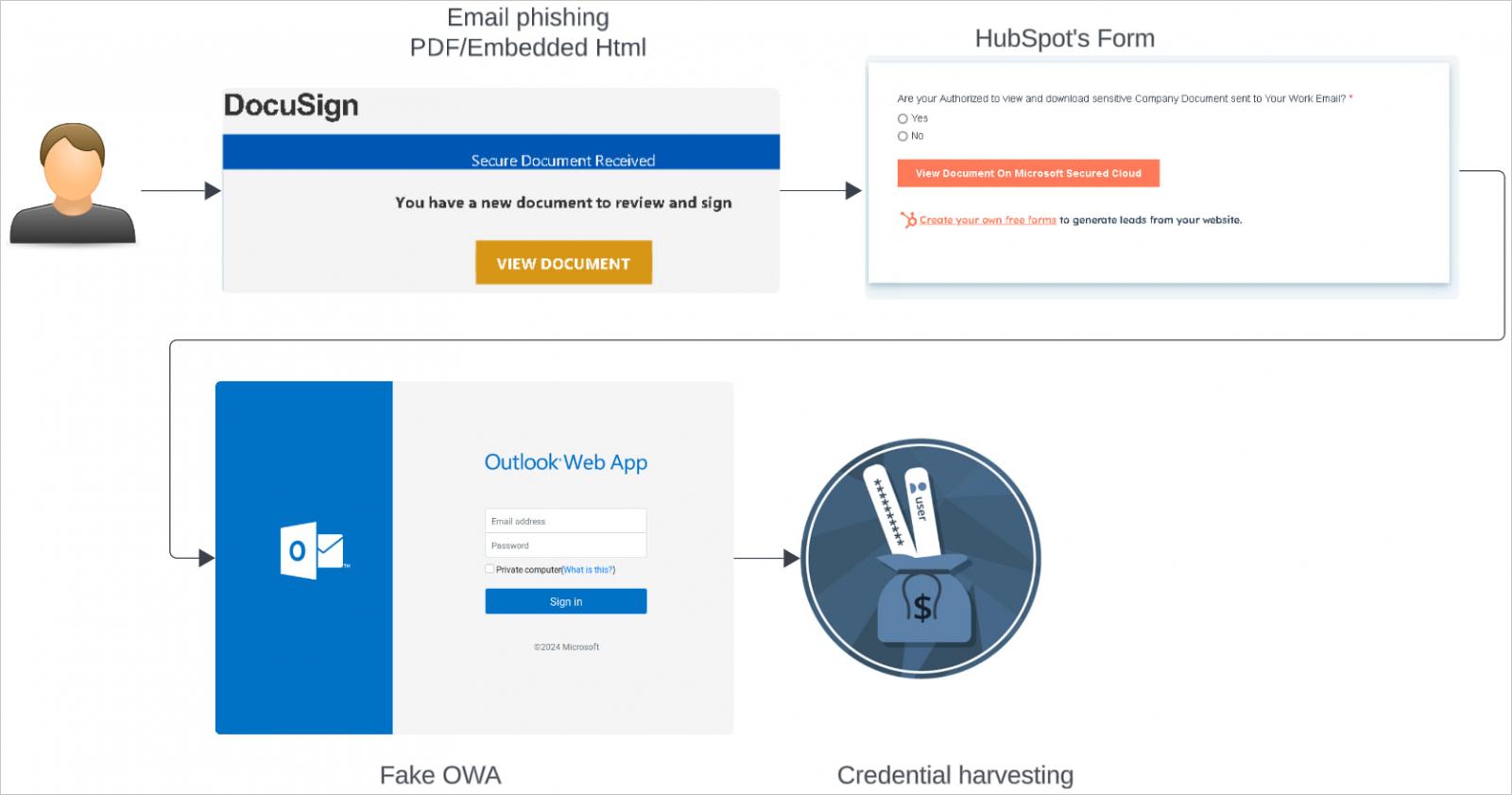
A phishing campaign targeting automotive, chemical, and industrial manufacturing companies in Germany and the UK is abusing HubSpot to steal Microsoft Azure account credentials.
The threat actors use HubSpot Free Form Builder links and DocuSign-mimicking PDFs to redirect victims to credential-harvesting pages.
According to Palo Alto Networks’ Unit 42 team of researchers, the campaign, which started in June 2024 and remained active until at least September 2024, has compromised approximately 20,000 accounts.
“Our telemetry indicates the threat actor successfully targeted roughly 20,000 users across various European companies,” explains the Palo Alto Unit 42 report.
HubSpot used for credential harvesting
HubSpot is a legitimate customer relationship management (CRM) platform used in marketing automation, sales, customer service, analytics, and building websites and landing pages.
The Form Builder is a feature that allows users to create custom online forms to capture information from website visitors.
In the phishing campaign Unit 42 tracked, threat actors exploited HubSpot Form Builder to create at least seventeen deceptive forms to lure victims into providing sensitive credentials in the next step.
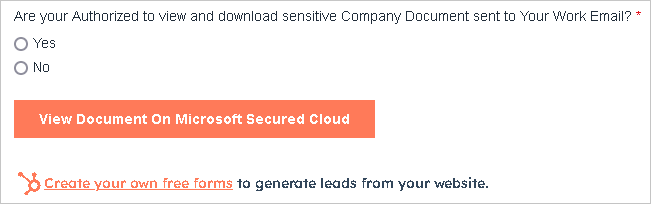
Source: Unit 42
Although the HubSpot infrastructure itself wasn’t compromised, it was used as an intermediate step to lead victims to attacker-controlled sites on ‘.buzz’ domains mimicking Microsoft Outlook Web App and Azure login pages.
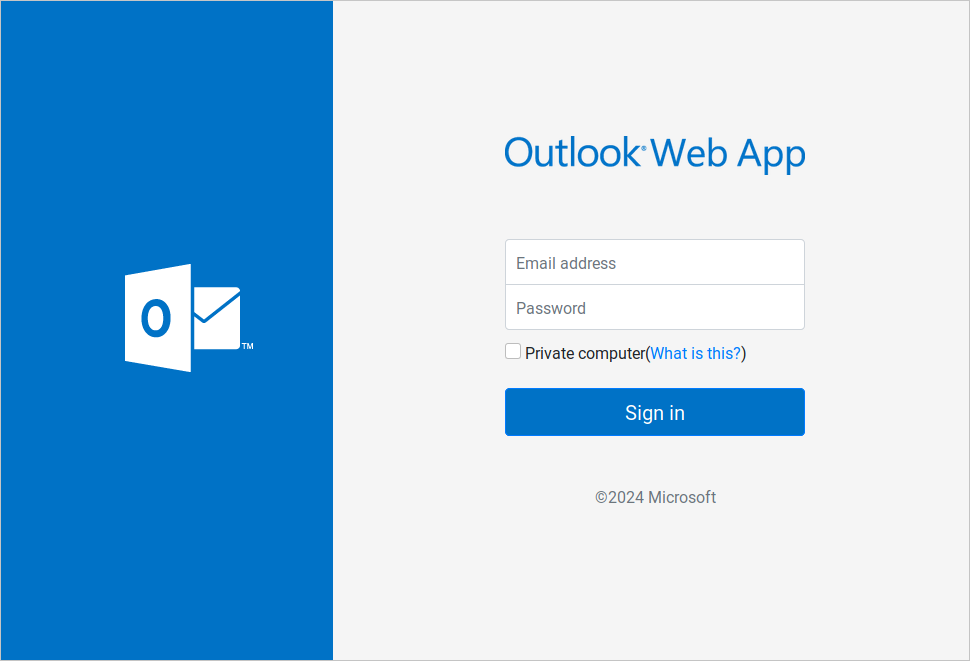
Source: Unit 42
Web pages mimicking DocuSign’s document management system, French notary offices, and organization-specific login portals were also used in the attacks.
Victims were directed to those pages by DocuSign-branded phishing messages containing links to HubSpot, either on an attached PDF or embedded HTML.
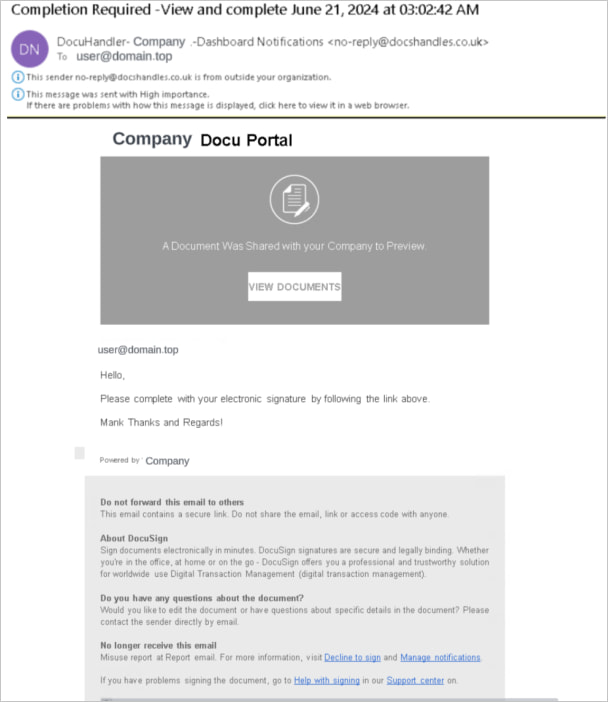
Source: Unit 42
As the emails contain links to a legitimate service (HubSpot), they are not typically flagged by email security tools, so they’re more likely to reach target inboxes.
However, the phishing emails associated with this campaign failed Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC) checks.
Source: Unit 42
Post-compromise activity
In cases of successful attacks seen by the researchers, the threat actors used VPNs to make it appear as if they were based on the country of the victimized organization.
“When IT regained control of the account, the attacker immediately initiated a password reset, attempting to regain control,” describe the Unit 42 researchers.
“This created a tug-of-war scenario in which both parties struggled for control over the account.”
Unit 42 also identified a novel Autonomous System Number (ASN) used in the campaign, which can be used for threat identification along with specific, unusual user-agent strings.
Although most of the servers that acted as the backbone of the phishing campaign have long gone offline, the activity is yet another example of legitimate service abuse, as threat actors constantly explore new avenues to bypass security tools.



