Hackers are using a fake Android app named ‘SafeChat’ to infect devices with spyware malware that steals call logs, texts, and GPS locations from phones.
The Android spyware is suspected to be a variant of “Coverlm,” which steals data from communication apps such as Telegram, Signal, WhatsApp, Viber, and Facebook Messenger.
CYFIRMA researchers say the Indian APT hacking group ‘Bahamut’ is behind the campaign, with their latest attacks conducted mainly through spear phishing messages on WhatsApp that send the malicious payloads directly to the victim.
Also, the CYFIRMA’s analysts highlight several TTP similarities to another Indian state-sponsored threat group, the ‘DoNot APT’ (APT-C-35), that has previously infested Google Play with fake chat apps acting as spyware.
Late last year, ESET reported that the Bahamut group was using fake VPN apps for the Android platform that included extensive spyware functions.
In the latest campaign observed by CYFIRMA, Bahamut targets individuals in South Asia.
“Safe Chat” details
While CYFIRMA doesn’t delve into the specifics of the social engineering aspect of the attack, it’s common for victims to be persuaded into installing a chat app under the pretext of transitioning the conversation to a more secure platform.
The analysts report that Safe Chat features a deceiving interface that makes it appear as a real chat app and also takes the victim through a seemingly legitimate user registration process that adds credibility and serves as an excellent cover for the spyware.
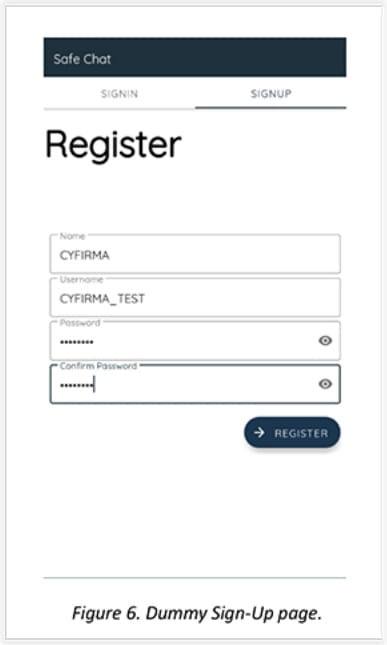
One critical step in the infection is the acquisition of permissions to use the Accessibility Services, which are subsequently abused to automatically grant the spyware more permissions.
These additional permissions enable the spyware to access to the victim’s contacts list, SMS, call logs, external device storage, and fetch precise GPS location data from the infected device.
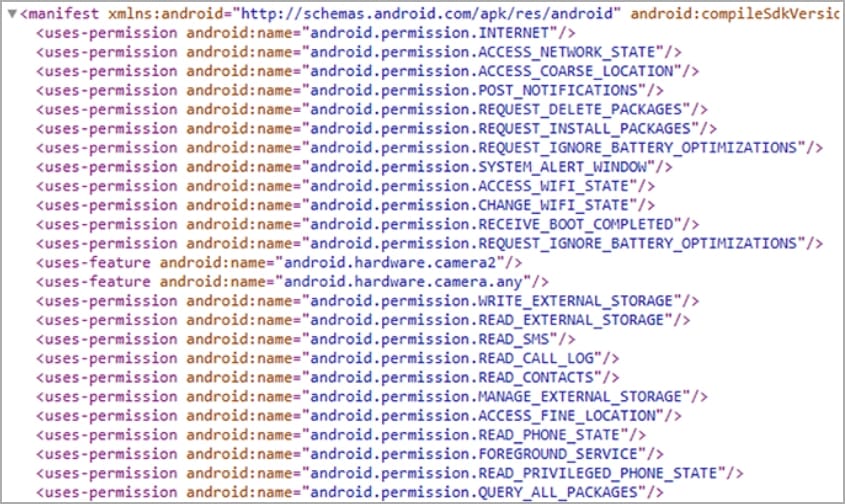
The app also requests the user to approve exclusion from Android’s battery optimization subsystem, which terminates background processes when the user isn’t actively engaging with the app.
“Another snippet from the Android Manifest file shows that the threat actor designed the app to interact with other already installed chat applications,” explains CYFIRMA.
“The interaction will take place using intents, OPEN_DOCUMENT_TREE permission will select specific directories and access apps mentioned in intent.”

A dedicated data exfiltration module transfers information from the device to the attacker’s C2 server through port 2053.
The stolen data is encrypted using another module that supports RSA, ECB, and OAEPPadding. At the same time, the attackers also use a “letsencrypt” certificate to evade any network data interception efforts against them.
CYFIRMA concludes the report by saying that it holds enough evidence to link Bahamut to working on behalf of a specific state government in India.
Also, using the same certificate authority as the DoNot APT group, similar data stealing methodologies, common targeting scope, and the use of Android apps to infect targets all indicate overlap or close collaboration between the two groups.
Update 8/4 – A Google spokesperson has sent BleepingComputer the following comment:
Users are protected by Google Play Protect, which can warn users of identified malicious apps on Android devices.



