New Glove Stealer malware can bypass Google Chrome’s Application-Bound (App-Bound) encryption to steal browser cookies.
As Gen Digital security researchers who first spotted it while investigating a recent phishing campaign said, this information-stealing malware is “relatively simple and contains minimal obfuscation or protection mechanisms,” indicating that it’s very likely in its early development stages.
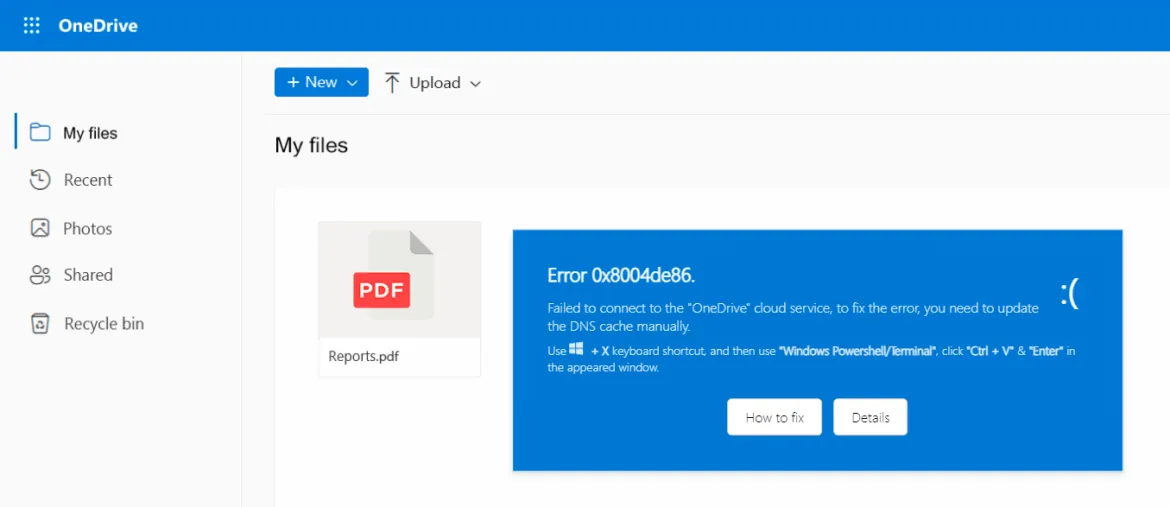
During their attacks, the threat actors used social engineering tactics similar to those used in the ClickFix infection chain, where potential victims get tricked into installing malware using fake error windows displayed within HTML files attached to the phishing emails.
The Glove Stealer .NET malware can extract and exfiltrate cookies from Firefox and Chromium-based browsers (e.g., Chrome, Edge, Brave, Yandex, Opera).
It’s also capable of stealing cryptocurrency wallets from browser extensions, 2FA session tokens from Google, Microsoft, Aegis, and LastPass authenticator apps, password data from Bitwarden, LastPass, and KeePass, as well as emails from mail clients like Thunderbird.
“Other than stealing private data from browsers, it also tries to exfiltrate sensitive information from a list of 280 browser extensions and more than 80 locally installed applications,” said malware researcher Jan Rubín.
“These extensions and applications typically involve cryptocurrency wallets, 2FA authenticators, password managers, email clients and others.”
Basic App-Bound encryption bypass capabilities
To steal credentials from Chromium web browsers, Glove Stealer bypasses Google’s App-Bound encryption cookie-theft defenses, which were introduced by Chrome 127 in July.
To do that, it follows the method described by security researcher Alexander Hagenah last month, using a supporting module that uses Chrome’s own COM-based IElevator Windows service (running with SYSTEM privileges) to decrypt and retrieve App-Bound encrypted keys.
It’s important to note that the malware first needs to get local admin privileges on the compromised systems to place this module in Google Chrome’s Program Files directory and use it to retrieve encrypted keys.
However, although impressive on paper, this still points to Glove Stealer being in early development since it’s a basic method that most other info stealers have already surpassed to steal cookies from all Google Chrome versions, as researcher g0njxa told BleepingComputer in October.
Malware analyst Russian Panda previously said to BleepingComputer that Hagenah’s method looks similar to early bypass approaches other malware took after Google first implemented Chrome App-Bound encryption.
Multiple infostealer malware operations are now capable of bypassing the new security feature to allow their “customers” to steal and decrypt Google Chrome cookies.
“This code [xaitax’s] requires admin privileges, which shows that we’ve successfully elevated the amount of access required to successfully pull off this type of attack,” Google told BleepingComputer last month.
Unfortunately, even though admin privileges are required to bypass App-Bound encryption, this has yet to put a noticeable dent in the number of ongoing information-stealing malware campaigns.
Attacks have only increased since July when Google first implemented App-Bound encryption, targeting potential victims via vulnerable drivers, zero-day vulnerabilities, malvertising, spearphishing, StackOverflow answers, and fake fixes to GitHub issues.




