A new QBot malware campaign is leveraging hijacked business correspondence to trick unsuspecting victims into installing the malware, new findings from Kaspersky reveal.
The latest activity, which commenced on April 4, 2023, has primarily targeted users in Germany, Argentina, Italy, Algeria, Spain, the U.S., Russia, France, the U.K., and Morocco.
QBot (aka Qakbot or Pinkslipbot) is a banking trojan that’s known to be active since at least 2007. Besides stealing passwords and cookies from web browsers, it doubles up as a backdoor to inject next-stage payloads such as Cobalt Strike or ransomware.
Distributed via phishing campaigns, the malware has seen constant updates during its lifetime that pack in anti-VM, anti-debugging, and anti-sandbox techniques to evade detection. It has also emerged as the most prevalent malware for the month of March 2023, per Check Point.
“Early on, it was distributed through infected websites and pirated software,” Kaspersky researchers said, explaining QBot’s distribution methods. “Now the banker is delivered to potential victims through malware already residing on their computers, social engineering, and spam mailings.”
Email thread hijacking attacks are not new. It occurs when cybercriminals insert themselves into existing business conversations or initiate new conversations based on information previously gleaned by compromised email accounts.
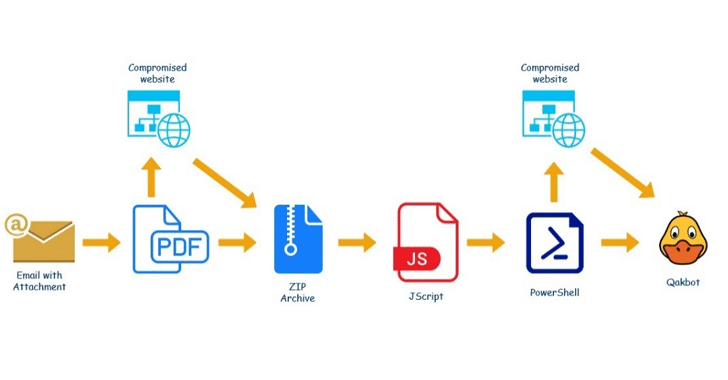
The goal is to entice victims into opening malicious links or malicious attachments, in this case, an enclosed PDF file that masquerades as a Microsoft Office 365 or Microsoft Azure alert.
Opening the document leads to the retrieval of an archive file from an infected website that, in turn, contains an obfuscated Windows Script File (.WSF). The script, for its part, incorporates a PowerShell script that downloads malicious DLL from a remote server. The downloaded DLL is the QBot malware.
The findings come as Elastic Security Labs unearthed a multi-stage social engineering campaign that employs weaponized Microsoft Word documents to distribute Agent Tesla and XWorm by means of a custom .NET-based loader.