Attackers are abusing a Microsoft 365 feature to send payment requests to users, tricking them into logging in to their accounts so attackers can seize control over them.
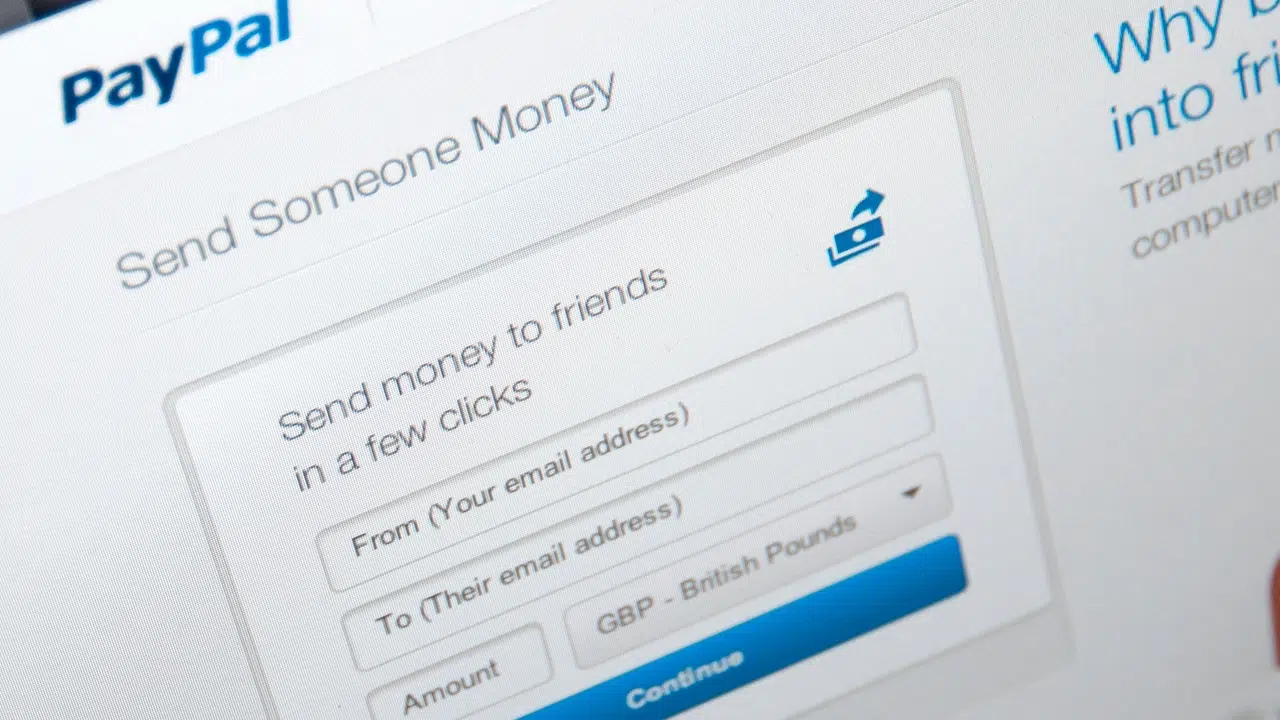
An unconventional phishing campaign convincingly impersonates online payments service PayPal to try to trick users into logging in to their accounts to make a payment; in reality, the login allows attackers to take over an account. The novel part of the attack is the abuse of a legitimate feature within Microsoft 365 to create a test domain, which then allows the attackers to create an email distribution list that makes the payment-request messages appear to be legitimately sent from PayPal.
Carl Windsor, CISO for Fortinet Labs, discovered the campaign when he himself was targeted by it, he revealed in a blog post published today.
Windsor received a request in his inbox from a sender with a nonspoofed PayPal email address seeking a payment of $2,185.96. The person requesting the money was someone called Brian Oistad, and aside from the “to” address not being Windsor’s email address — it was addressed to Billingdepartments1[@]gkjyryfjy876.onmicrosoft.com — there were few obvious signs it was not a genuine email, he said.
“What’s interesting about this attack is that it doesn’t use traditional phishing methods,” Windsor wrote. “The email, the URLs, and everything else are perfectly valid.”
That validity might persuade an average email user to click on the link in the email, which redirects them to a PayPal login page showing a request for payment.
At this point, “some folks might be tempted to log in with their account details, however, this would be extremely dangerous,” he wrote. That’s because the login page links the target’s PayPal account address with the address it was sent to — Billingdepartments1[@]gkjyryfjy876.onmicrosoft.com, controlled by the attacker — not their own email address.
Abusing Microsoft 365 Test Domains for Cybercrime
The campaign works because the scammer appears to have registered a Microsoft 365 test domain — which is free for three months — and then created a distribution list containing target emails. This allows any messages sent from the domain to bypass standard email security checks, Windsor explained in the post.
Then, “on the PayPal Web portal, they simply request the money and add the distribution list as the address,” he wrote.
This money request is then distributed to the targeted victims, and the Microsoft 365 Sender Rewrite Scheme (SRS) rewrites the sender to, for example, “bounces+SRS=onDJv=S6[@]5ln7g7.onmicrosoft.com, which will pass the SPF/DKIM/DMARC check,” Windsor added.
“Once the panicking victim logs in to see what is going on, the scammer’s account (Billingdepartments1[@]gkjyryfjy876.onmicrosoft.com) gets linked to the victim’s account,” he wrote. “The scammer can then take control of the victim’s PayPal account — a neat trick … [that] would sneak past even PayPal’s own phishing check instructions.”
Indeed, abusing a vendor feature to deliver the phishing message does give the attackers a stealthy advantage when it comes to bypassing typical email security, a security expert notes.
“The emails are sent from a verified source and follow an identical template to legitimate messages, such as a standard PayPal payment request,” says Elad Luz, head of research at Oasis Security, a provider of non-human identity management. “This makes them difficult for mailbox providers to distinguish from genuine communications.”
Cyber Defense: Create a “Human Firewall” Against Phishing
Because the attack appears to be a genuine email, the best solution to avoid falling prey to it is what Windsor calls the “human firewall,” or “someone who has been trained to be aware and cautious of any unsolicited email, regardless of how genuine it may look,” he wrote in the post.
“This, of course, highlights the need to ensure your workforce is receiving the training they need to spot threats like this to keep themselves — and your organization — safe,” Windsor noted.
It is also possible to create a rule within email security scanners to “look for multiple conditions that indicate that this email is being sent via a distribution list,” to help detect a campaign that uses this vector, he added.
Another potential mitigation is to use artificial intelligence (AI)-based security tools that use neural networks to analyze social graph patterns, among other techniques, “to help spot these hidden interactions by analyzing user behaviors more deeply than static filters,” Stephen Kowski, field chief technology officer (CTO) at SlashNext Email Security+, tells Dark Reading.
“That kind of proactive detection engine recognizes unusual group messaging patterns or requests that slip through basic checks,” he says. “A thorough inspection of user interaction metadata will catch even this sneaky approach.”