A new UEFI Secure Boot bypass vulnerability tracked as CVE-2024-7344 that affects a Microsoft-signed application could be exploited to deploy bootkits even if Secure Boot protection is active.
The vulnerable UEFI application is present in multiple real-time system recovery tools from several third-party software developers.
Bootkits represent a critical security threat that is difficult to detect because they take action before the operating system loads, and survive OS re-installs.
Underlying problem
The issue stems from the application using a custom PE loader, which allows loading any UEFI binary, even if they are not signed.
Specifically, the vulnerable UEFI application does not rely on trusted services like ‘LoadImage’ and ‘StartImage’ that validate binaries against a trust database (db) and a revocation database (dbx).
In this context, ‘reloader.efi’ manually decrypts and loads into memory binaries from ‘cloak.dat’, which contains a rudimentary encrypted XOR PE image.
This unsafe process could be exploited by an attacker by replacing the app’s default OS bootloader on the EFI partition with a vulnerable ‘reloader.efi’ and planting a malicious ‘cloak.dat’ file on its nominal paths.
Upon system boot, the custom loader will decrypt and execute the malicious binary without Secure Boot validation.
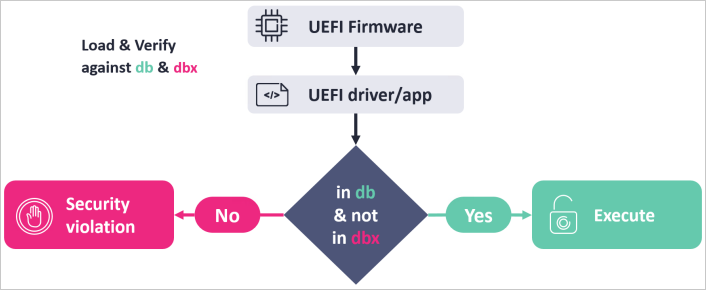
Source: ESET
Scope of impact
The vulnerability affects UEFI applications designed to assist in system recovery, disk maintenance, or backups and are not general-purpose UEFI applications.
ESET’s report lists the following products and versions as vulnerable:
- Howyar SysReturn before version 10.2.023_20240919
- Greenware GreenGuard before version 10.2.023-20240927
- Radix SmartRecovery before version 11.2.023-20240927
- Sanfong EZ-back System before version 10.3.024-20241127
- WASAY eRecoveryRX before version 8.4.022-20241127
- CES NeoImpact before version 10.1.024-20241127
- SignalComputer HDD King before version 10.3.021-20241127
It should be noted that attackers could exploit CVE-2024-7344 even if the above applications are not present on the target computer. The hackers could perform the attack by deploying only the vulnerable ‘reloader. efi’ binary from those apps.
However, those using the above apps and impacted versions should move to the newer releases as soon as possible to eliminate the attack surface.
ESET published a video to demonstrate how the vulnerability could be exploited on a system that has Secure Boot enabled
Fixes and mitigations
Microsoft has released a patch for CVE-2024-7344
ESET discovered the vulnerability on July 8, 2024, and reported it to the CERT Coordination Center (CERT/CC) for coordinated disclosure to the impacted parties.
Affected vendors fixed the issue in their products and Microsoft revoked the certificates on January 14th Patch Tuesday update
In the following months, ESET worked with the affected vendors to evaluate the proposed patches and eliminate the security problem.
Eventually, on January 14, 2025, Microsoft revoked the certificates of vulnerable UEFI applications, which should block any attempts to execute their binaries.
This mitigation is automatically applied to users who installed the latest Windows update. ESET also shared PowerShell commands that admins of critical systems can use to manually check if the revocations have been successfully applied.